Hi @David Maryo ,
Thanks for reaching out.
This error usually comes when application/user don’t have permission to access the resource, Key-Vault in this case which is secured by Azure AD tenant. It seems the access policy has not been defined for security principal which can be application or user group to perform different operations on Key Vaults.
To assign an access policy, you need to acquire the object ID of the application, group, or user to which you want to assign the access policy.
Here “Oid” is the claim name for Object Id property which is always immutable and uniquely identify the relevant directory object.
You can retrieve application details from object Id using powershell or using Graph API endpoint https://graph.microsoft.com/v1.0/applications/{ {objectId}}.
Get-AzureADApplication -Filter "ObjectId eq '421599eb-eed7-4988-9b31-02b43a4d37b8'"
Use the Get-AzADServicePrincipal or Get-AzADGroup or Get-AzADUser to get the Service Principal, group or user based on the object Id as below:
Get-AzureADServicePrincipal -ObjectId '13b4b048-c79e-4065-b411-b9570f271a46'
To add the access policy, Navigate to Azure Portal > Key vaults > your_key_vault > Access policies > Add Access Policy.
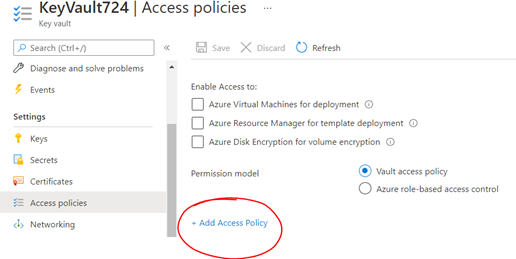
In Access Policy, Select the permissions you want. Also, under Select principal, choose the name of the user, app, or service principal in the search field, select the appropriate result, then choose Select to add and save the access policy.
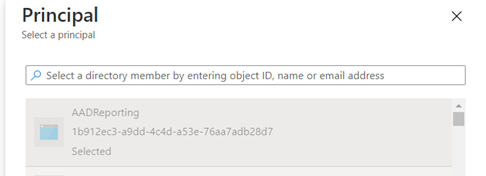
Ref : Assign access policy
Thanks,
Shweta
-----------------------------------
Please remember to "Accept Answer" if answer helped you.