Hello @Raj D ,
Thanks for the question and using MS Q&A platform.
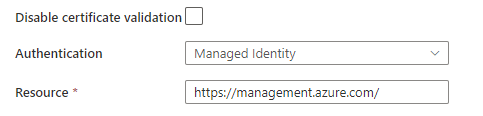
The Managed Identity Authentication eliminates the necessity of generating the Access token
STEP 1
You will have grab the identity of the system assigned ADF or create a user assigned identity.
Add this identity to the resource that you are accessing. For instance if you are accessing the Storage Account from ADF
You will access the IAM of the Storage account and ADF Identity with Appropriate access.
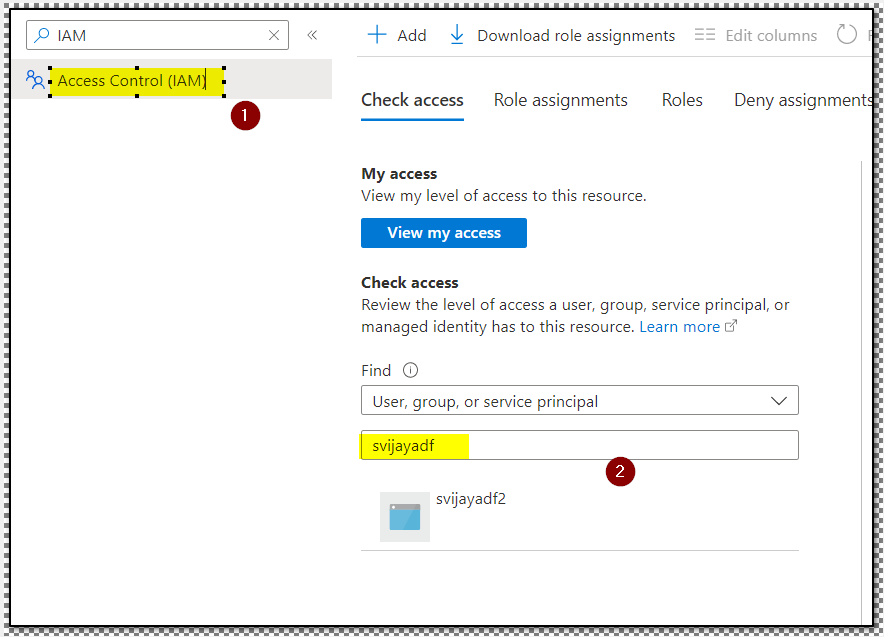
In the above case, sivjayadf2 is the adf instance at my end.
STEP2 :
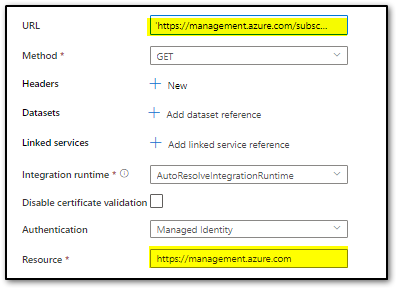
You will use managed Identity if you are accessing the resource through the ADF Identity
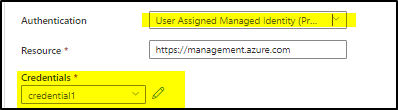
Alternatively, if you are using the user assigned identity, you will have configure the credential.
You could refer this Video here for more information : https://learn.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
Option 2 :
If you want to generate the OAUTH token. You will have issue the request in the below format :
POST /{tenant}/oauth2/v2.0/token HTTP/1.1 //Line breaks for clarity
Host: login.microsoftonline.com
Content-Type: application/x-www-form-urlencoded
client_id=535fb089-9ff3-47b6-9bfb-4f1264799865
&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default
&client_secret=sampleCredentia1s
&grant_type=client_credentials
Here the Client ID and Client Secret service principal.
Hope this will help. Please let us know if any further queries.
------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators