Hello @Nina Franchaisse ,
Thanks for reaching out.
You can not sent "ImmutableId" element through application claims directly, because this is not supported claim schema entry. Here are list of the Source/ID element pair.
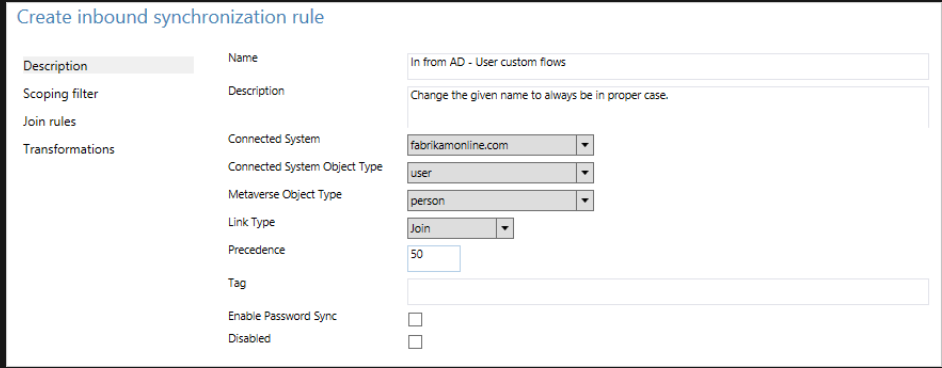
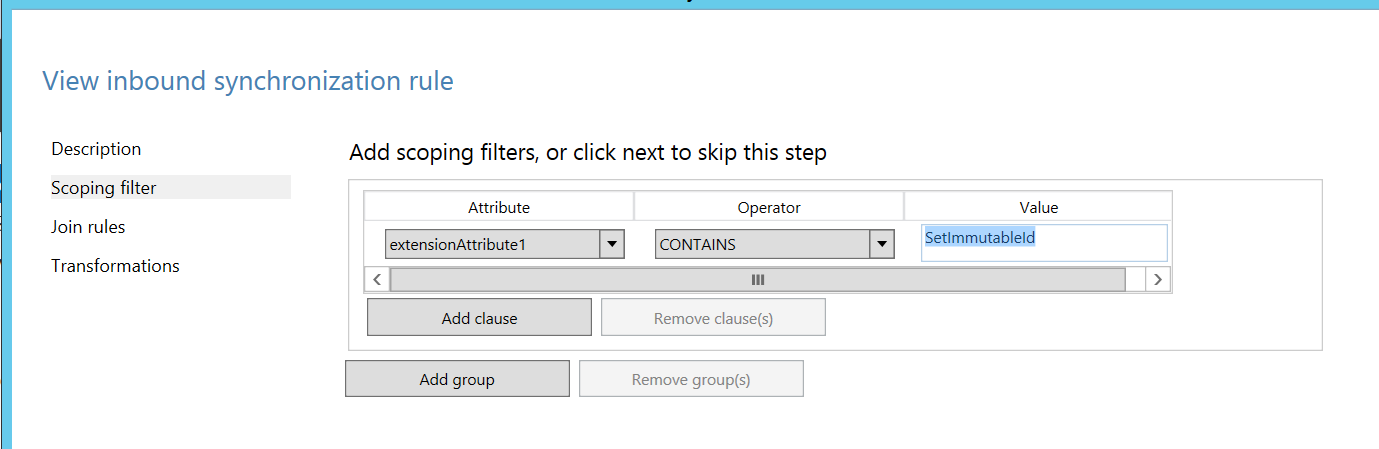
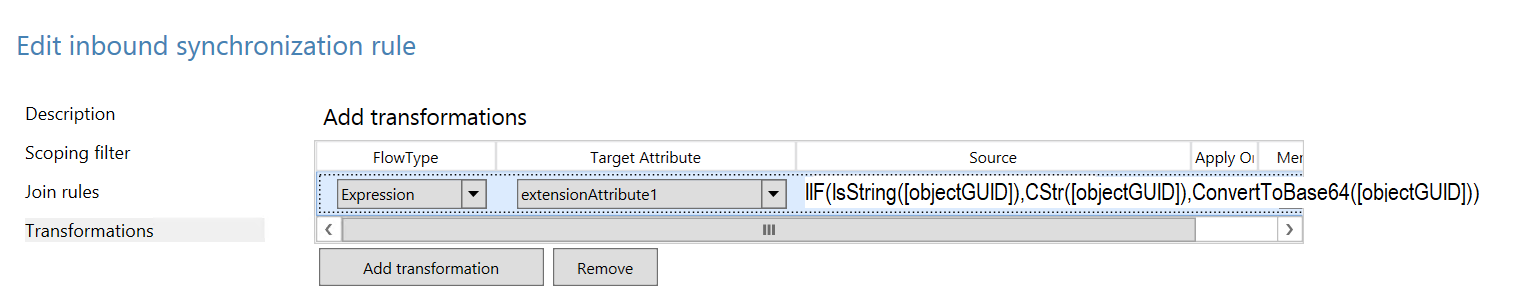
Alternatively, you could leverage anyone of unused "extensionAttribute" copy ImmutableId value manually and sent them in claim as shown below.
Hope this helps.
Example:
Azure AD policy creation:
New-AzureADPolicy -Definition('{"ClaimsMappingPolicy":{"Version":1,"IncludeBasicClaimSet":"true","ClaimsSchema":[{"Source":"user","ID":"extensionAttribute1","SamlClaimType":"http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableId"}]}}') -DisplayName ImmutableId -Type "ClaimsMappingPolicy"
Copy ImmutableId
Set-AzureADUserExtension -ObjectId <User_Object_ID> -ExtensionName extensionattribute1 -ExtensionValue BpazOkLGm0iEtljAONPvOQ==
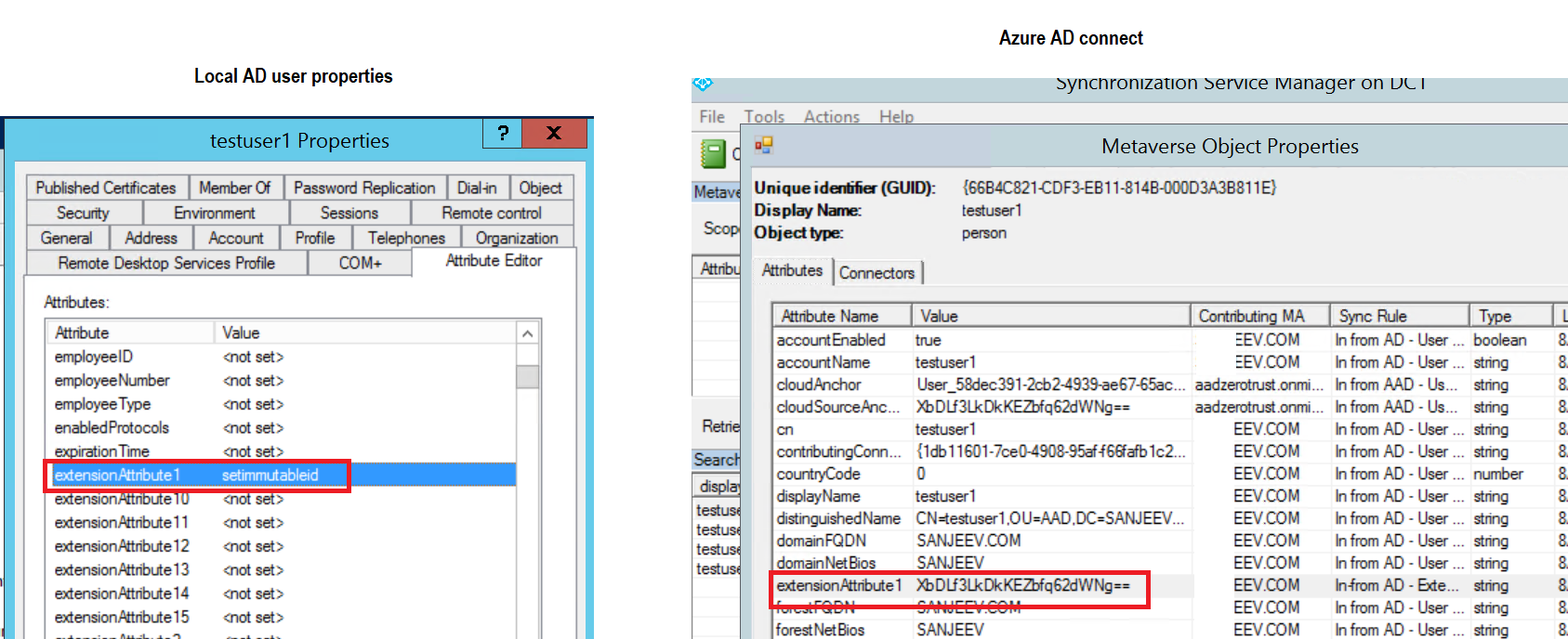
Outcome:
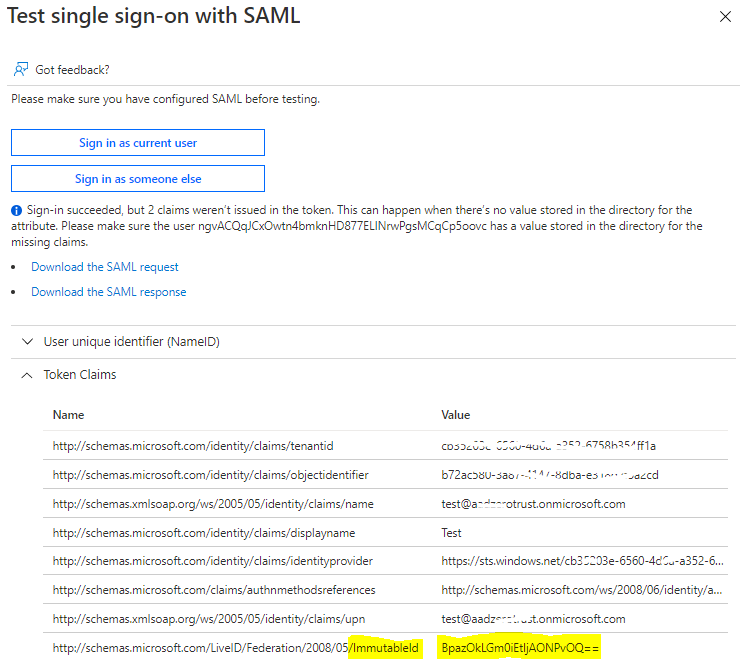
------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.