Hi @Anthony Chu - MSFT I am nearly finished with my Xamarin + Azure app and would greatly appreciate your insight on this troubling issue! Thank you for being such a legend so far with your great support.
I'm building a Xamarin.Forms app that loads HTML pages via HTTPS from Azure Static Web Apps using a Xamarin.Forms custom webview (derived from WkWebViewRenderer on iOS). The webview works well, except that when I enabled an "authenticated users only" role for my books directory in SWA in staticwebapp.config.json, I get a 401 Unauthorized error back from SWA when I use Active Directory B2C for authentication inside my mobile app. Here are my diagnostic steps so far:
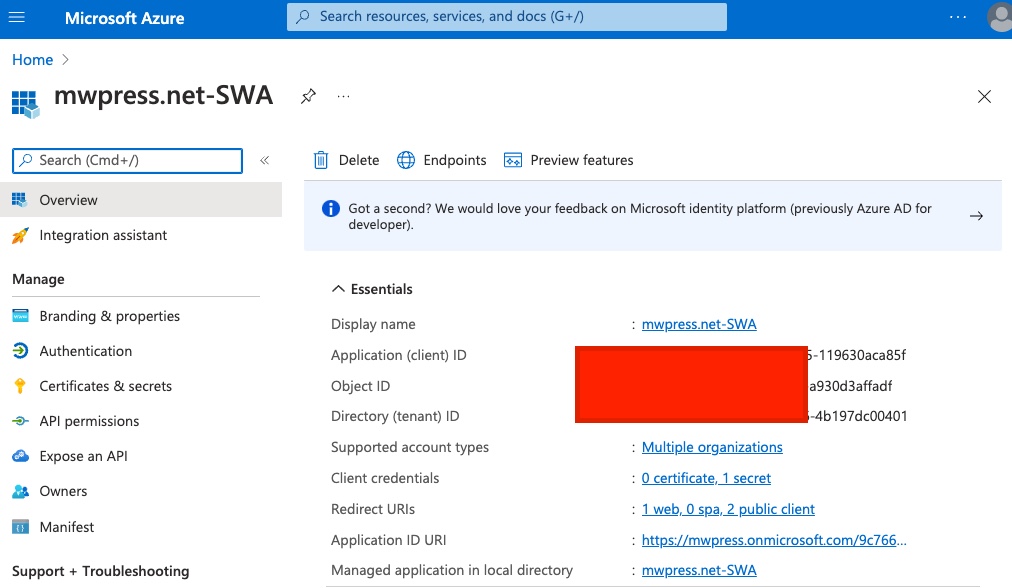
- Registered Azure Static Web App and Xamarin.Forms iOS/Android app in AAD B2C (directory: 'Mental Wealth Press'). NOTE: Azure Static Web app has ADB2C app ID ending in '85f' (Azure DNS Zone: mwpress.net - DEFAULT directory)
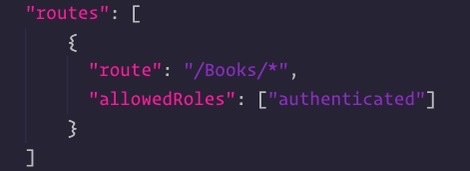
- Updated my SWA's staticwebapp.config.json to only allow authorized HTTPS requests to my 'Books' directory:
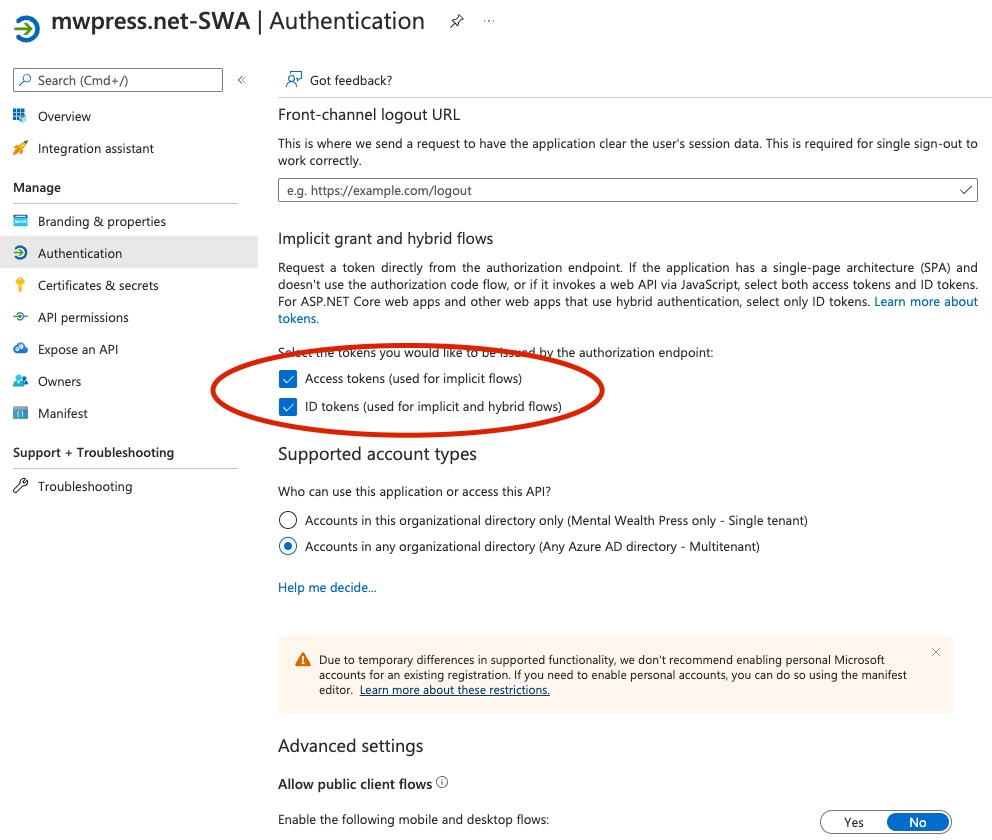
- Checked that my AD B2C app registration for my Azure Static Web app had authentication turned on (I successfully retrieve an access token via MSAL later):
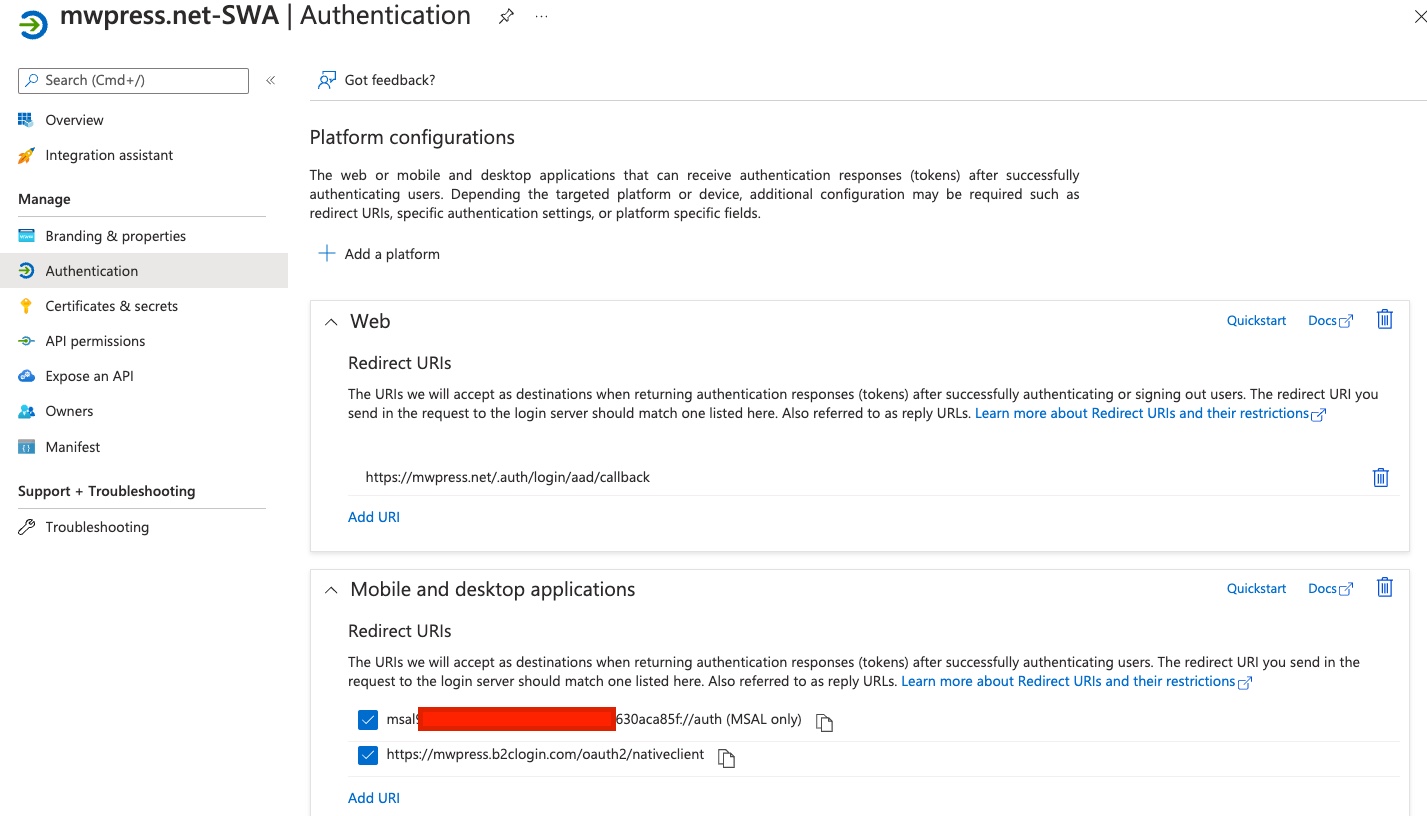
- I have also registered my Xamarin.Forms app in AD B2C, it has an app ID ending with 9fc5. This 9fc5 becomes important later because it is used as the Client ID for MSAL AcquireTokenInteractive().:


- Both of my AD B2C app registrations (SWA 85f and Xamarin forms 9fc5), have scopes set in AD B2C:

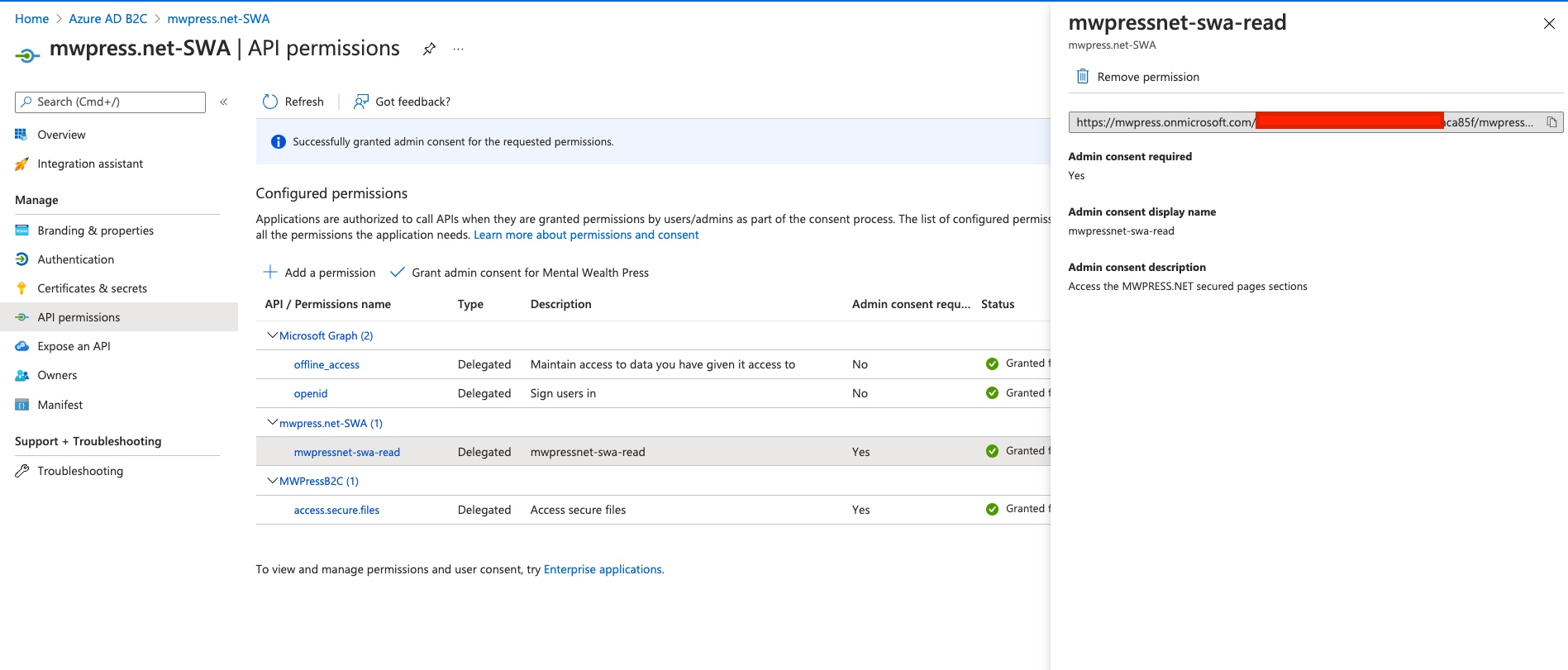
- I use MSAL to grab an access token from AD B2C with the following credentials:


- My Xamarin.Forms app successfully authenticates via Azure AD B2C, and I get back a valid access token, which looks like this. Notice that the 'audience' is for my SWA app ID ending in 85f (my app registration for Static Web App):

But...when I actually try to access my pages on my SWA app using Bearer Authentication, I get a 401 Unauthorized. Here is what I get in Postman using the access token from Step 7:

I have also confirmed that my Xamarin app is actually sending in the right Bearer Authorization header obtained from my AD B2C access token, by loading this page ("whatismybrowser.com/detect/what-http-headers-is-my-browser-sending") with the auth header set in my Xamarin iOS custom webview:


One more test was to use the B2C App ID of my Static Web App instead of my Xamarin App to login and obtain the access token, but that throws an even stranger message, this time during B2CLOGIN. The error B2CLOGIN returns is "AADB2C90068: The provided application with ID ending in ca85f is not valid against this service. Please use application created via the B2C portal and try again" - but I did create the app registration via the B2C portal in the first place???!?!:


Have absolutely no idea how to diagnose this problem, any fixes or assistance would be greatly appreciated.