Hi @David • Thank you for reaching out.
You can control SSO behavior by using the below settings in Azure AD B2C:
- If you are using User Flow, go to properties of the user flow and set below setting to either
TenantorPolicy. If you set it to policy, SSO experience between Web_App_1 and Web_App_2 will be provided when both applications are authenticated via same user flow.
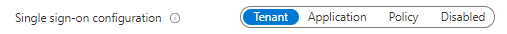
- If you are using a custom policy, you can set the above setting by configuring the
SingleSignOn Scopeto eitherTenantorPolicyin the RP file (signup/sign-in file).
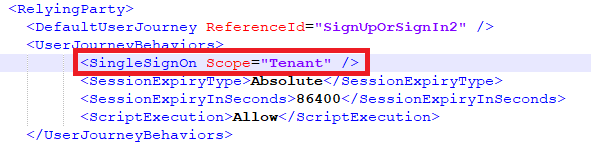
With the above configuration, users with access to both Web_App_1 and Web_App_2, will get SSO experience. Whereas, for the other set of users who have access to Web_App_1 but not to Web_App_2 or vise versa, you will have to configure applications to perform the authorization. As you already know, you can use API connectors to enrich the user access token with application-specific authorization data. You can also use this approach without using the API connector if the application can distinguish between the allowed and restricted users by looking at a claim populated from built-in or a custom attribute, e.g., allow users with country x and deny if the value of the country claim is y.
In short, regardless of what approach you choose or your application supports, it is a piece of authorization and has to be done from the application side. You cannot configure it from the B2C side.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
