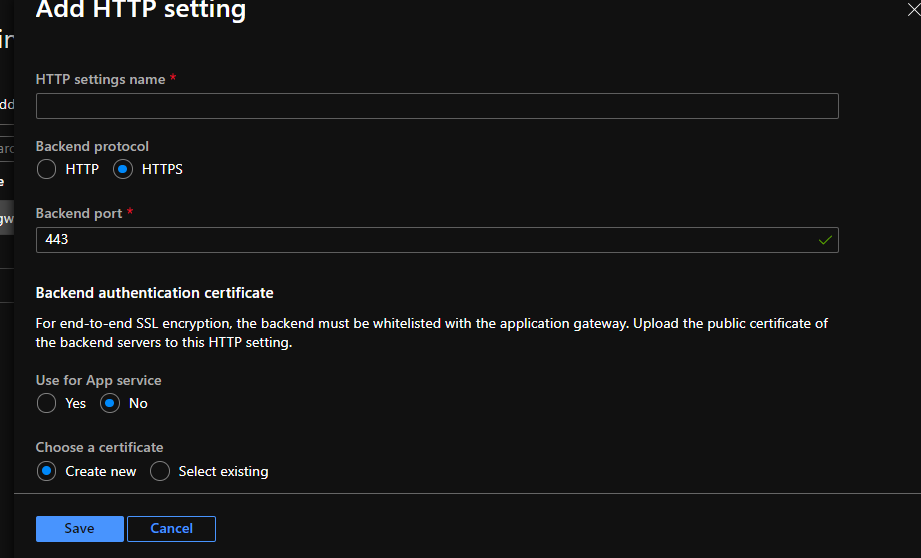
Hello @Aztech-2268 ,
To fix this, bundle the PFX to include the leaf, intermediate, and root cert (in that order) and put on the backend target.
From:
https://learn.microsoft.com/en-us/azure/application-gateway/certificates-for-backend-authentication#export-trusted-root-certificate-for-v2-sku
https://learn.microsoft.com/en-us/azure/application-gateway/application-gateway-backend-health-troubleshooting#trusted-root-certificate-mismatch
For Application gateway V2, a trusted root certificate is required to allow backend instances. The root certificate is a Base-64 encoded X.509(.CER) format root certificate from the backend server certificates. You can export the public key from the TLS/SSL certificate for the backend certificate and then export the root certificate of the trusted CA from the public key in base64 encoded format to get the trusted root certificate. The intermediate certificate(s) should be bundled with server certificate and installed on the backend server.
If the back-end certificate is issued by a well-known certificate authority (CA), you can select the Use Well Known CA Certificate check box, and then you don't have to upload a certificate.
Not having the intermediate bundled in the PFX, can stop the "well known CA" from working correctly.
Try checking the intermediate certs on the backend cert. Here is an online tool for checking SSL certificates.
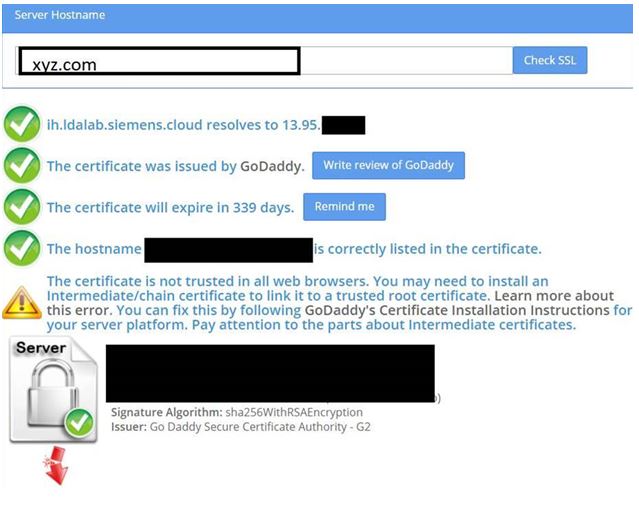
Incorrectly Bundled Cert would show something like the one below:
A Properly Bundled Cert would show something like the one below:
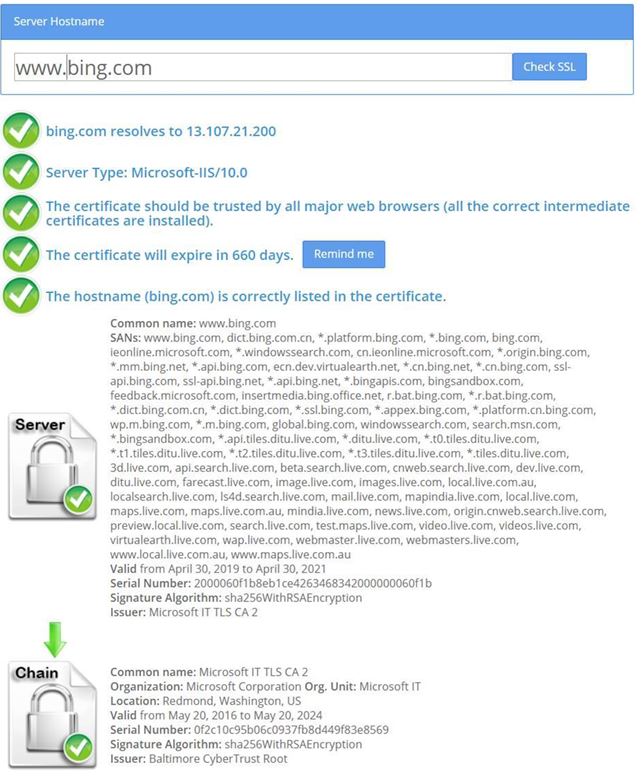
The order should be leaf, intermediate, root.
The rebundled PFX can be put on the appgw listener (renew/replace the one that is there) and then put on the backend as well.
How to rebundle the PFX manually to ensure it's in the right order:
First create a private.key like so from the PFX
openssl pkcs12 -in Certificate.pfx -nocerts -out private.key
Then create a CER Bundle of the entire chain ensuring that they are bundled in the correct order:
Creating a .pem with the Private Key and Entire Trust Chain
https://www.digicert.com/kb/ssl-support/pem-ssl-creation.htm
Then recreate the PFX from the bundled CER and private key from step 1
Create a PFX from the PEM like so:
https://www.ssl.com/how-to/create-a-pfx-p12-certificate-file-using-openssl/
Hope this helps!
Kindly let us know if the above helps or you need further assistance on this issue.
Please don’t forget to "Accept the answer" wherever the information provided helps you, this can be beneficial to other community members.