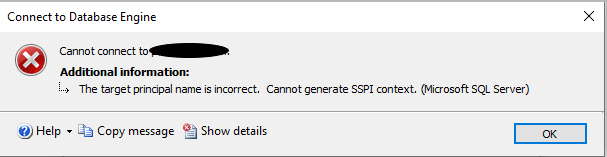
Service Principal Names has to be set on the account where the service is running.
When you have configured your SQL Server running with Local Services, the SPN's were probably on the SQL Server Computer account in Active Directory (this is why it was working)
If you want to configure your SQL Server service to run with a service account (user account in AD or gMSA), the SPN's has to be set on the service account.
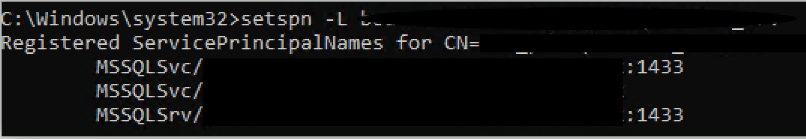
You can run the following command from the SQL Server
setspn -q MSSQLSvc/[SQLServerName]:1433
This should give you the list of the SPN's as well as the AD Account where the SPN's are currently registered (computer account / user account / gMSA).
If you want to configure your SQL Server to run with a service account, you must first remove the SPN's that are registered on the computer account and then register the SPN's to the service account.
Here is the steps.
- Remove SPN from the computer account SQL01.mydomain.local
setspn -D MSSQLSvc/SQL01:1433 SQL01
setspn -D MSSQLSvc/SQL01.mydomain.local:1433 SQL01 - Register the SPN to the service account SVC-SQL01
setspn -S MSSQLSvc/SQL01:1433 mydomain\SVC-SQL01
setspn -S MSSQLSvc/SQL01.mydomain.local:1433 mydomain\SVC-SQL01 - For testing, you may have to purge kerberos tickets from your client computer
From your client computer, open a command prompt and execute the following command: klist purge
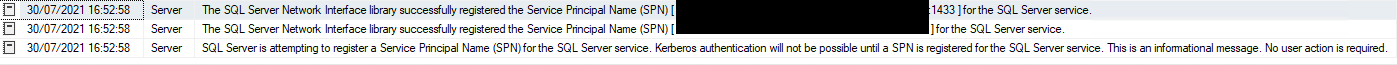
When completed, your client should be able to access your SQL Server using Kerberos Authentication.
For troubleshooting, you can also enable Kerberos logging on your client computer... This can be done using this simple command from an elevated cmd or powershell:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters" /v LogLevel /T REG_DWORD /d 1 /f
This will add Kerberos errors in the System Event Log that may help you debugging.
To stop logging Kerberos errors, just change the value 1 to 0...
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters" /v LogLevel /T REG_DWORD /d 0 /f
hth