Hi @Christine Fecteau • Thank you for providing the required details to investigate the issue.
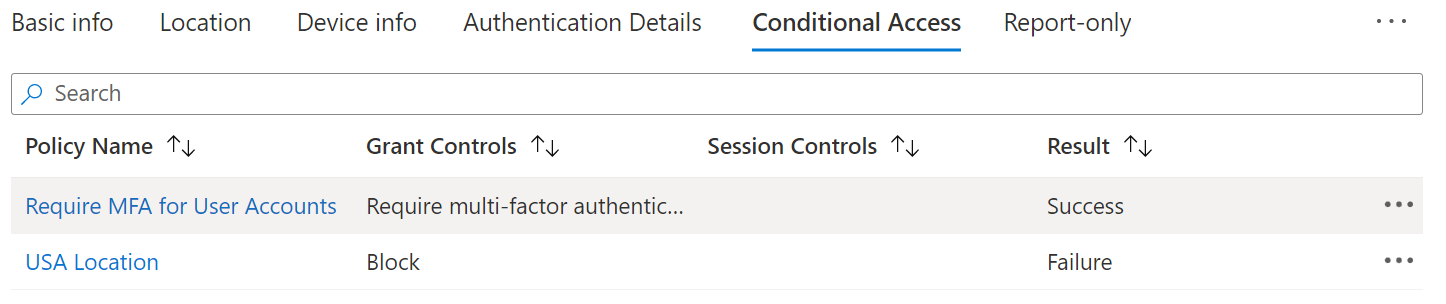
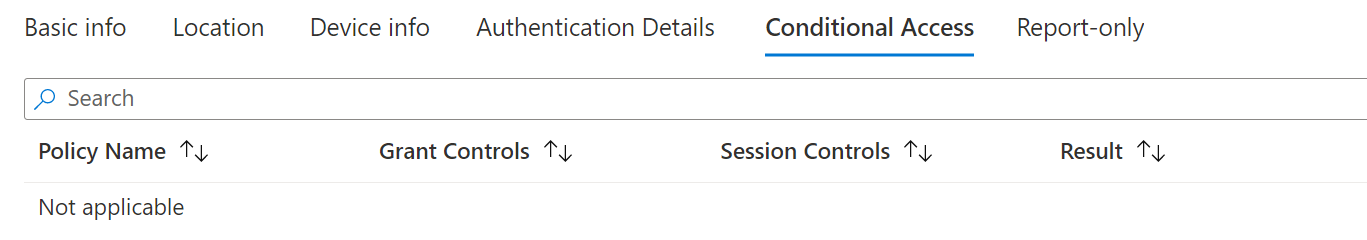
By tracking the correlation ID, I found that the conditional access evaluation was skipped because of the 'bootstrap' scenario. There are multiple scenarios that CA consider as 'bootstrap' and one of them is when the target audience is OCaaS Client Interaction Service, which is a Microsoft Service present by default in all Azure AD tenants. The "OCaaS Client Interaction Service" is usually accessed by the office client applications such as Outlook, Onedrive, etc. to complete the required flows uninterruptedly required by these clients to work properly.
In your case, the application 'OneDrive' redeemed a refresh token to access OCaaS Client Interaction Service and the conditional access evaluation was skipped. We consider such scenarios as expected behavior and can be safely ignored. Looking at the screenshot that you shared, I can see that all applications are within the scope of the CA policy. So, CA policy evaluation will only the bootstrap services and not other services.
Another example of the bootstrap scenario is Intune Management Setup, for which CA evaluation is skipped in favor of Intune to complete its flow uninterruptedly.
Hope this information help address your concerns.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.