Hi @Ramachandran Krishnamoorthy ,
I understand that you are hoping to block access to users who try to access company resources with your personal device. (Please correct me if I'm wrong, as I can interpret your description to either mean that you want to block the access entirely on personal devices or enforce MFA for them.)
To block access on personal devices, there are two settings you can use in Conditional Access:
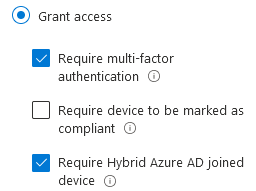
- Require device to be marked as compliant - Marked as compliant means the device is enrolled in a mobile device management solution, such as Intune, and meets that MDM’s compliance requirements, such as having an active firewall.
- Require Hybrid Azure AD joined device - This means that the device is joined to your on-premises Active Directory, but also synchronized and joined to the cloud-based Azure AD.
Conditional access gives you the option to require one or both of these controls so that both on-premises domain joined and Azure AD only joined devices can get access. (This is the recommended approach as well.)
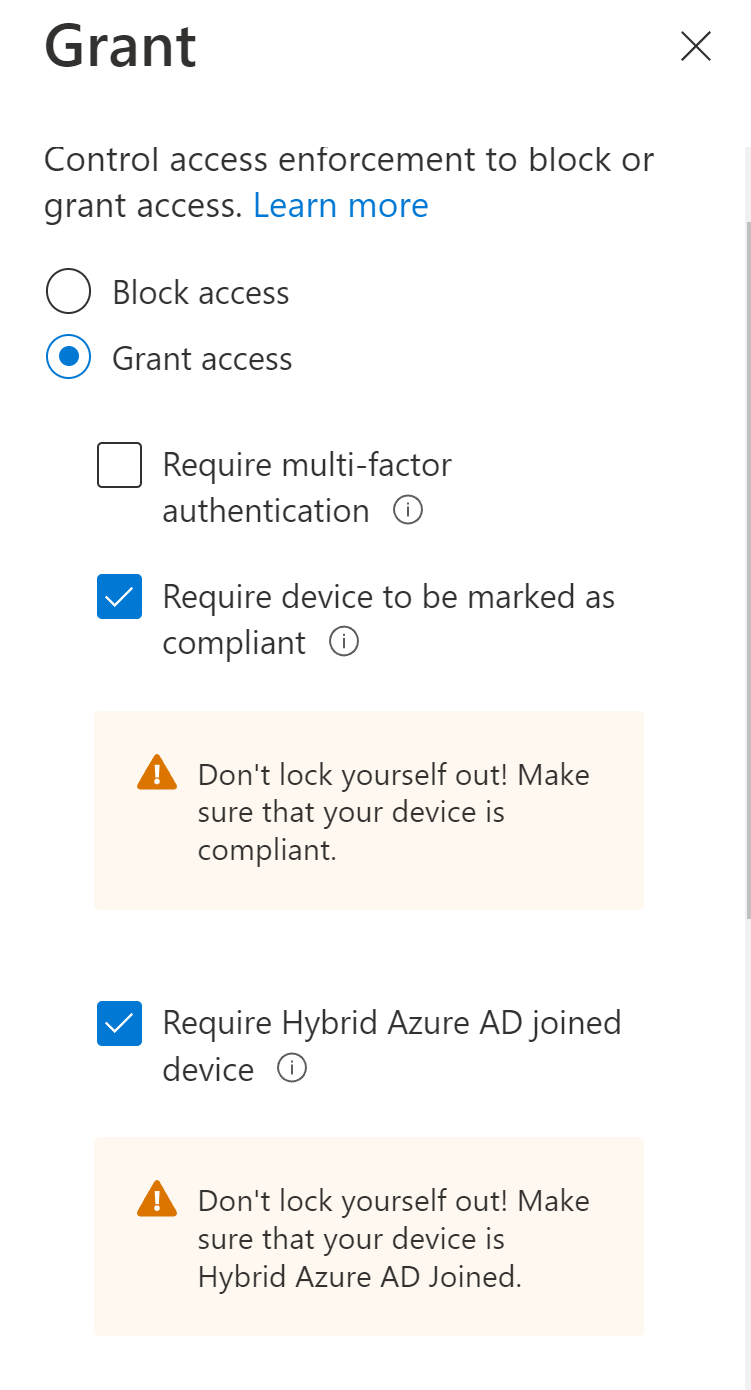
You also have the option to set compliance policies based on particular criteria.
Let me know if this helps.
Here are the official guides for this setting:
Conditional Access: Require compliant or hybrid Azure AD joined device
Use compliance policies to set rules for devices you manage with Intune