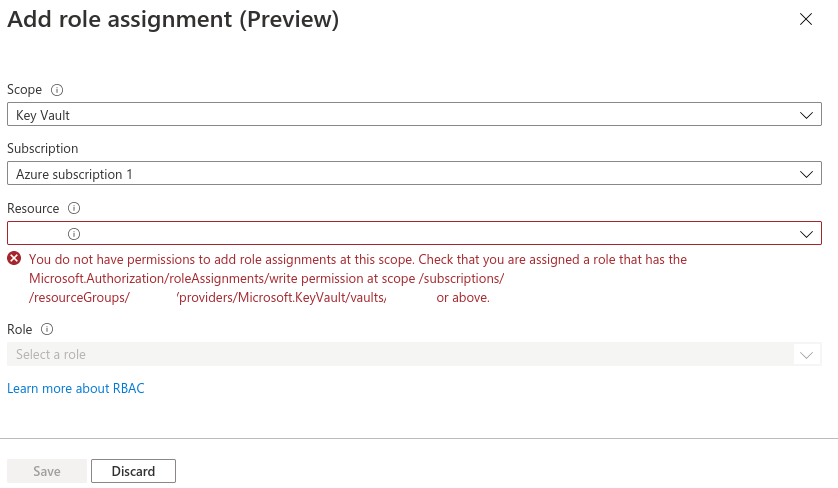
Hello @MT ,
Thanks for reaching out.
Looking at the error, the MI(Managed Identity) doesn't have access to perform the action 'Microsoft.Authorization/roleAssignments/write'. Since the MI(Managed Identity) is assigned with Privileged role administrator, Cloud application administrator, Application administrator which is part of Azure AD roles and these roles are limited within Azure AD directory so instead we need to assign Azure RBAC roles (IAM) to manage Azure resources like Key Vault.
To understand different between Azure AD roles and RBAC roles, refer : https://learn.microsoft.com/en-us/azure/role-based-access-control/rbac-and-directory-admin-roles#how-the-roles-are-related
I would request you to check, the Managed Identity is assigned with a RBAC role (Not Azure AD role) that has the Microsoft.Authorization/roleAssignments/write permission such as Owner or User Access Administrator at the scope you are trying to assign the role.
To resolve the issue, assign the MI(Managed Identity) with Owner/User Access Administrator RBAC role or create a custom role with Microsoft.Authorization/roleAssignments/write permission and assign this role to the Managed Identity.
You can create custom roles using Azure portal, Azure PowerShell, Azure CLI. Below are the steps using Azure CLI:
when you create custom role, you can export any build role Ex: Contributor Role and update it to include roleAssignments/write permission. Below are the steps that you can follow for this purpose:
- Run
Connect-AzAccountcmdlet and sign-in with the subscription owner account. If you don't have Az Module installed, please refer to Install Azure PowerShell. - Run
Get-AzRoleDefinition contributor | ConvertTo-Json > c:\temp\rbac.jsonto export the Contributor role to a JSON file. - Open the JSON file in notepad or any other text editor and remove
"Microsoft.Authorization/*/Write",line under NotActions section. - Also update Name, Id, IsCustom, Description and AssignableScopes parameters. Please refer to below sample for your reference: {
"Name": "Custom Contributor",
"Id": "1a200ac6-5a49-4198-9403-0af86342bd35",
"IsCustom": true,
"Description": "Grants full access to manage all resources, allow you to assign roles in Azure RBAC but not delete roles in Azure RBAC manage assignments in Azure Blueprints, or share image galleries.",
"Actions": [
""
],
"NotActions": [
"Microsoft.Authorization//Delete",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete",
"Microsoft.Compute/galleries/share/action"
],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/subscriptions/TYPE_YOUR_SUBSCRIPTION_ID_HERE"
]
} - Run
New-AzRoleDefinition -InputFile "C:\temp\rbac.json"to create Custom RBAC role using the above JSON file. - Run
Get-AzRoleDefinition -Name "custom contributor"cmdlet to view the role.
Note: The new RBAC role might not appear in Azure Portal immediately. To see the new role in Azure Portal immediately, sign out from Azure Portal, close the browser and sign back in.
Finally, assign the Custom Contributor RBAC role to the MI(Managed Identity). You should no longer get above error for role assignments and should return StatusCode=201 (Created).
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.