Hi @Rameez Ali ,
Thanks for reaching out and apologies for delay in response.
I understand you are looking to restrict the user to access the resources which has been granted earlier and user still has credentials to access the application.
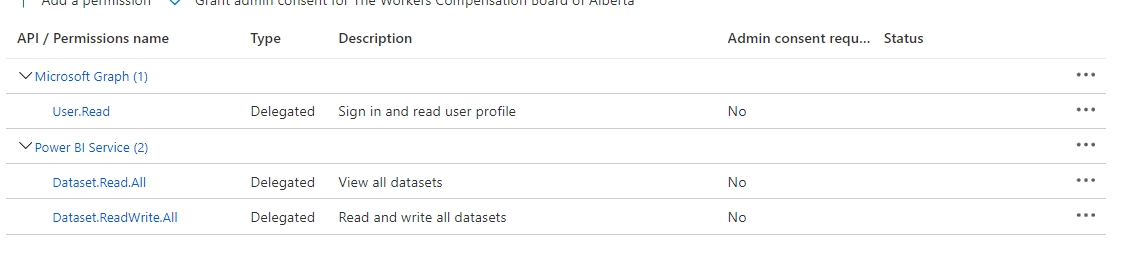
1.This is basically depends on the configuration of the application. If your application has been protected and authorizing users to verify right scopes and roles for each action, then you can restrict the user by revoking permissions in new access token to not perform particular action.
[Authorize]
public class TodoListController : Controller
{
/// The web API will accept only tokens for users that have the `access_as_user` scope for this API.
static readonly string[] scopeRequiredByApi = new string[] { "access_as_user" };
[HttpGet]
public IEnumerable<TodoItem> Get()
{
HttpContext.VerifyUserHasAnyAcceptedScope(scopeRequiredByApi);
}
}
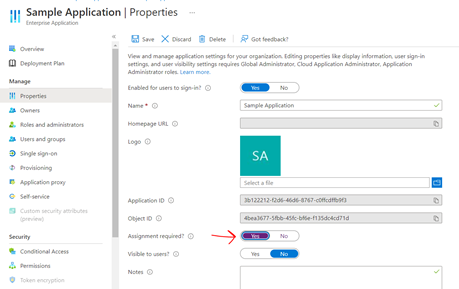
2.Another way to restrict the user completely to not grant access to the application in Azure AD by checking the "Assignment required" box in your Enterprise application, then users must be assigned to the application before being able to access it. But this will not work if user is allowed to perform another operations in the application.
3.One more safest approach is to rotate the secret/certificate and create new secret for the application. In this if you have large number of users using the application, you need to share new secret among all.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.