Hi @Piyumi Perera ,
Thanks for reaching out.
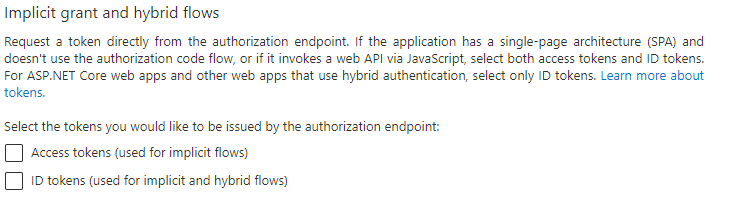
From you query, I understand that you are calling custom Web API from Single Page application and getting "invalid token" error while authorizing the Web API.
Protected APIs are protected and called by authorized identity only using bearer token which holds the information about authorized identity to validate against protected API.
Web API need to configure a bearer token by specifying the authority, audience, tenant id JSON configuration based on your requirement
{
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"ClientId": "[Client_id-of-web-api-eg-2ec40e65-ba09-4853-bcde-bcb60029e596]",
/*
You need specify the TenantId only if you want to accept access tokens from a single tenant
(line-of-business app).
Otherwise, you can leave them set to common.
This can be:
- A GUID (Tenant ID = Directory ID)
- 'common' (any organization and personal accounts)
- 'organizations' (any organization)
- 'consumers' (Microsoft personal accounts)
*/
"TenantId": "common"
},
"AllowedHosts": "*"
}
ASP.net forwarded the bearer token to JWTBearer middleware which calls Microsoft Identity Model Extension for .Net.
public void ConfigureServices(IServiceCollection services)
{
services.AddAuthentication(AzureADDefaults.JwtBearerAuthenticationScheme)
.AddAzureADBearer(options => Configuration.Bind("AzureAd", options));
Currently Microsoft.Identity.Web is recommended where middleware can be initialized as
public void ConfigureServices(IServiceCollection services)
{
services.AddMicrosoftIdentityWebApiAuthentication(Configuration, "AzureAd");
}
or
public void ConfigureServices(IServiceCollection services)
{
// Adds Microsoft Identity platform (AAD v2.0) support to protect this API
services.AddAuthentication(AzureADDefaults.JwtBearerAuthenticationScheme)
.AddMicrosoftIdentityWebApi(Configuration, "AzureAd");
services.AddControllers();
}
Hope this will help to configure middleware to accept bearer token for web API with valid scopes which can be validated using jwt.ms
Thanks,
Shweta
----------------------------------------------------
Please remember to "Accept Answer" if answer helped you.