Hi mohamedelashkr-4024,
how will the Hub VM route the traffic to AZFW2 then to AZFW1 and then to TEST VM(there are to Stations FWs in between)? and how would you configure both Az-FWs so that the traffic is working well between them?
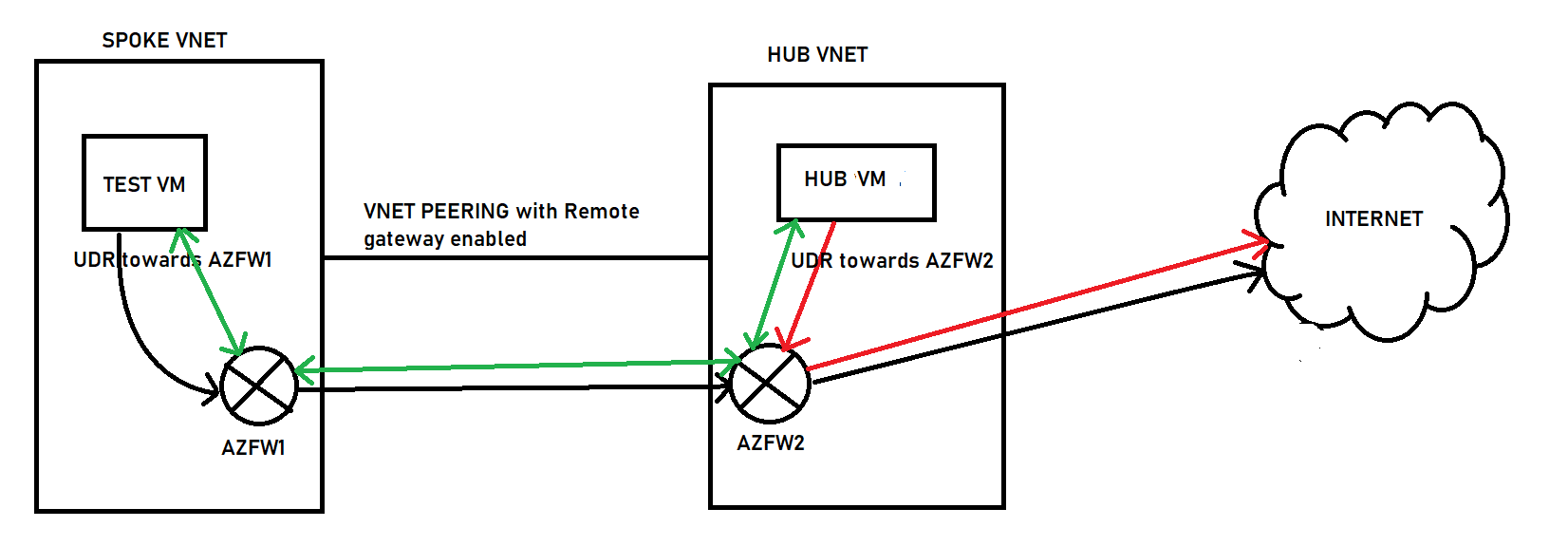
In my lab environment, I have 2 AZFW's (SKU: standard with firewall policy - force tunnel enabled).
Traffic flow: Test VM -> AZFW1 -> AZFW2 -> Hub VM
The subnet of the test VM contains a UDR for the hub VM, which points to AZFW1. The NSG rule allows traffic to reach the hub VM
AZFW1 has 2 subnets : AzureFirewallSubnet and AzureFirewallManagementSubnet. A UDR is attached (for HUB VM address prefix) to AzureFirewallSubnet, which points to AZFW2 (there is no UDR attached to AzureFirewallManagementSubnet). This traffic is allowed by AZFW1's network rule.
AZFW2 has 2 subnets: AzureFirewallSubnet and AzureFirewallManagementSubnet. There is a UDR attached to AzureFirewallSubnet (Test VM address prefix) which forwards traffic to AZFW1. This traffic is allowed by AZFW2's network rule.
This traffic is directed towards AZFW2 by the UDR on Hub VM, and it is allowed by the NSG rule.
I hope this helps. You can follow this article if you would like to keep the application gateway behind the AZFW.
https://learn.microsoft.com/en-us/azure/architecture/example-scenario/gateway/firewall-application-gateway