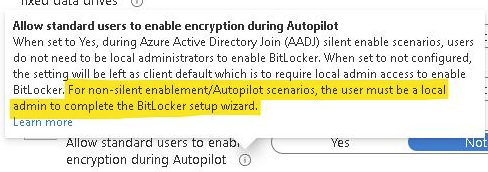
Intune has no ability to do this. Today, you need to use a supplemental method, like a script, to prompt an end-user for a PIN (aka preboot authentication password) to set. This script will need to be run elevated as well as this does require local admin privileges to set (or reset).
Setup Intune Bitlocker Statup Pin Will Not Work

I can not seem to figure out what is required to get Intune Bitlocker to prompt a user (even as admin) for a password. I have read all the docs repeatedly and I feel I'm just missing something.
What do I need to get Bitlocker to work as documented?
Right now it seems my policy enables bitlocker but never prompts.
As admin I can set a pin.
I'm lost with Bitlocker it seems overly simplified in documentation and then nothing works in practice.
7 answers
Sort by: Most helpful
-
 Jason Sandys 31,196 Reputation points Microsoft Employee
Jason Sandys 31,196 Reputation points Microsoft Employee2022-03-04T20:49:13.247+00:00 -
Nick Hogarth 3,436 Reputation points
2022-03-06T21:05:27.407+00:00 In addition to Jason's comment, here is a good blog post that has a workaround where you can use TPM startup and then deploy an app to get the user to set a Bitlocker PIN. https://oliverkieselbach.com/2019/08/02/how-to-enable-pre-boot-bitlocker-startup-pin-on-windows-with-intune/
-
 ComputerHabit 861 Reputation points
ComputerHabit 861 Reputation points2022-03-07T14:26:32.27+00:00 Yeah I had started reading the link mentioned above.
I'm not really used to administrating bitlocker. Do most people use the startup password? Does it seem like a bad idea to encrypt with an end user password?
-
 Jason Sandys 31,196 Reputation points Microsoft Employee
Jason Sandys 31,196 Reputation points Microsoft Employee2022-03-07T14:34:41.127+00:00 That's a bit of a loaded question. In general, we try to discourage folks from using a pre-boot authenticator as it prevents systems from rebooting without requiring human intervention. This can be quite undesirable in a number of situations including unattended updates which are common in most environments. There are some attack vectors on TPMs though -- whether these are viable depends on the TPMs your systems use (the attacks are all physical in nature) and whether they are truly a risk is for your org to decide. I'd say in general, most orgs should not consider this a risk, but I don't have any responsibility there so that's possibly easy for me to say. You will find debate on this point.
Note that the pre-boot auth password is not used to encrypt to drive and is not user specific. It's just a hardware level password used to unlock the TPM.
-
 Jason Sandys 31,196 Reputation points Microsoft Employee
Jason Sandys 31,196 Reputation points Microsoft Employee2022-03-08T14:36:26.383+00:00 I don't want my end users having Admin access of course and that seems to be the main criteria to set the startup pin. So the app mentioned is probably the way to go.
No, not at all which is exactly why I called out that a preboot authenticator (aka PIN) and recovery password are two completely different things. As I called out in my previous answer, the only thing that the preboot auth does is unlock the TPM so that the encryption key is available to the OS to use to access the encrypted disk volume. The recovery password is used to recovery a BitLocker volume that has been locked for one of a variety of reasons usually related to the detection of tampering with the device or OS. Users do not choose recovery passwords, these are generated randomly by the system and are 48 characters long. You don't keep a list of these, these are escrowed (aka saved with controlled) to an escrow system like MBAM or ConfigMgr (this is truly the main purpose in life for MBAM) or saved to AAD or AD.
The main reason to set up a preboot auth is to mitigate the risk of a physical attack on the TPM that could allow the encryption key to be stolen. As noted, this is a physical level, hardware attack on the TPM itself that greatly depends on the physical design of the TPM and motherboard as how big of risk this type of attack actually is.
Not having a PIN does equate to a lower level of security because of this, but as with all security, you need to evaluate the risk and compare that against other factors to determine whether you truly need it. Thus, I'll say it again here that most orgs do not deem the use of a prebott authenticator necessary as the physical attacks on the TPM are generally non-trivial and not ubiquitous, i.e., attacks vary between different types of TPMs and motherboards and not all TPMs are even susceptible to any known attacks.