Hi @alma eyre ,
Thanks for reaching out.
As per my understanding, you are trying to authenticate users registered in Azure AD for your application.
To access your application by Azure AD users, your application should also need to register in Azure AD.
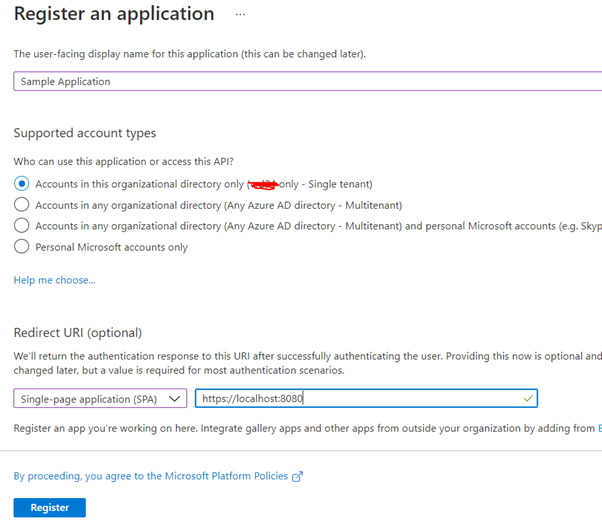
To register the application in Azure Active Directory,
Sign into the Azure portal and select Azure Active Directory in the tenant where you want to register the application.
Under Manage, select App registrations > New registration.
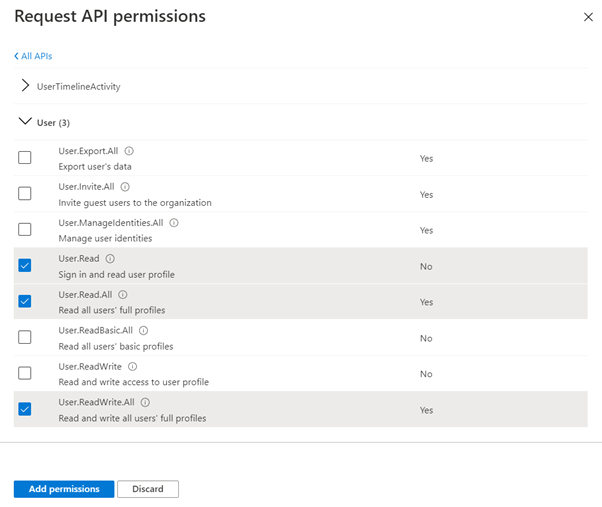
The user or administrator must grant it the correct permissions via a consent process to access the application.
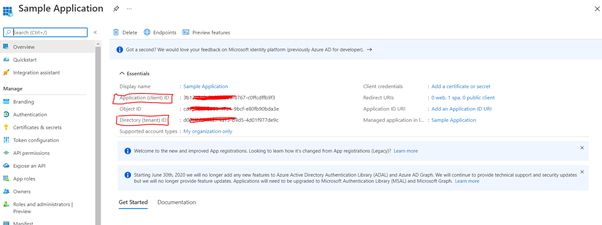
Update the below applicationID, tenantID and redirect URI information in your application as registered in Azure Active Directory.
Once your application is register, you can acquire the access token based on different OAuth flows which is needed to call various resources(Users in your case) or protected API based on your scenario.
Azure Identity TokenCredential provide various flows to obtain an access token based on different scenarios.
InteractiveBrowserCredential is one way to launches the system default browser to interactively authenticate a user and obtain an access token.
Using access token, you can retrieve user’s info or access any other resource in Azure tenant. The InteractiveBrowserCredential uses Authorization Code Flow to authenticate users for browser based applications and to access resources further.
Client credential flow is OAuth flow commonly used for server-to-server interactions that usually run in the background, without immediate interaction with a user and help to acquire the token and call protected web APIs.
Sample Reference to use interactive credential flow in node : azure-sdk-for-js/interactive-browser-credential.md at main · Azure/azure-sdk-for-js (github.com)
Hope this will helps. If you have any other questions on this. Please let us know.
Thanks,
Shweta
--------------------------------------
Please remember to "Accept Answer" if answer helped you.