Hi @Alex Rourke • Thank you for providing the required information.
Looking at the details at our backend, I found that your Ba*****a Ne****s app calls the Windows Azure Active Directory Graph resource (App ID 00000002-0000-0000-c000-000000000000), and a policy that requires MFA is getting applied to this resource.
As the "All User MFA" policy includes all applications, the app 00000002-0000-0000-c000-000000000000 is also getting protected by this policy and is requiring MFA when this app is called.
Now, the challenge is, that this app doesn't get listed in the conditional access policy. So there is no easy solution to this problem i.e., excluding this app from the "All User MFA" Policy. To get it working without changing any other conditions of your CA policy, you need to explicitly specify the applications that you want to include in the CA Policy rather than including all cloud apps.
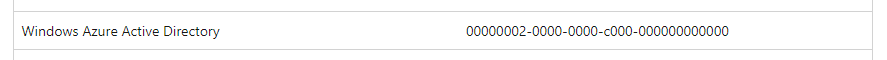
Ref: Application IDs for commonly used Microsoft applications
Hope this helps.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.

