Hello @EXT Smith Mathilda
The settings you mentioned, control access from public networks, meaning networks not connected to the listed scopes (AMPLSs).
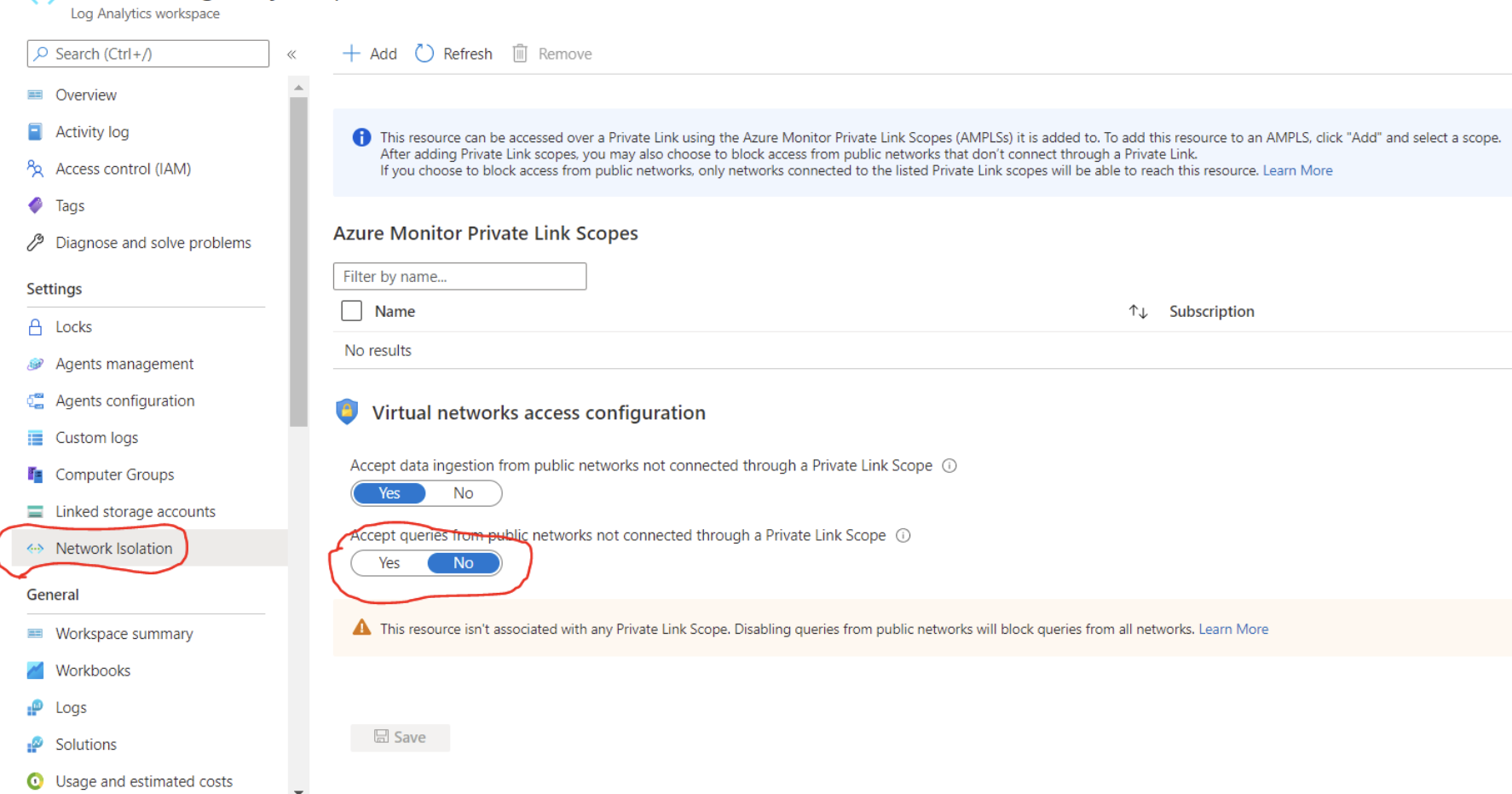
In your resource's menu, there's a menu item called Network Isolation on the left-hand side. This page controls both which networks can reach the resource through a Private Link, and whether other networks can reach it or not.
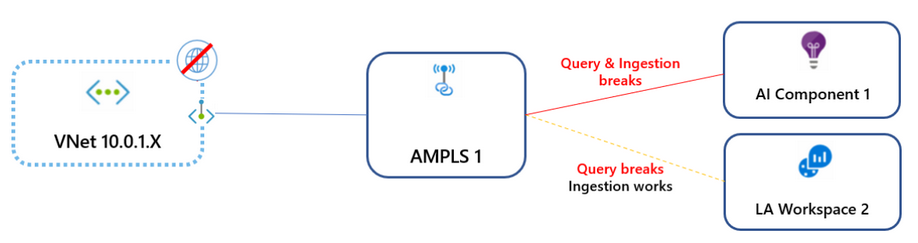
Connecting to scopes (AMPLSs) allows traffic from the virtual network connected to each AMPLS to reach the resource.
The settings on the bottom part of this page control access from public networks, meaning networks not connected to the listed scopes (AMPLSs).
If you set Allow public network access for ingestion to No, then clients (machines, SDKs, etc.) outside of the connected scopes can't upload data or send logs to the resource.
If you set Allow public network access for queries to No, then clients (machines, SDKs etc.) outside of the connected scopes can't query data in the resource. That data includes access to logs, metrics, and the live metrics stream, as well as experiences built on top such as workbooks, dashboards, query API-based client experiences, insights in the Azure portal, and more. Experiences running outside the Azure portal and that query Log Analytics data also have to be running within the private-linked VNET.
****Starting September, 2021, Network Isolation will be strictly enforced. Resources set to block queries from public networks, and that aren't connected to any private network (through an AMPLS) will stop accepting queries from any network.****
https://learn.microsoft.com/en-us/azure/azure-monitor/logs/private-link-configure