Hi adusheba-9169,
Thanks for reaching out.
I understand you are looking to verify the signature of the access token issued by Azure Ad by using public endpoint.
An access token contains claims that you can use in Azure Active Directory to identify the granted permissions to your APIs. When your internal application receives an access token, it must validate the signature to prove that the token is authentic.
To Verify the JWT token:
Verify that the JWT contains three segments, separated by two period ('.') characters.
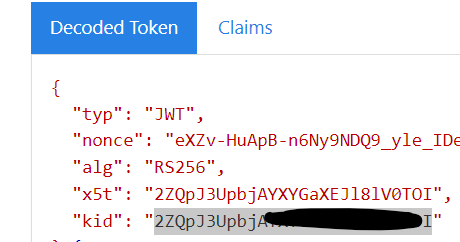
Parse the JWT to extract its three components. The first segment is the Header, the second is the Payload, and the third is the Signature. Each segment is base64url encoded.
Signature contains the digital signature of the token that was generated by Azure AD’s private key and verify that the token was signed by the sender.
To validate the authenticity of the JWT token’s data is by using Azure AD’s public key to verify the signature.
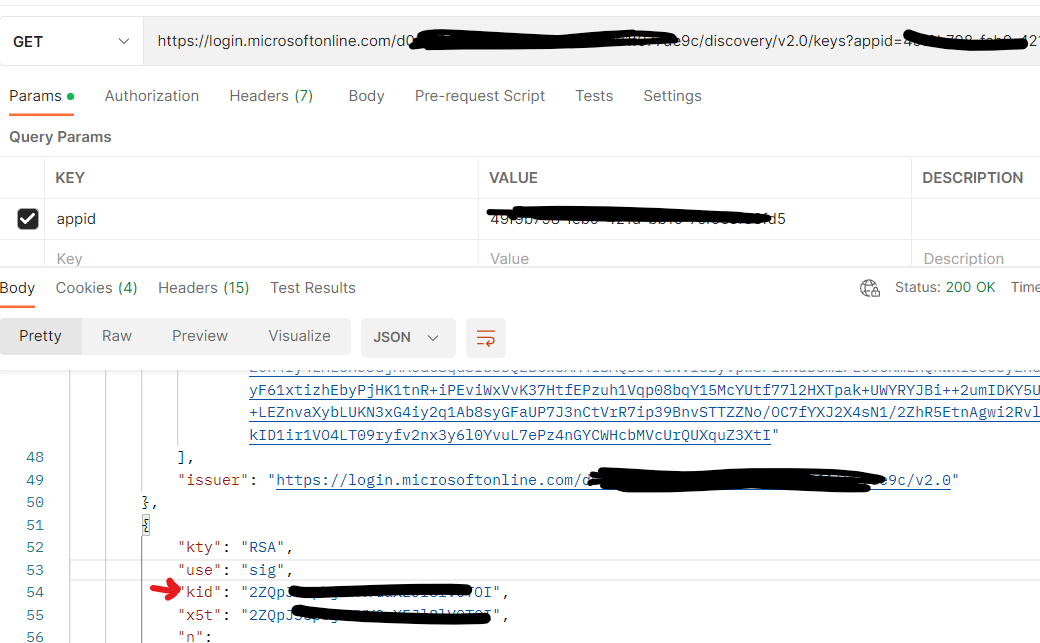
You can obtain public key by calling the public Azure AD OpenID configuration endpoint:
https://login.microsoftonline.com/{tenant_id}/discovery/keys?appid={client_id} and verify against the private key generated by Azure AD token. For validation, developers can decode JWTs using jwt.ms and verify against "kid" claim.
If it works, you know the contents were signed with the private key. If not, you can’t be sure of it so you should treat the JWT token as an invalid token.
The warning which is mentioned is regarding that access token are secure and contain sensitive information so we should avoid reading other's tokens and secure our tokens securely from attacks.
Hope this will help.
Thanks,
Shweta
--------------------------------------------
Please remember to "Accept Answer" if answer helped you.