Hi @Blue Tongue • Thank you for reaching out.
When you run the Get-AzureADAuditSignInLogs cmdlet, in the background it runs https://graph.microsoft.com/beta/auditLogs/signIns graph call and Azure AD actually returns the userAgent but it is not displayed in the output of the command. You can use the below PowerShell script to get this value:
Prerequisites:
- Navigate to Azure AD > App Registration > Register new app and copy the ClientID.
- Generate a client secret and copy that as well.
- Under Api Permissions blade, add https://graph.microsoft.com/AuditLog.Read.All permission (Application Permission, not delegated) and grant admin consent.
Below is how the output looks like:$ApplicationID = "Paste client ID from step1" $TenatDomainName = "YOUR_TENANT.onmicrosoft.com" $AccessSecret = 'Paste client secret from step2' $Body = @{ Grant_Type = "client_credentials" Scope = "https://graph.microsoft.com/.default" client_Id = $ApplicationID Client_Secret = $AccessSecret } $ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenatDomainName/oauth2/v2.0/token" ` -Method POST -Body $Body $token = $ConnectGraph.access_token $GraphUrl = "https://graph.microsoft.com/beta/auditLogs/signIns" Invoke-RestMethod -Headers @{Authorization = "Bearer $($token)"} -ContentType "application/json" -Uri $GraphUrl -Method Get | select -ExpandProperty value | Where-Object {$_.UserDisplayName -eq "YOUR_USER_DISPLAY_NAME"} | fl CreatedDateTime, UserDisplayName, userAgent
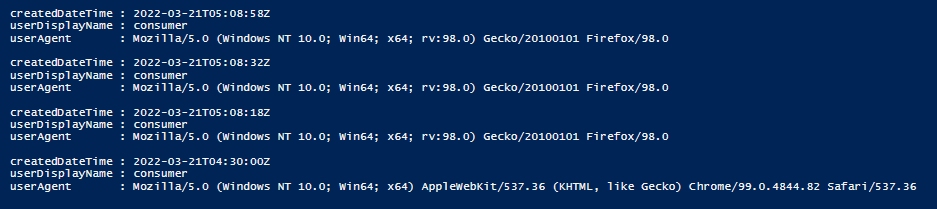
Note: This script is using Client_credentials flow that utilizes application context to fetch the logs and not the user context. You can customize the script as per your requirement. E.g., you can remove Where-Object parameter to get a list of activities for all users.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.