Hi, are there any updates with this case? If not, please select the appropriate response as "Answered." Otherwise please let us know how we can assist you.
SqlThreatDetection_Audit on all Azure SQL Virtual Machines
I recently began seeing failures in my SQL Error logs relating to SQL Audits. We do not utilize SQL Audits in our environment so I began investigating.
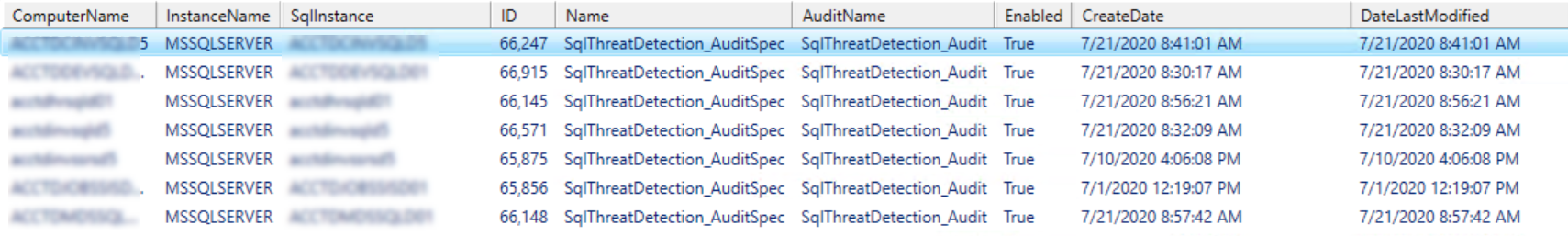
I found that an audit named SqlThreatDetection_Audit was created and enabled on all of my IAAS SQL Servers. This is not a behavior I was expecting and I am trying to find the source of this change.
Starting on 07/01/2020 was the firsts creation of the Audit that I find on my servers. It has continued until today as the most recent was added.
And here is the error that started the investigation.
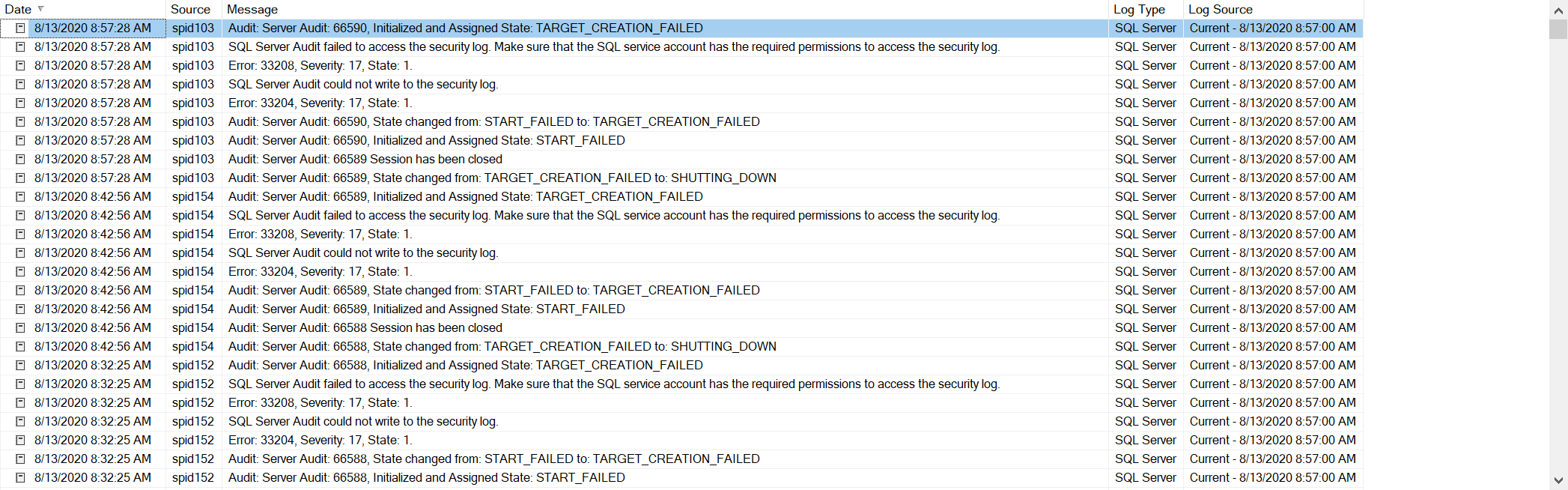
My research shows this might be related to something in Azure Security Center. However, no one in our Security, Networking or Infrastructure team has enabled anything that they feel would impact or cause this Audit to be enabled.
SQL Server on Azure Virtual Machines
Microsoft Security | Microsoft Defender | Microsoft Defender for Cloud

SQL Server | Other
7 answers
Sort by: Most helpful
-
-
Abimbola Adeniran 86 Reputation points
2024-01-19T22:38:41.66+00:00 Hello all, I need some help. I am seeing this issue for “SqlThreatDetection_Audit” SQL Server audit on SQL Server instances running SQL Server 2016 and older (2014,2012 etc) in my client environment. They didn’t use to have these issues before until servers rebooted a few days ago and I have tried all the steps highlighted in the main thread and comments from Cris above. The service account is an AD account and I have confirmed it’s an admin on the server with perms on the security fold in windows registry, the key flag changed to 1, Local security policy changed to grant audit access to the service account and allowing success/failure auditing. I have also granted sysadmin to the service account as a server principal on SQL server with the required server level and database level perms. Not sure what else is required here. Please help urgently.