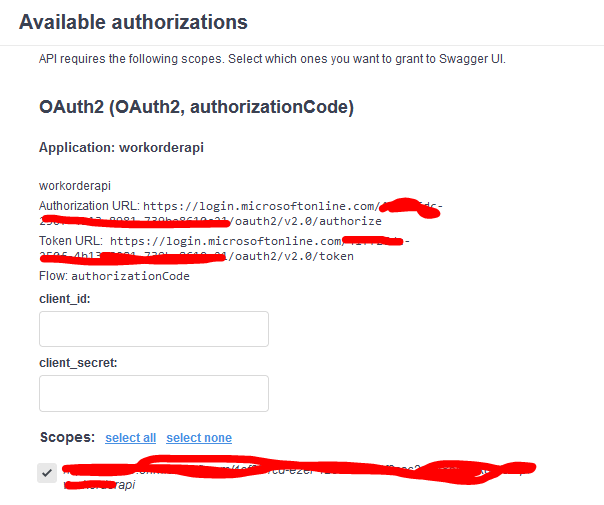
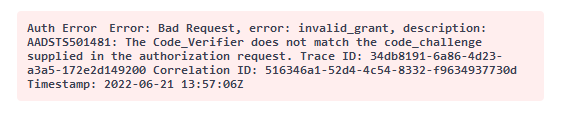
Hello @Pinkesh Dashrathbhai Patel , the AADSTS501481 error is cause the /token post_verifier param value not matching the /authorize code_challenge param value.
This is not an Azure AD limitation but an error coming from the calling client. Immediate recommendation is to do a fiddler trace to see what the values are being generated and ensuring none of them is not being cached.
Azure AD App Registration Redirect URL must follow the actual application type: SPA or Web App.
In case it is a Web App and as a temporary workaround you might enable Authorization Grant without PKCE. Configuration should be similar to this:
components:
schemas: {}
securitySchemes:
accessCode:
type: oauth2
flows:
authorizationCode:
authorizationUrl: 'https://login.microsoftonline.com/common/oauth2/v2.0/authorize'
tokenUrl: 'https://login.microsoftonline.com/common/oauth2/v2.0/token'
scopes:
'api://<READ SCOPE RESOURCE ID>/read': allows reading resources
Let us know if this answer was helpful to you or if you need additional assistance. If it was helpful, please remember to accept it so that others in the community with similar questions can more easily find a solution.