@Dawid Zyrek
Thank you for the detailed post!
If you're the only user allowed access to the Key Vault via the Access Policies and have only been accessing the Key Vault via the Azure Portal, those logs should only be actions from the Portal. If you've ever used the Azure Key Vault REST API to access the key vault, I wasn't able to find any distinction between the two VaultGet calls, when reviewing the logs since the Azure Portal uses the REST API calls as well.
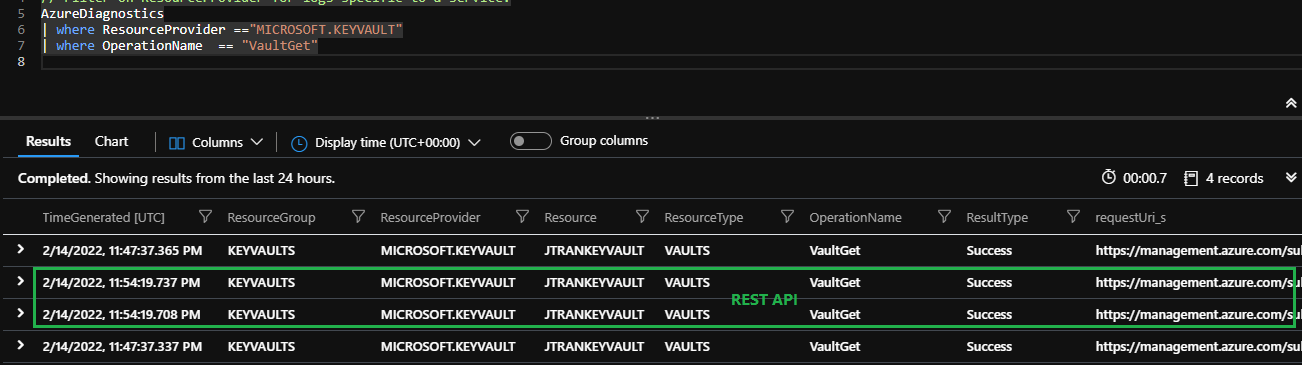
If you'd like to provide some sort of distinction when reviewing logs, you can leverage other Key Vault authentication options such as application-only, using another user, or the Application-plus-user (sometimes referred as compound identity).
Example of compound identity:
The user is required to access the key vault from a specific application and the application must use the on-behalf-of authentication (OBO) flow to impersonate the user.
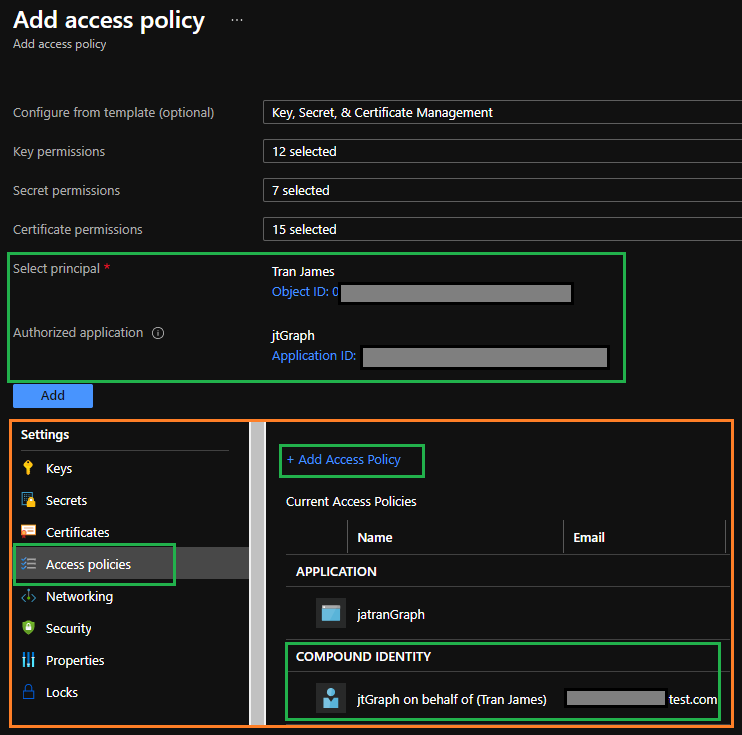
Additional Link:
The Key Vault request operation flow with authentication
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
