@sns ,
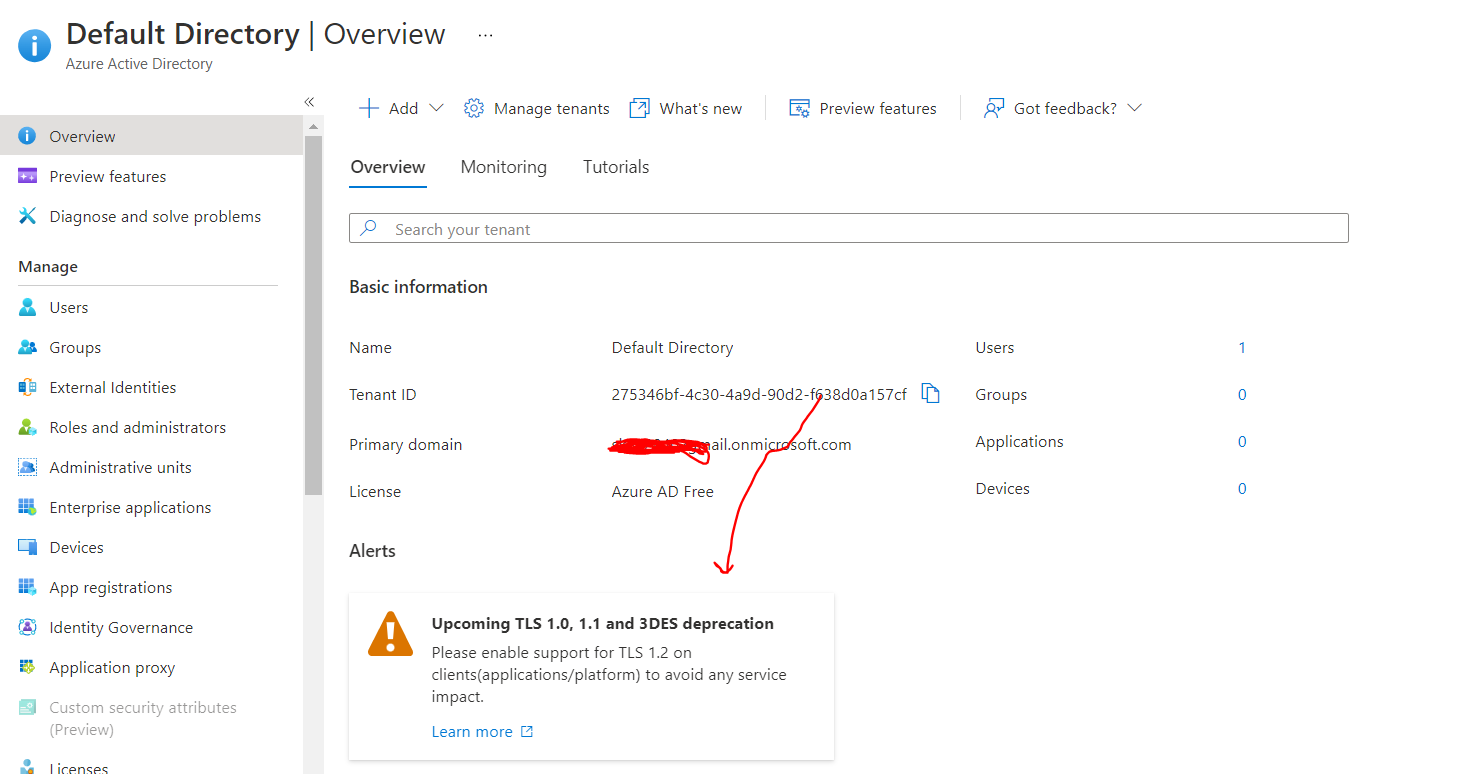
In order to use at least TLS1.2 all the users in your organization should only use devices which are enabled only for TLS1.2 and above for creating any encrypted connection . Any connection that originates from your origination for any application in azure goes to an encrypted tunnel by default. TLS 1.0 and TLS 1.1 are two of the protocol specifications on the basis of which the operating systems of devices create secure communication tunnel between the device and any other endpoint (in this case apps on azure) . During any Secure connection the most secure protocol supported on both client and server side is used to establish a secure tunnel . At this point most of the secure TLS connections to azure use either TLS1.0 or above depending upon if client machine accessing azure supports it too . We are making this change to improve security for our users and be in compliance with latest FedRAMP regulations.
The following application may face connection issues if the servers/machines they are being run on do not have settings changed to support only TLS1.2 . If your application authenticates against azure active directory , you may see issues if you access from any machine which does not support TLS1.2 protocol for communication.
- Azure AD Connect
- Azure AD PowerShell
- Azure AD Application Proxy connectors
- PTA agents
- Legacy browsers
- Applications that are integrated with Azure AD
Make sure all your client machines and servers Operating systems have TLS1.2 and modern cipher suites support enabled . Please use the following to enable the same on client or server operating systems (Windows) .
Please update the following registry strings on the machines using registry editor (Regedit.exe) tool.
Make sure that the following registry DWORD values are configured for these subkeys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client
"DisabledByDefault": 00000000
"Enabled": 00000001
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
"DisabledByDefault": 00000000
"Enabled": 00000001
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
"SchUseStrongCrypto": 00000001
To enable TLS 1.2, use the PowerShell script that's provided in TLS 1.2 enforcement for Azure AD Connect.
As most of the components in this case use .net so it is very important to update .net to the latest version wherever you can and enable strong cryptography on those machines. Please follow the article for enabling TLS1.2 support for .net .
Lastly I would request you to make sure that any network devices in your organization which may create secure tunnel with Azure infrastructure or any site-to-site VPN with Azure must support TLS1.2 so that no connection gets dropped from Azure cloud side. Generally Network devices allow these and do not specifically block these things but in some cases you may have very old devices which may or may not support the settings hence I would request you to check the same. If you do not have any such thing in your on-premise environment then you are good.
I would suggest you to go through the article related to deprecation of older TLS versions. This provides almost all the details related to what changes need to be made and where. Hope this helps. Should you still have any doubts , please feel free to let us know and we will be happy to help you further. If the information in this post is useful , please feel free to accept the post as answer so that it is helpful to other community members.
Thank you
----------------------------------------------------------------------------------------------------------------------------------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators