This is also happening on Checkpoint Endpoint VPN client. It may eventually happen after the user changed their domain account password. If the certificate is re-imported it will work.
https://support.checkpoint.com/results/sk/sk178727
Greetings
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Dear
Our domain joined Windows 10 Enterprise (1909 / 20H2 / 2019 LTSC) clients are getting a machine certificate through an internal AD CA when machine group policy processing is done. This auto enrolled certificate has a validity of one year. A few weeks prior to the expiry date they are renewed (with a new private key) automatically.
In a small percentage of cases, something this goes wrong and the certificate becomes invalid as the private key is no longer found or linked to the cert.
This certificate is used in the host compliancy check for our SSL VPN solution. When the certificate issue occurs, users cannot establish a connection with the VPN because the certificate is not “valid”.
The following is the certutil output of a end-user device with this issue. Some names were obfuscated for privacy reasons. In the personal store of the machine you can see an archived certificate and the renewed certificate. Please note that the archived certificate has a “simple container name” entry and the message that the private key is not exportable.
C:\Windows\system32>certutil -store my
my "Personal"
================ Certificate 0 ================
Archived!
Serial Number: 1500054bf462edd8af4e8715db000000054bf4
Issuer: CN=subdomain-ISSUING-CA, DC=subdomain, DC=company, DC=com
NotBefore: 5/10/2021 3:30 PM
NotAfter: 5/10/2022 3:30 PM
Subject: CN=COMPUTER-030651.subdomain.company.com
Non-root Certificate
Template: 1.3.6.1.4.1.311.21.8.14979681.12405196.1132950.8513548.8995499.105.12472998.10710845, subdomain - Workstation
Cert Hash(sha1): 9b9f77e9b9f504425f54894df26b3aca21ac828b
Key Container = 1a6d6aaa6a6a7b3278f4d5e1677a6256_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
Simple container name: te-subdomain-Workstation-72d33244-7d8a-4b2d-b284-e1f8378ec03e
Provider = Microsoft RSA SChannel Cryptographic Provider
Private key is NOT exportable
Encryption test passed================ Certificate 1 ================
Serial Number: 1500103f783acd064a7293fb38000100103f78
Issuer: CN=subdomain-ISSUING-CA, DC=subdomain, DC=company, DC=com
NotBefore: 3/30/2022 9:35 AM
NotAfter: 3/30/2023 9:35 AM
Subject: CN=COMPUTER-030651.subdomain.company.com
Non-root Certificate
Template: 1.3.6.1.4.1.311.21.8.14979681.12405196.1132950.8513548.8995499.105.12472998.10710845, subdomain - Workstation
Cert Hash(sha1): 17f29a9842efd0af6faf642d44afa3a4f8a76378
Key Container = 185b3e683d848c978d87b2ce5a0dcc06_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
Provider = Microsoft RSA SChannel Cryptographic Provider
Missing stored keyset
In C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys both private key files are present.
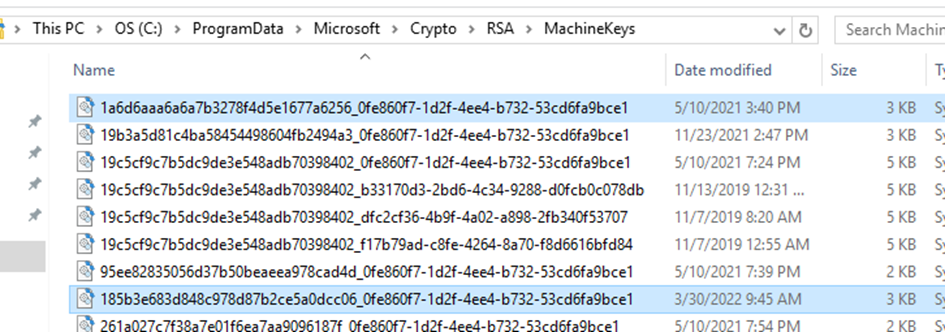
In the registry both the certificates and the keys are present as well:
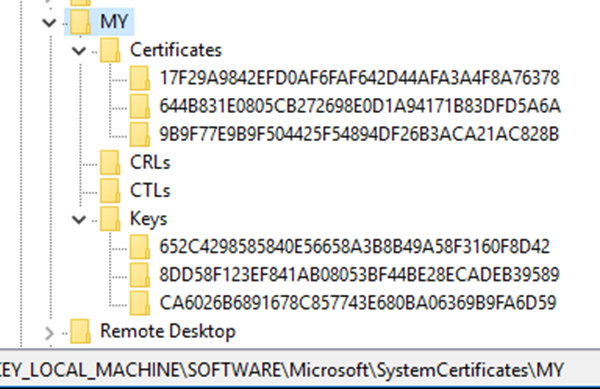
RFC-SHA1 key 652C4298585840E56658A3B8B49A58F3160F8D42 corresponds with key container 185b3e683d848c978d87b2ce5a0dcc06_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
RFC-SHA1 key 8DD58F123EF841AB08053BF44BE28ECADEB39589 corresponds with key container 1a6d6aaa6a6a7b3278f4d5e1677a6256_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
When we enumerate all keys from the Microsoft RSA provider I get the error 0x8009000b NTE_BAD_KEY_STATE for what I presume is the simple name container for the private key of the renewed certificate.
C:\Windows\system32>certutil -csp "Microsoft RSA SChannel Cryptographic Provider" -key
Microsoft RSA SChannel Cryptographic Provider:
cuLoadKey: LoadKeys returned Key not valid for use in specified state. 0x8009000b (-2146893813 NTE_BAD_KEY_STATE) -- te-SUBDOMAIN-Workstation-a0d6630f-9c0e-4780-9e6a-9b3da0c64421
cuLoadKey: LoadKeys returned Keyset as registered is invalid. 0x8009001a (-2146893798 NTE_KEYSET_ENTRY_BAD) -- SMS
te-SUBDOMAIN-Workstation-72d33244-7d8a-4b2d-b284-e1f8378ec03e
1a6d6aaa6a6a7b3278f4d5e1677a6256_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
RSA
AT_KEYEXCHANGETSSecKeySet1
f686aace6942fb7f7ceb231212eef4a4_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
RSA
AT_KEYEXCHANGEcuLoadKey: LoadKeys returned Invalid type specified. 0x8009000a (-2146893814 NTE_BAD_TYPE) -- DefaultKeys
CertUtil: -key command completed successfully.
According to the WinCrypt API documentation it means that the user password has changed since the last encryption. It’s a computer certificate and the computer account password change has been disabled on the system so I’m not sure why this error is being thrown.
C:\Windows\system32>reg query "HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" /f Disable
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
DisablePasswordChange REG_DWORD 0x1End of search: 1 match(es) found.
So all information seems to be there.
In the computer certificate mmc there is no obvious error been shown.
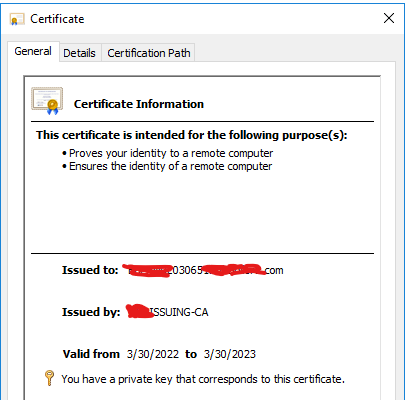
When we renew the certificate manually with “certreq -enroll -machine -q -PolicyServer * -cert <Cert_SN> renew” everything seems to be fine.
Unfortunately, the issue only becomes apparent when the user is not in the corporate network (most likely at home) and trying to connect on the VPN. If the user contacts the servicedesk we can’t re-enroll the certificate from their home as they need to be connected to the corporate network in order to reach the internal CA to get a new cert. So users must come to the office to resolve the issue.
Does anyone have any idea on how to troubleshoot this further? Why is the cert – private key pair broken? Happy to provide further info to help get to the bottom of this.
This is the verbose information of both the archived and renewed certificates:
C:\Windows\system32>certutil -v -store my
my "Personal"
================ Certificate 0 ================
Archived!
X509 Certificate:
Version: 3
Serial Number: 1500054bf462edd8af4e8715db000000054bf4
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=SUBDOMAIN-ISSUING-CA
DC=subdomain
DC=company
DC=com
Name Hash(sha1): dcfdcd803ecd3f5a350bf250b071668457e5acaa
Name Hash(md5): 2fba5791d04b64043702b5cb65524b82NotBefore: 5/10/2021 3:30 PM
NotAfter: 5/10/2022 3:30 PMSubject:
CN=COMPUTER-030651.subdomain.company.com
Name Hash(sha1): 21d39ae7302d6da0117377d7ffbae2ec6ba369d2
Name Hash(md5): d2196a2e04bd4290affa58ef5e078f98Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 b0 0e 35 9e cc 30 48
0010 9b d4 94 60 9f 86 3f f6 3a 66 ba 5f ef da 0f 52
0020 a1 37 ef 2a 3d b2 b8 6f a3 a8 5d fd 61 f6 3b 53
0030 2c 9b c9 03 7f 0c d3 f7 0b 65 12 00 0f 91 56 27
0040 5e da 2d 69 9a 0a 32 c5 4c 7d dd e3 4f 34 bf 4e
0050 27 52 01 86 b4 06 b5 35 41 bb 49 77 02 e1 66 f2
0060 9c cf 53 0b da a7 6c 04 88 ac 43 e2 8e 83 b2 50
0070 d8 72 c6 ec cc a4 0f de f1 31 a1 21 3b 5d cf 44
0080 b6 c3 17 dc 60 f3 10 7d d3 c2 6e e8 ee fe 94 4f
0090 cf f8 93 a7 c7 2b 1d 9f c4 7b 07 84 db 44 a9 a5
00a0 c4 cf f8 64 3c 60 20 02 b0 e0 33 2d d9 13 6d 64
00b0 c6 c9 fb ee e4 03 43 de e6 c5 4c c2 c4 4b d0 a3
00c0 20 ec 4e 6b 38 98 7e d8 eb 1e bc 22 5c e2 7c 89
00d0 dd 1f 93 60 79 b7 76 c1 5a a8 ca 35 48 fb 0d ad
00e0 3a f3 de a1 3d 41 9c ad af 20 35 7b 60 79 50 52
00f0 60 b2 10 ad 8d f7 98 fe ac b2 c1 19 48 4b 73 2b
0100 e7 01 0c ec 60 77 2d c5 b5 02 03 01 00 01
Certificate Extensions: 9
1.3.6.1.4.1.311.21.7: Flags = 0, Length = 2f
Certificate Template Information
Template=SUBDOMAIN - Workstation(1.3.6.1.4.1.311.21.8.14979681.12405196.1132950.8513548.8995499.105.12472998.10710845)
Major Version Number=100
Minor Version Number=212.5.29.37: Flags = 0, Length = 16 Enhanced Key Usage Client Authentication (1.3.6.1.5.5.7.3.2) Server Authentication (1.3.6.1.5.5.7.3.1) 2.5.29.15: Flags = 1(Critical), Length = 4 Key Usage Digital Signature, Key Encipherment (a0) 1.3.6.1.4.1.311.21.10: Flags = 0, Length = 1a Application Policies [1]Application Certificate Policy: Policy Identifier=Client Authentication [2]Application Certificate Policy: Policy Identifier=Server Authentication 2.5.29.14: Flags = 0, Length = 16 Subject Key Identifier 8d d5 8f 12 3e f8 41 ab 08 05 3b f4 4b e2 8e ca de b3 95 89 2.5.29.35: Flags = 0, Length = 18 Authority Key Identifier KeyID=26 12 4b e0 48 d5 24 6d 4d f9 75 25 db 16 1c 27 ee 01 68 2e 2.5.29.31: Flags = 0, Length = 110 CRL Distribution Points [1]CRL Distribution Point Distribution Point Name: Full Name: URL=ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=SFRCRBPKI002VM,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint (ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=SFRCRBPKI002VM,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint) URL=http://crl.subdomain.company.com/CertEnroll/SUBDOMAIN-ISSUING-CA.crl 1.3.6.1.5.5.7.1.1: Flags = 0, Length = 12f Authority Information Access [1]Authority Info Access Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2) Alternative Name: URL=ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?cACertificate?base?objectClass=certificationAuthority (ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?cACertificate?base?objectClass=certificationAuthority) [2]Authority Info Access Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2) Alternative Name: URL=http://crl.subdomain.company.com/CertEnroll/SUBDOMAIN-ISSUING-CA.crt [3]Authority Info Access Access Method=On-line Certificate Status Protocol (1.3.6.1.5.5.7.48.1) Alternative Name: URL=http://ocsp.subdomain.company.com/ocsp 2.5.29.17: Flags = 0, Length = 51 Subject Alternative Name Other Name: Principal Name=COMPUTER-030651$@subdomain.company.com DNS Name=COMPUTER-030651.subdomain.company.comSignature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 5a d5 13 d5 11 de 97 91 2e 09 15 7e 6c e3 9b 75
0010 79 b9 51 1d e0 dd 39 40 47 e3 db 4e 43 22 ec 54
0020 bd b9 d8 45 78 8f e2 64 70 b2 e2 98 63 af 14 23
0030 b2 1b f4 76 5a 21 93 08 d5 85 13 63 a9 22 6a 18
0040 19 91 a6 15 72 03 d8 b0 e7 2e fc 0b d2 b3 87 05
0050 e5 27 d0 6e 70 3f 7a d8 c6 4f ca 46 f1 03 b1 db
0060 3a 16 a3 c6 48 23 d1 81 6b 07 a3 8c 54 20 26 a6
0070 6b 40 31 03 fc 7d 76 53 77 58 5b e9 c6 31 73 e8
0080 5e 14 67 dd dd ff fc a4 e5 d6 5f b9 8f 00 89 38
0090 79 8f 3f 86 43 bf 95 8a 3a 3b b3 83 60 83 69 56
00a0 67 1a d9 23 27 f9 84 9d c4 75 39 29 6a 69 fd 59
00b0 74 2b c8 64 9b fc 74 21 40 77 9d 14 1d 03 35 ba
00c0 45 4d 91 2b 8f 74 4a cd 6d 6d b8 ca e9 0a 73 b3
00d0 fb 95 2c f8 c9 d4 85 ba a2 10 1e fb b1 4d 2a d3
00e0 53 f4 b2 41 a7 1c ad 34 41 ca db 59 10 c8 4a 0c
00f0 1d 73 86 da 84 f4 86 b3 f7 85 52 a7 44 55 1b 8d
Non-root Certificate
Key Id Hash(rfc-sha1): 8dd58f123ef841ab08053bf44be28ecadeb39589
Key Id Hash(sha1): 21d45f3a2a504a48d7c9d574950be195f5eaddcf
Key Id Hash(md5): 607ed300480b255776d42ab45b320eef
Key Id Hash(sha256): 88e50fa131a5f39c05e678148aeb15b204a791455744ae37658a2078b8c28471
Cert Hash(md5): 032edf61ede76f7cf36d704bb41f9fa8
Cert Hash(sha1): 9b9f77e9b9f504425f54894df26b3aca21ac828b
Cert Hash(sha256): 47fd40ddb8c281319e2a0ea8377ffc27f19a4e2d396e67c7c9a73c62f08cdc0c
Signature Hash: 6d1039baf5598b08ed6845c8e0729999913c9a96b6e505e585fa4f47bc006babCERT_REQUEST_ORIGINATOR_PROP_ID(71):
COMPUTER-030651.subdomain.company.comCERT_CEP_PROP_ID(87):
Enrollment Policy Url: ldap:
Enrollment Policy Id: {EE1464EB-310F-4070-B71E-DDC3835A498F}
Enrollment Server Url: SFRCRBPKI002VM.subdomain.company.com\SUBDOMAIN-ISSUING-CA
Request Id: 347124
Flags = 0
DefaultNone -- 0
Url Flags = 0
Authentication = 2
Kerberos -- 2
Enrollment Server Authentication = 2
Kerberos -- 2CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = 1a6d6aaa6a6a7b3278f4d5e1677a6256_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
Simple container name: te-SUBDOMAIN-Workstation-72d33244-7d8a-4b2d-b284-e1f8378ec03e
Provider = Microsoft RSA SChannel Cryptographic Provider
ProviderType = c
Flags = 20 (32)
CRYPT_MACHINE_KEYSET -- 20 (32)
KeySpec = 1 -- AT_KEYEXCHANGECERT_OCSP_CACHE_PREFIX_PROP_ID(75):
F9E78C401BCA2A15567C2C8E0036C159_CERT_ISSUER_PUBLIC_KEY_MD5_HASH_PROP_ID(24):
7fccd905eb9b7c4f87cd303e3286409eCERT_SUBJECT_PUB_KEY_BIT_LENGTH_PROP_ID(92):
0x00000800 (2048)CERT_KEY_IDENTIFIER_PROP_ID(20):
8dd58f123ef841ab08053bf44be28ecadeb39589CERT_SIGNATURE_HASH_PROP_ID(15) disallowedHash:
6d1039baf5598b08ed6845c8e0729999913c9a96b6e505e585fa4f47bc006babCERT_MD5_HASH_PROP_ID(4):
032edf61ede76f7cf36d704bb41f9fa8CERT_SUBJECT_PUBLIC_KEY_MD5_HASH_PROP_ID(25):
607ed300480b255776d42ab45b320eefCERT_SHA1_HASH_PROP_ID(3):
9b9f77e9b9f504425f54894df26b3aca21ac828bCERT_RENEWAL_PROP_ID(64):
17f29a9842efd0af6faf642d44afa3a4f8a76378CERT_ARCHIVED_PROP_ID(19):
EMPTYCERT_ACCESS_STATE_PROP_ID(14):
AccessState = 6
CERT_ACCESS_STATE_SYSTEM_STORE_FLAG -- 2
CERT_ACCESS_STATE_LM_SYSTEM_STORE_FLAG -- 4Provider = Microsoft RSA SChannel Cryptographic Provider
ProviderType = c
Simple container name: te-SUBDOMAIN-Workstation-72d33244-7d8a-4b2d-b284-e1f8378ec03e
RSA
PP_KEYSTORAGE = 1
CRYPT_SEC_DESCR -- 1
KP_PERMISSIONS = 3b (59)
CRYPT_ENCRYPT -- 1
CRYPT_DECRYPT -- 2
CRYPT_READ -- 8
CRYPT_WRITE -- 10 (16)
CRYPT_MAC -- 20 (32)D:PAI(A;;GAGR;;;SY)(A;;GAGR;;;BA)
Allow Full Control NT AUTHORITY\SYSTEM Allow Full Control BUILTIN\AdministratorsPrivate key is NOT exportable
Encryption test passed================ Certificate 1 ================
X509 Certificate:
Version: 3
Serial Number: 1500103f783acd064a7293fb38000100103f78
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=SUBDOMAIN-ISSUING-CA
DC=subdomain
DC=company
DC=com
Name Hash(sha1): dcfdcd803ecd3f5a350bf250b071668457e5acaa
Name Hash(md5): 2fba5791d04b64043702b5cb65524b82NotBefore: 3/30/2022 9:35 AM
NotAfter: 3/30/2023 9:35 AMSubject:
CN=COMPUTER-030651.subdomain.company.com
Name Hash(sha1): 21d39ae7302d6da0117377d7ffbae2ec6ba369d2
Name Hash(md5): d2196a2e04bd4290affa58ef5e078f98Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 da ea 1b 40 f6 5e 7b
0010 71 37 3a ca 67 44 18 4e 35 93 a4 82 24 bb e9 d3
0020 fd b4 17 15 4c 86 75 d3 10 c8 84 0f 39 b1 a8 c1
0030 9b 14 e4 b6 a3 1e b1 73 95 81 14 99 cc 3b 91 95
0040 6a bc 6a 4c c6 ec 54 7a 7b e1 70 9e 49 55 9b 5f
0050 25 c3 93 5f ac fc 13 42 8b c3 a6 69 b8 7f 29 a1
0060 55 f3 cc 0e fc 0f e3 34 c6 34 d7 4c 8b 92 31 17
0070 b7 fa e3 83 7e 2b f5 23 31 80 2a db f9 66 98 29
0080 bb d3 eb 36 0e 94 f7 7b bb 6a 16 b3 59 a7 84 ea
0090 47 85 76 04 87 4b dc 14 ee ac e1 c9 50 ad 96 9c
00a0 6b c2 9e 1f 7a c5 17 75 08 55 c7 ee 77 81 d4 db
00b0 e7 12 7c 50 0d 4f 64 47 dd ea 05 d6 d6 06 3e 10
00c0 6b d0 29 69 e9 d1 f6 4d 45 5c 4e 25 2c 95 11 31
00d0 0d 04 ed 2f 6c ce 28 63 b1 85 8b a4 eb 0f 8d ba
00e0 da 2d 32 e6 db 9a ba 5d 3f 6b 29 7b e5 98 35 3d
00f0 82 2b 50 57 6a 69 7a 40 3d a8 74 e9 9a 35 ed f5
0100 38 79 81 a9 68 80 fb 34 9d 02 03 01 00 01
Certificate Extensions: 9
1.3.6.1.4.1.311.21.7: Flags = 0, Length = 2f
Certificate Template Information
Template=SUBDOMAIN - Workstation(1.3.6.1.4.1.311.21.8.14979681.12405196.1132950.8513548.8995499.105.12472998.10710845)
Major Version Number=100
Minor Version Number=212.5.29.37: Flags = 0, Length = 16 Enhanced Key Usage Client Authentication (1.3.6.1.5.5.7.3.2) Server Authentication (1.3.6.1.5.5.7.3.1) 2.5.29.15: Flags = 1(Critical), Length = 4 Key Usage Digital Signature, Key Encipherment (a0) 1.3.6.1.4.1.311.21.10: Flags = 0, Length = 1a Application Policies [1]Application Certificate Policy: Policy Identifier=Client Authentication [2]Application Certificate Policy: Policy Identifier=Server Authentication 2.5.29.17: Flags = 0, Length = 51 Subject Alternative Name Other Name: Principal Name=COMPUTER-030651$@subdomain.company.com DNS Name=COMPUTER-030651.subdomain.company.com 2.5.29.14: Flags = 0, Length = 16 Subject Key Identifier 65 2c 42 98 58 58 40 e5 66 58 a3 b8 b4 9a 58 f3 16 0f 8d 42 2.5.29.35: Flags = 0, Length = 18 Authority Key Identifier KeyID=26 12 4b e0 48 d5 24 6d 4d f9 75 25 db 16 1c 27 ee 01 68 2e 2.5.29.31: Flags = 0, Length = 110 CRL Distribution Points [1]CRL Distribution Point Distribution Point Name: Full Name: URL=ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=SFRCRBPKI002VM,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint (ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=SFRCRBPKI002VM,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint) URL=http://crl.subdomain.company.com/CertEnroll/SUBDOMAIN-ISSUING-CA.crl 1.3.6.1.5.5.7.1.1: Flags = 0, Length = 132 Authority Information Access [1]Authority Info Access Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2) Alternative Name: URL=ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?cACertificate?base?objectClass=certificationAuthority (ldap:///CN=SUBDOMAIN-ISSUING-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=subdomain,DC=company,DC=com?cACertificate?base?objectClass=certificationAuthority) [2]Authority Info Access Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2) Alternative Name: URL=http://crl.subdomain.company.com/CertEnroll/SUBDOMAIN-ISSUING-CA(1).crt [3]Authority Info Access Access Method=On-line Certificate Status Protocol (1.3.6.1.5.5.7.48.1) Alternative Name: URL=http://ocsp.subdomain.company.com/ocspSignature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 97 49 ed 0f e8 49 c9 59 04 89 80 51 8a f9 9e 0b
0010 7e aa f0 54 71 79 f7 f3 a1 66 95 ea 7c 47 f1 d2
0020 75 06 c0 37 8e c6 bb d0 9e 5c 16 d7 ef e9 86 b1
0030 c9 46 c8 e1 98 07 bf 57 3c 6d 94 38 65 aa 14 1d
0040 2e 05 fd 47 16 17 76 e6 d1 57 34 72 57 14 ea e4
0050 a6 8b 5a 4b 5f 88 c0 44 ca 24 61 0c f0 cb 04 10
0060 cc 50 f4 b8 44 4c 62 b7 64 85 21 fb 5d 54 20 f0
0070 b5 47 0d d6 c4 0b 7e 2b 6d 7d 1f b0 0b 82 f1 cb
0080 b4 86 01 91 4a 53 a3 f5 71 25 d7 32 93 24 54 6a
0090 fc f2 64 09 ee af b3 67 e9 41 70 b9 29 81 d0 c8
00a0 bd 9c dd b7 77 6e 80 29 54 2d cc ab 35 60 ff ec
00b0 b2 9d 5d 33 48 67 f6 00 0b 8a 33 95 5e 65 7e c0
00c0 30 ed ea 3a ee e2 e6 2d 8f f7 78 a5 6f d9 51 c9
00d0 d1 5c b4 a9 59 0b 1a 72 f8 5c 60 ac 0a f8 59 ea
00e0 30 9d 4f d6 e3 27 9b 8a b4 41 a4 f1 d0 32 da 26
00f0 64 de a7 e2 62 9f 58 82 6e c7 7d 79 4d 40 28 24
Non-root Certificate
Key Id Hash(rfc-sha1): 652c4298585840e56658a3b8b49a58f3160f8d42
Key Id Hash(sha1): 370f239247af79544adae17b68b5a2657694be77
Key Id Hash(md5): 75ee2d84b9af68e7ce9e6e3a7d278663
Key Id Hash(sha256): 41ae93f9a38f931b5d201fbd351c638e22f575cb106149e0992177fdab294bc7
Cert Hash(md5): a4a2570578dd440ba1c5fa5f7141bad7
Cert Hash(sha1): 17f29a9842efd0af6faf642d44afa3a4f8a76378
Cert Hash(sha256): 788296fd65bb3558049fb961362659ae2f3063075eb1c1188d203e8404599017
Signature Hash: 7a286ea9f8bb7cfb50e6ed36caaf40b1b86f76ad9fc6193f585e2c5e2d7336daCERT_SHA1_HASH_PROP_ID(3):
17f29a9842efd0af6faf642d44afa3a4f8a76378CERT_SUBJECT_PUBLIC_KEY_MD5_HASH_PROP_ID(25):
75ee2d84b9af68e7ce9e6e3a7d278663CERT_MD5_HASH_PROP_ID(4):
a4a2570578dd440ba1c5fa5f7141bad7CERT_SIGNATURE_HASH_PROP_ID(15) disallowedHash:
7a286ea9f8bb7cfb50e6ed36caaf40b1b86f76ad9fc6193f585e2c5e2d7336daCERT_KEY_IDENTIFIER_PROP_ID(20):
652c4298585840e56658a3b8b49a58f3160f8d42CERT_SUBJECT_PUB_KEY_BIT_LENGTH_PROP_ID(92):
0x00000800 (2048)CERT_ISSUER_PUBLIC_KEY_MD5_HASH_PROP_ID(24):
7fccd905eb9b7c4f87cd303e3286409eCERT_OCSP_CACHE_PREFIX_PROP_ID(75):
F9E78C401BCA2A15567C2C8E0036C159_CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = 185b3e683d848c978d87b2ce5a0dcc06_0fe860f7-1d2f-4ee4-b732-53cd6fa9bce1
Provider = Microsoft RSA SChannel Cryptographic Provider
ProviderType = c
Flags = 20 (32)
CRYPT_MACHINE_KEYSET -- 20 (32)
KeySpec = 1 -- AT_KEYEXCHANGECERT_CEP_PROP_ID(87):
Enrollment Policy Url: ldap:
Enrollment Policy Id: {EE1464EB-310F-4070-B71E-DDC3835A498F}
Enrollment Server Url: SFRCRBPKI002VM.subdomain.company.com\SUBDOMAIN-ISSUING-CA
Request Id: 1064824
Flags = 0
DefaultNone -- 0
Url Flags = 0
Authentication = 2
Kerberos -- 2
Enrollment Server Authentication = 2
Kerberos -- 2CERT_REQUEST_ORIGINATOR_PROP_ID(71):
COMPUTER-030651.subdomain.company.comCERT_ACCESS_STATE_PROP_ID(14):
AccessState = 6
CERT_ACCESS_STATE_SYSTEM_STORE_FLAG -- 2
CERT_ACCESS_STATE_LM_SYSTEM_STORE_FLAG -- 4Missing stored keyset
CertUtil: -store command completed successfully.
This is also happening on Checkpoint Endpoint VPN client. It may eventually happen after the user changed their domain account password. If the certificate is re-imported it will work.
https://support.checkpoint.com/results/sk/sk178727
Greetings
Sorry for my late reply. We circumvented the issue by writing a script that requests a new certificate if the computer is connected to the corporate network... on each system startup. We were not able to solve the issue but the workaround does the trick.
FYI, we use Crowdstrike as AV and Pulse Secure as our VPN solution.