Hello @Gangi Reddy ,
Thank you for posting here.
We can check all TLS Cipher Suites by running command below.
Get-TlsCipherSuite
OR
Get-TlsCipherSuite >C:\machinename.txt
For example:
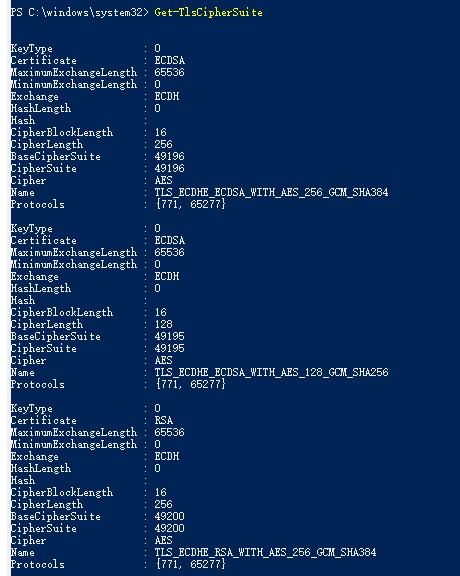
Or you can check DES, 3DES, IDEA or RC2 cipher Suites as below.
Get-TlsCipherSuite -Name "DES"
Get-TlsCipherSuite -Name "3DES"
Get-TlsCipherSuite -Name "IDEA"
Get-TlsCipherSuite -Name "RC2"
For example:

You can disable certain specific ciphers by removing them from HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002
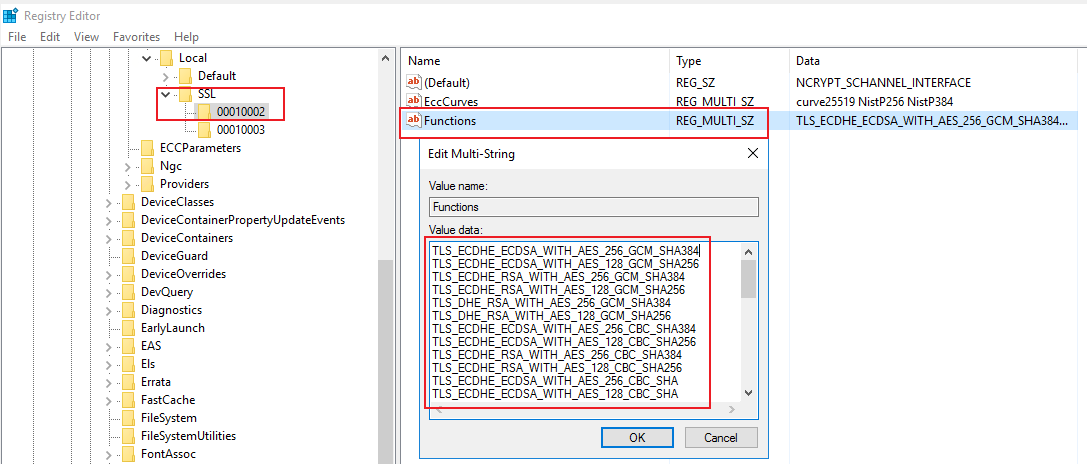
Then restart the machine to see if it helps.
For more information, please refer to the part "Enabling or Disabling additional cipher suites" in the following link.
Managing SSL/TLS Protocols and Cipher Suites for AD FS
https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/operations/manage-ssl-protocols-in-ad-fs
Hope the information above is helpful to you.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
