@mx-oss Thanks for reaching out. You can call the Web Application Firewall Policies - Get API in your logic app to verify if the Policy is already created. If yes then you need to get the customRules parameter from the response of Get API. Initialize the array variable and assign the customRules parameter parse value and then add your new custom rule to this array.
Pass the new array to your Update Policy API.
Workflow:
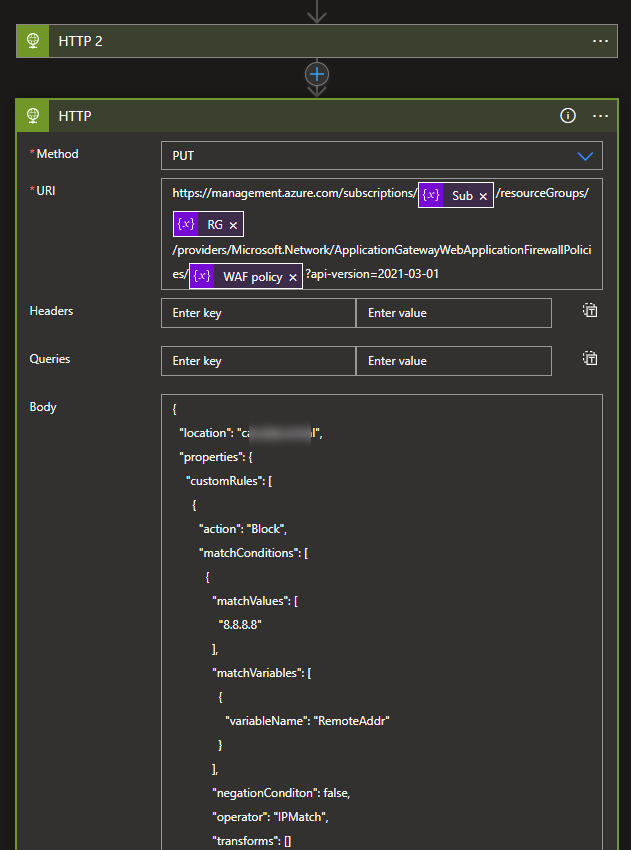
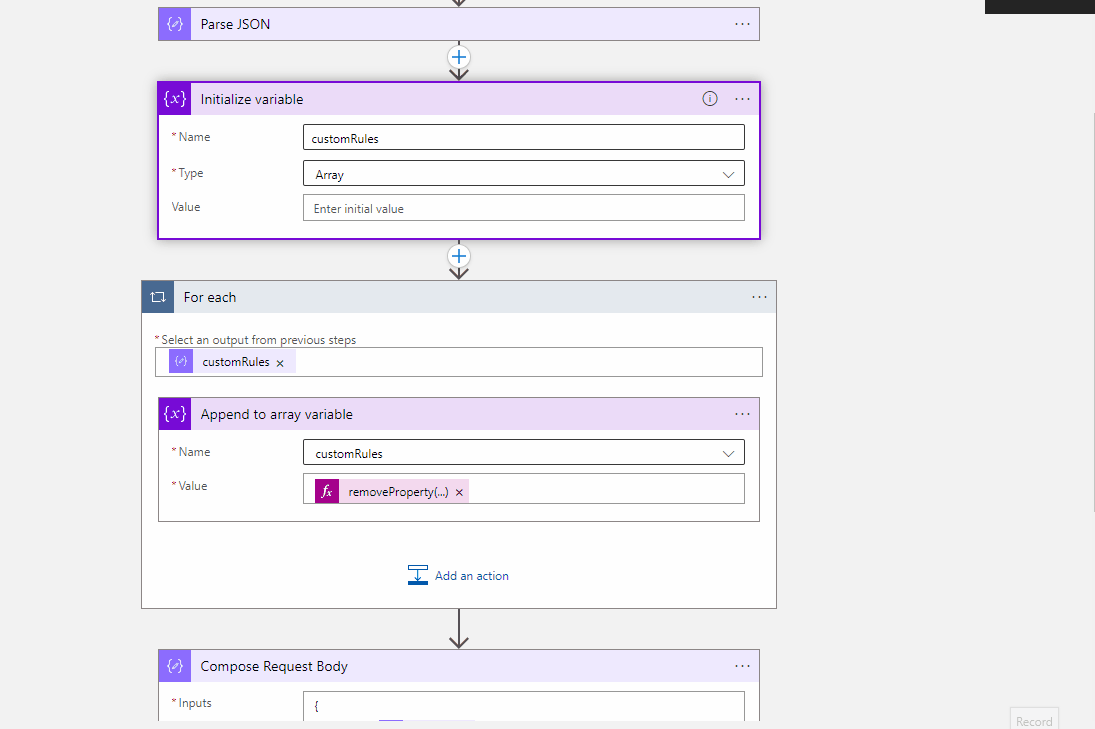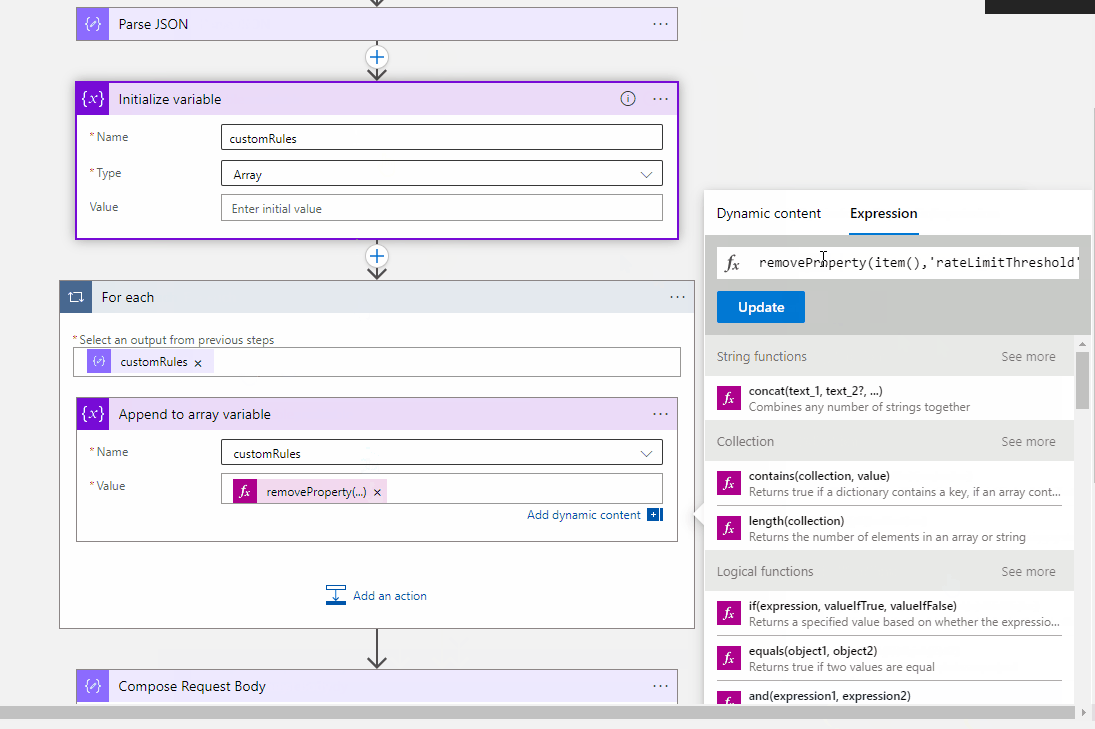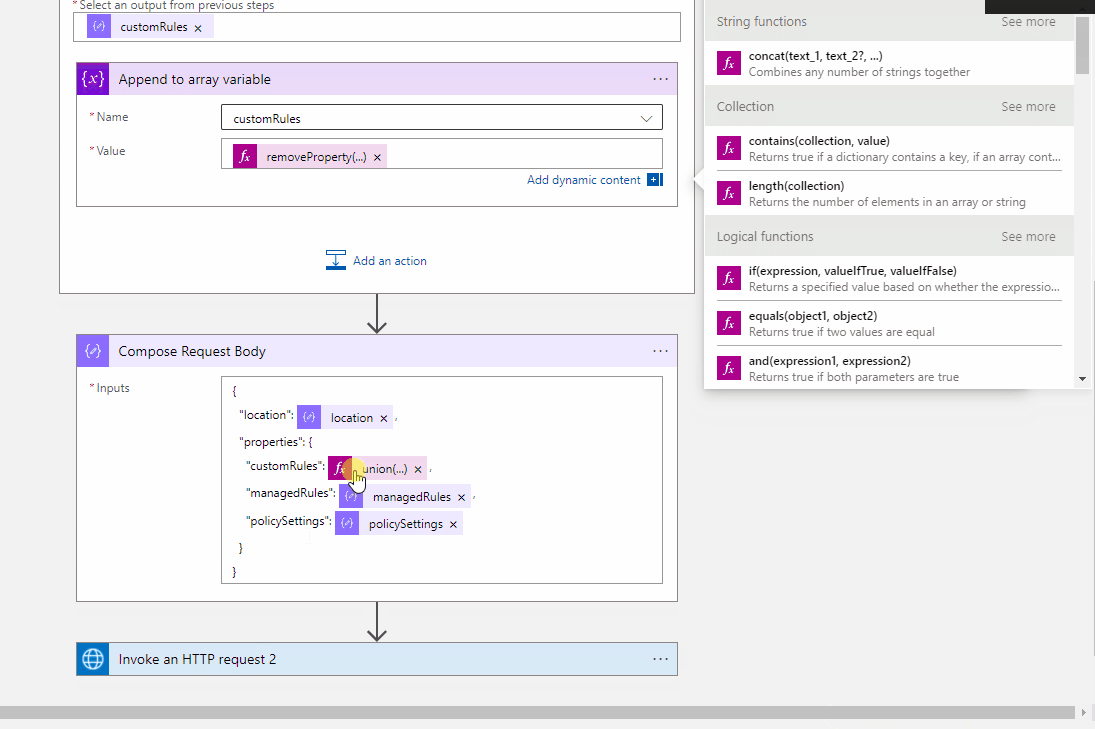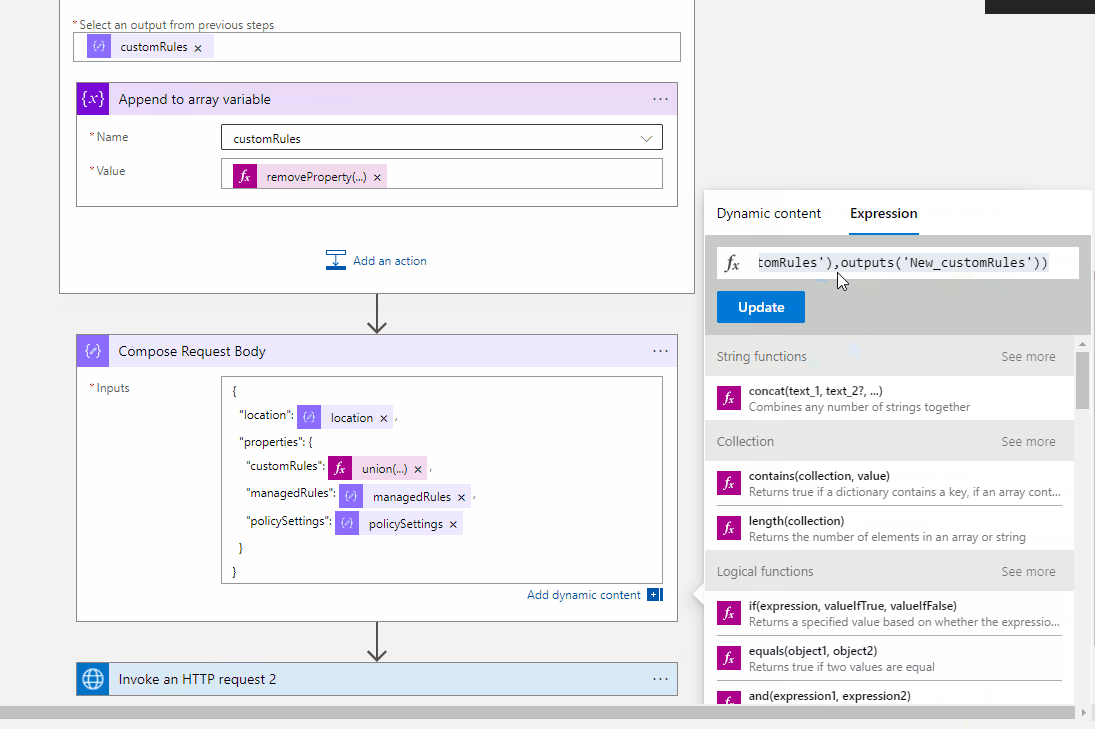
Web Application Firewall Policies Policy --> Parse the Json --> Add new custom role to the array --> Web Application Firewall Policies Create/Update Policy
Note: Please handle the error/exception scenario as per your responses.
Feel free to get back to me if you need any assistance.
Update 1/31:
I have created the test workflow with HTTP trigger and you can refer to the code view of my workflow for your reference.
Workflow:
Http Trigger --> Http with Azure AD (Web Application Firewall Policies Policy) --> Compose Action (to get your input customRules) --> Parse the Json (the output of get call) --> Compose Action (to create the request body for your PUT operation) --> Http with Azure AD (to update the the Web Application Firewall Policies)
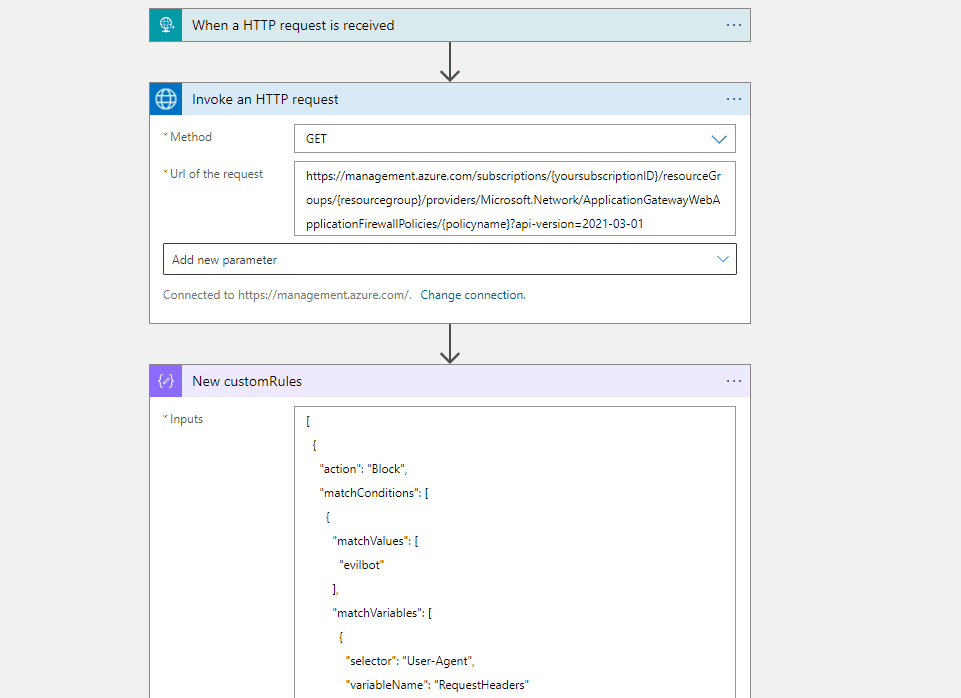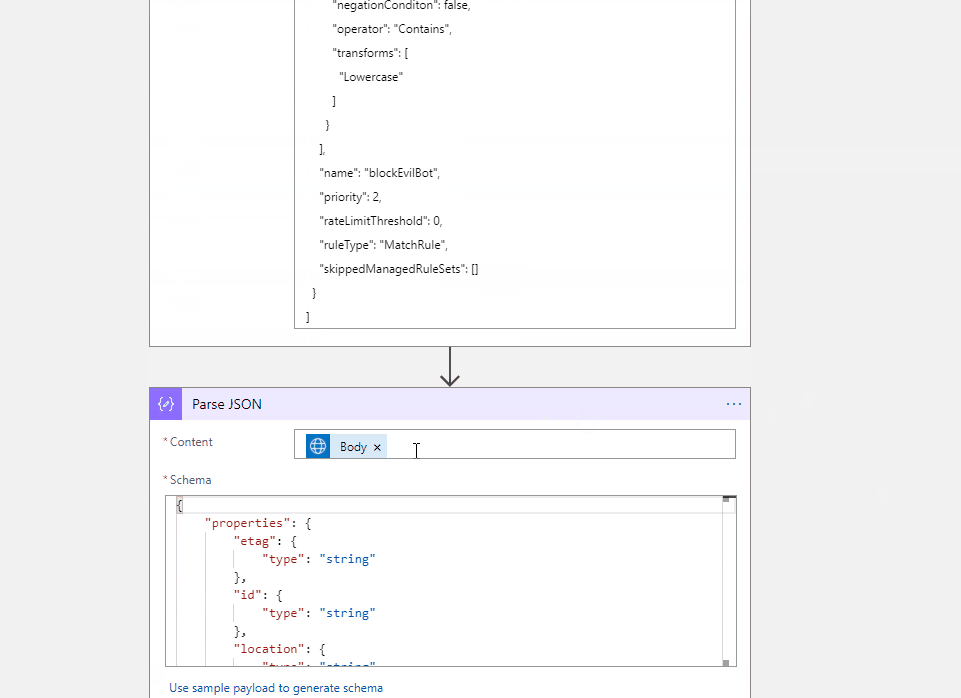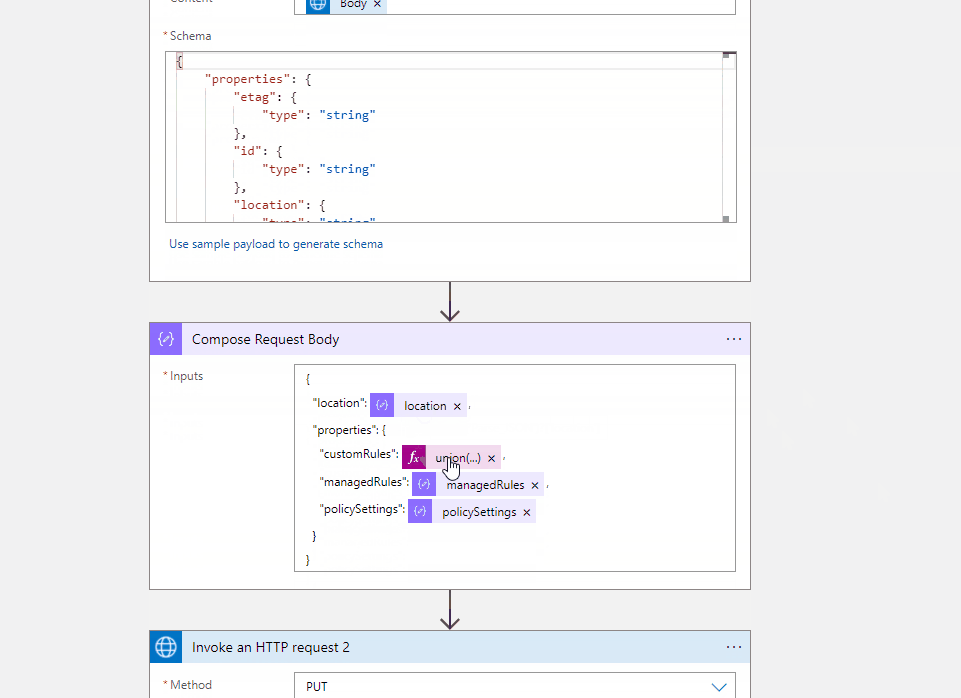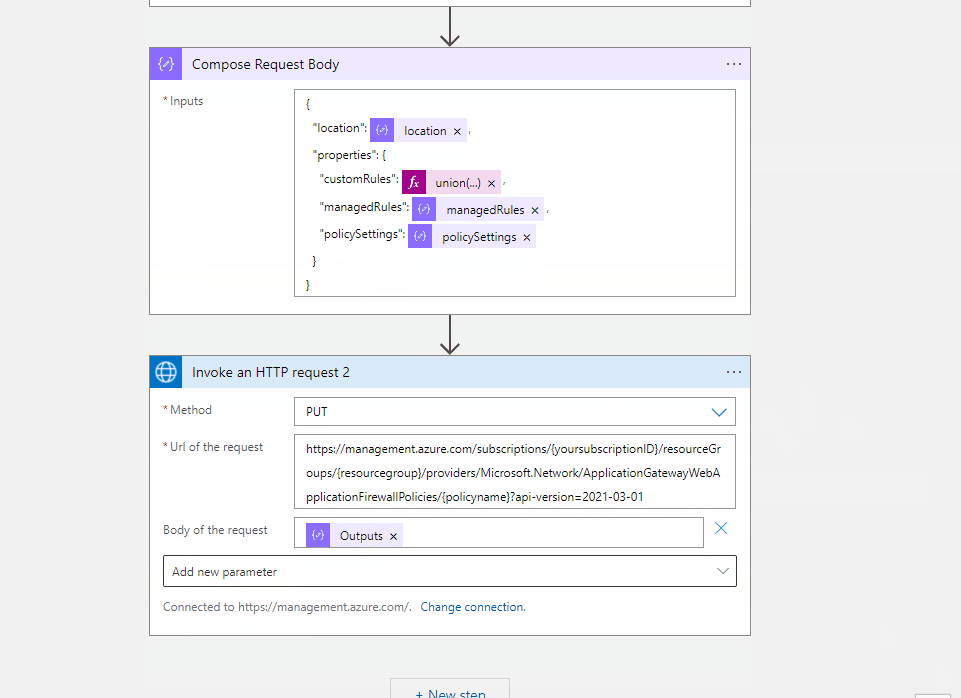
The above is for reference and you can modify the action, add/remove different actions and update the request body as per your requirement.