Hello BangMirae807ExternMirae-9981,
Thank you for posting here.
Hope the information provided by BangMirae807ExternMirae-9981 is helpful.
Here I add some information.
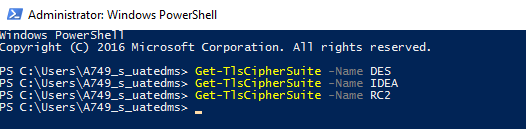
From the screenshot you provided, I did not see you have DES cipher. Based on "however, still detected." How did you detect it/them?
Here I can see DES cipher in my lab.
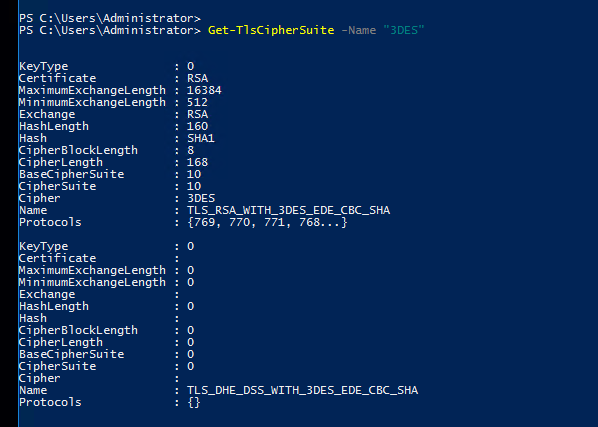
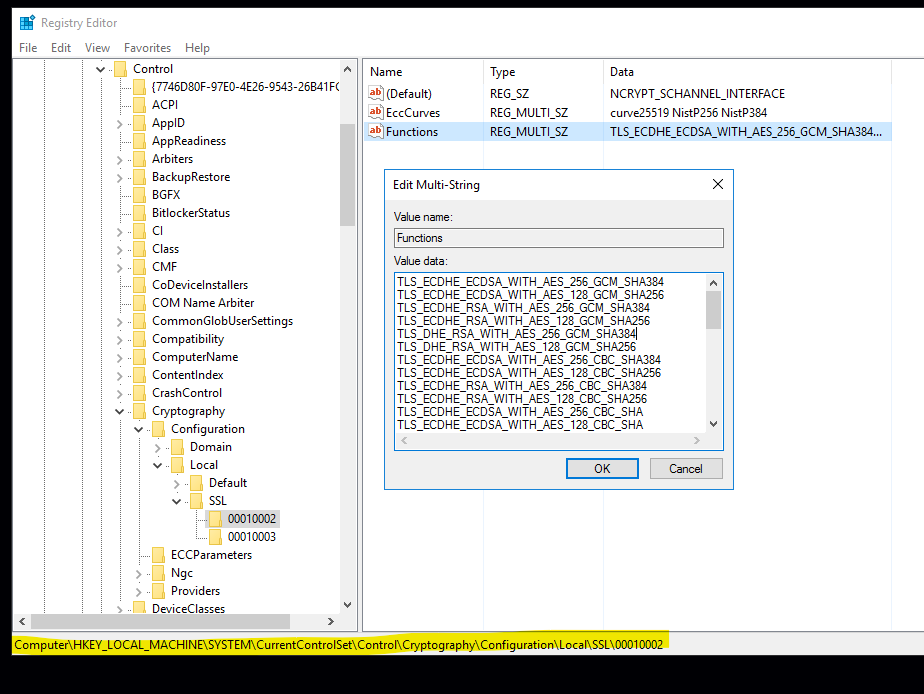
You can remove the DES ciphers if needed through registry as below.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002
Reference
Managing SSL/TLS Protocols and Cipher Suites for AD FS
https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/operations/manage-ssl-protocols-in-ad-fs
Note: For system security, please back up the registry before modifying the registry.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.

 ]
]


