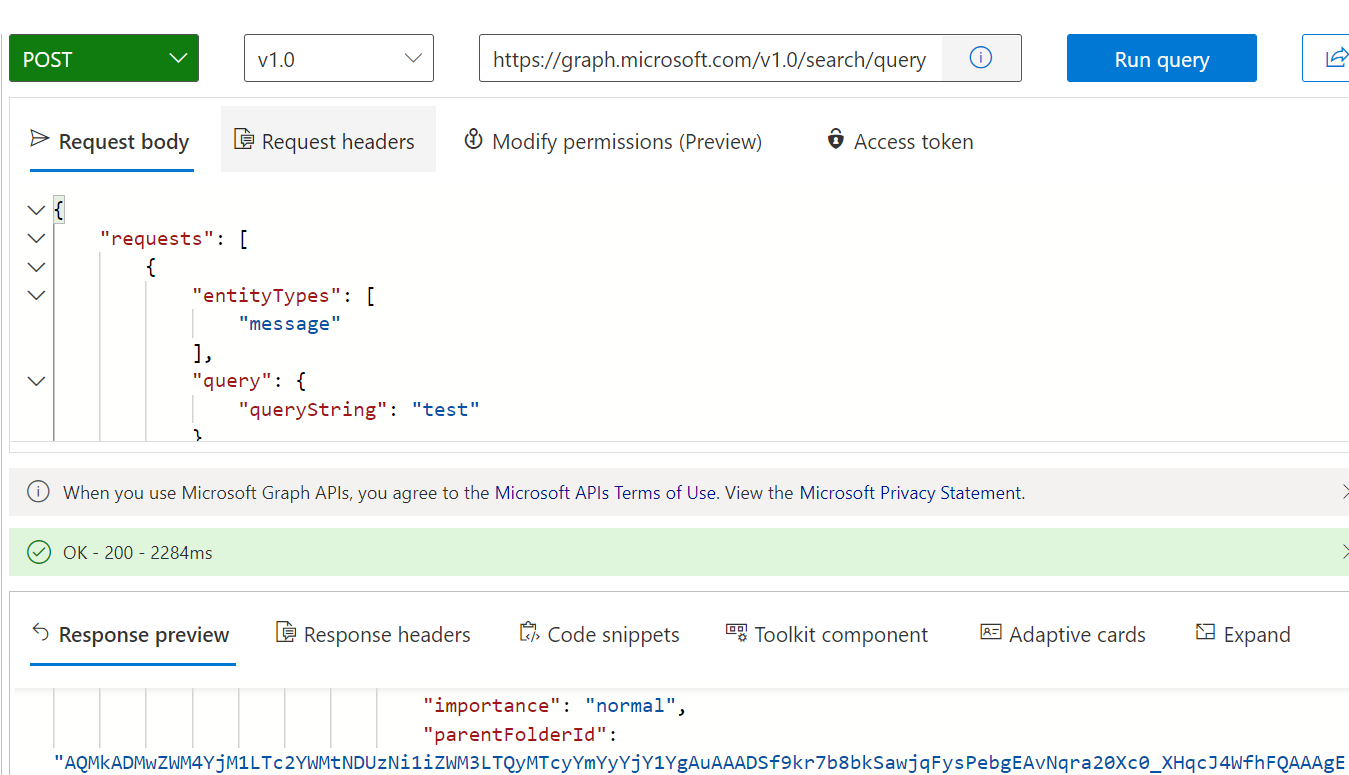
Hi @Blue Tongue • This depends on the context that you used to acquire the token. If you have acquired the token with user context, you can only access your own messages. This is because there is no delegated permission in Graph API that allows reading other users' messages. That is why it is working when you use the /me endpoint and not when you specify a different user account.
However, if you acquire the token with application context, you can add and grant admin consent for the user.read application (not delegated) permission to get read access to all users' messages.
- Navigate to Azure AD > App Registration > Register new app and copy the ClientID.
- Generate a client secret and copy that as well.
- Under Api Permissions blade, add https://graph.microsoft.com/user.read application permission and grant admin consent.
Then acquire the token using below method:
$ApplicationID = "Paste client ID from step1"
$TenatDomainName = "YOUR_TENANT.onmicrosoft.com"
$AccessSecret = 'Paste client secret from step2'
$Body = @{
Grant_Type = "client_credentials"
Scope = "https://graph.microsoft.com/.default"
client_Id = $ApplicationID
Client_Secret = $AccessSecret
}
$ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenatDomainName/oauth2/v2.0/token" `
-Method POST -Body $Body
$token = $ConnectGraph.access_token
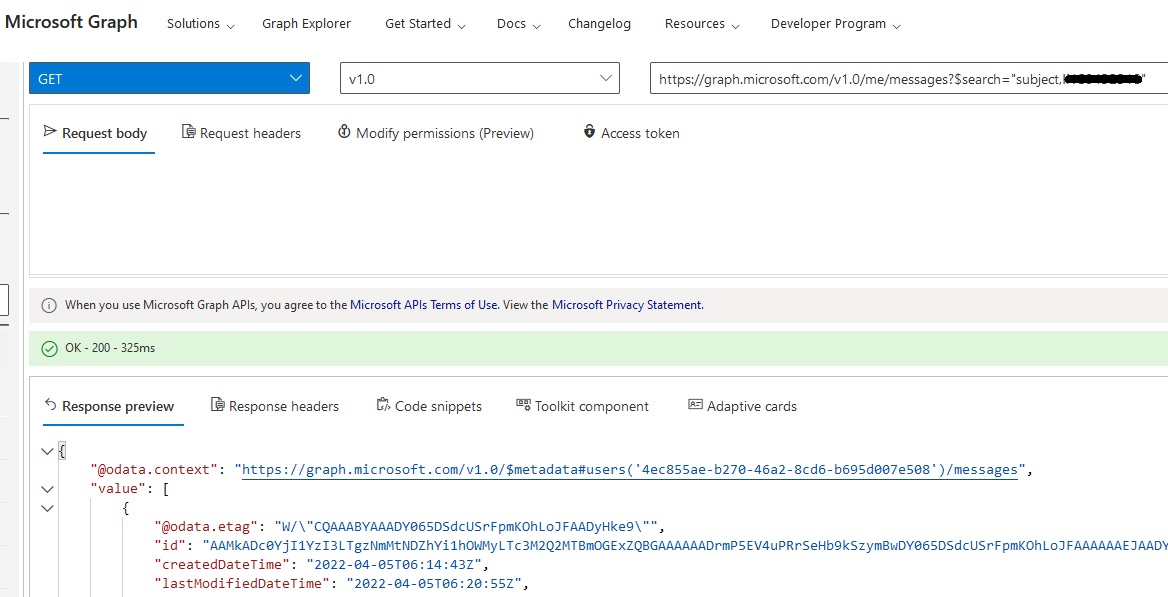
You can then use the token as bearer in the Authorization header of the request, to query any user's messages as shown below:

-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.