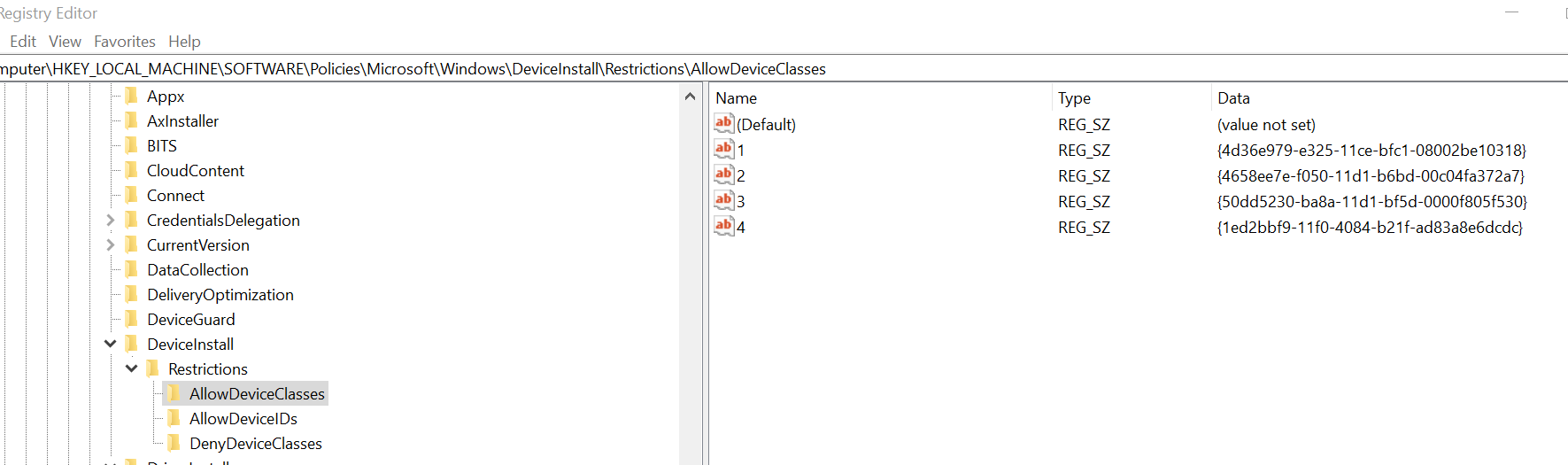
For our personal experience with over 11000 computers environment. Using a method where we don't do change the security enforced by 2021-08 patch (like HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" RestrictDriverInstallationToAdministrators = 1) is random.
If we revise 4 options that Microsoft give:
- Provide administrator username and password when prompted -> This solution is just totally ridicul.
- Include drivers in Windows image / preinstall drivers on the computer -> Work at 60% of the time. Some driver react properly and the are no more prompting to be required at user logon (HP, Ricoh or native driver like Generic Text). But some drivers, even if they are already on the machine, ask to be reinstalled at each opening session time (Minolta and some Ricoh). It very random and trying different/newer drivers not seem to fix it.
- Use SCCM or Endpoint Manager to remotely install printer driver. -> It's exactly the same situation enumerated at point #2. This solution is working RANDOM depending of the driver/printer used.
- Temporarily set RestrictDriverInstallationToAdministrators to 0 and install printer drivers... Again "Temporarily" could be "Permenantly" due to issue where some drivers asking to be reinstalled at each reopenig session.
Finally, the only working solution is to use RestrictDriverInstallationToAdministrators to 0 "permanent". Then add a mitigation where you need to add another strategy to secure which printer servers are allowed.