We have a client using Azure as there SSO provider. My organization currently uses Ping Federate as our SSO provider. We own multiple internal applications which are SSO enabled.
We currently have a single connection setup on our end and a enterprise application on the client which is working properly. They are using SP-initiated flow to login to our application with no issues.
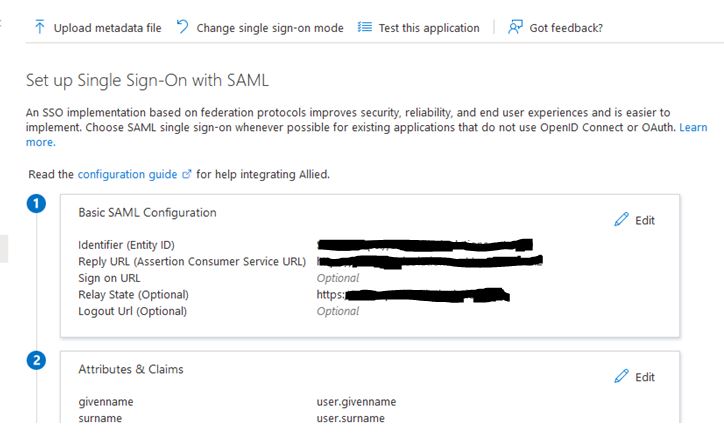
We are now migrating another one of our applications from the clients previous sso provider to Azure SSO. on our end we normally just add the additional Application Adapter to the existing connection. We are now running into an issue because we only have a single Entity ID and ACS. Is there a way for them to configure the existing connection to also include this additional application with the same entity ID and ACS.
I have seen cases were organizations use Rely state or Redirect URI. I'm not sure how that would be configured. I know this is possible because we have other more mature clients which have implemented this with no issue using Azure SSO.
Application one:
EntityID: SAML2:https://auth.organziation.com:443
ACS: https://auth.organziation.com/sp/ACS.saml2
Application url: https://application1.organziation.com
Application two:
EntityID: SAML2:https://auth.organziation.com:443
ACS: https://auth.organziation.com/sp/ACS.saml2
Application url: https://application2.organziation.com
I can provide more information as it's requested.