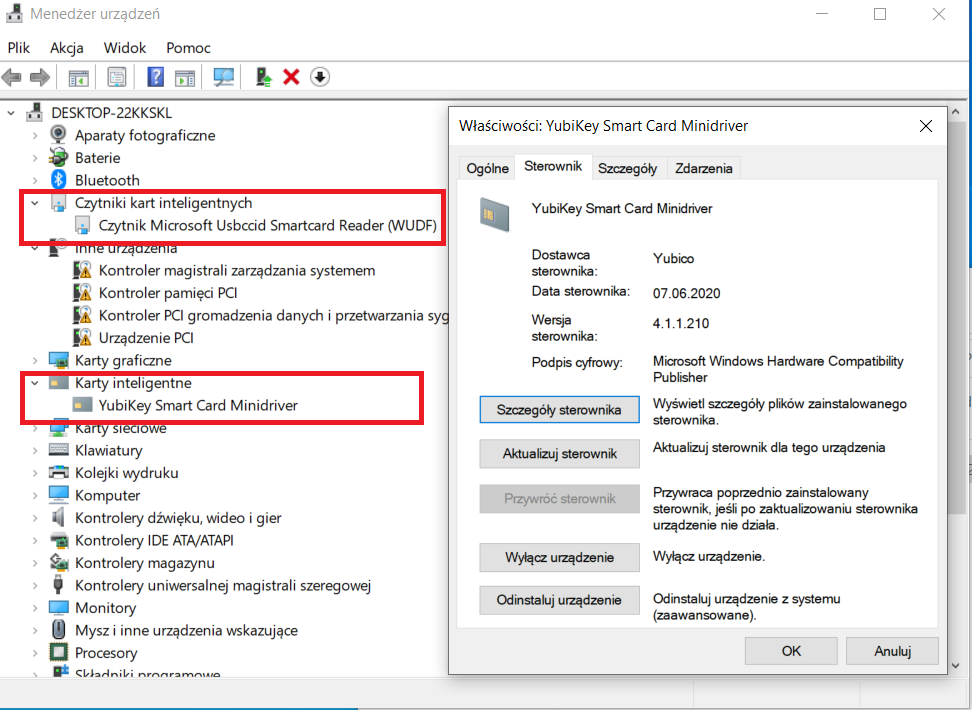
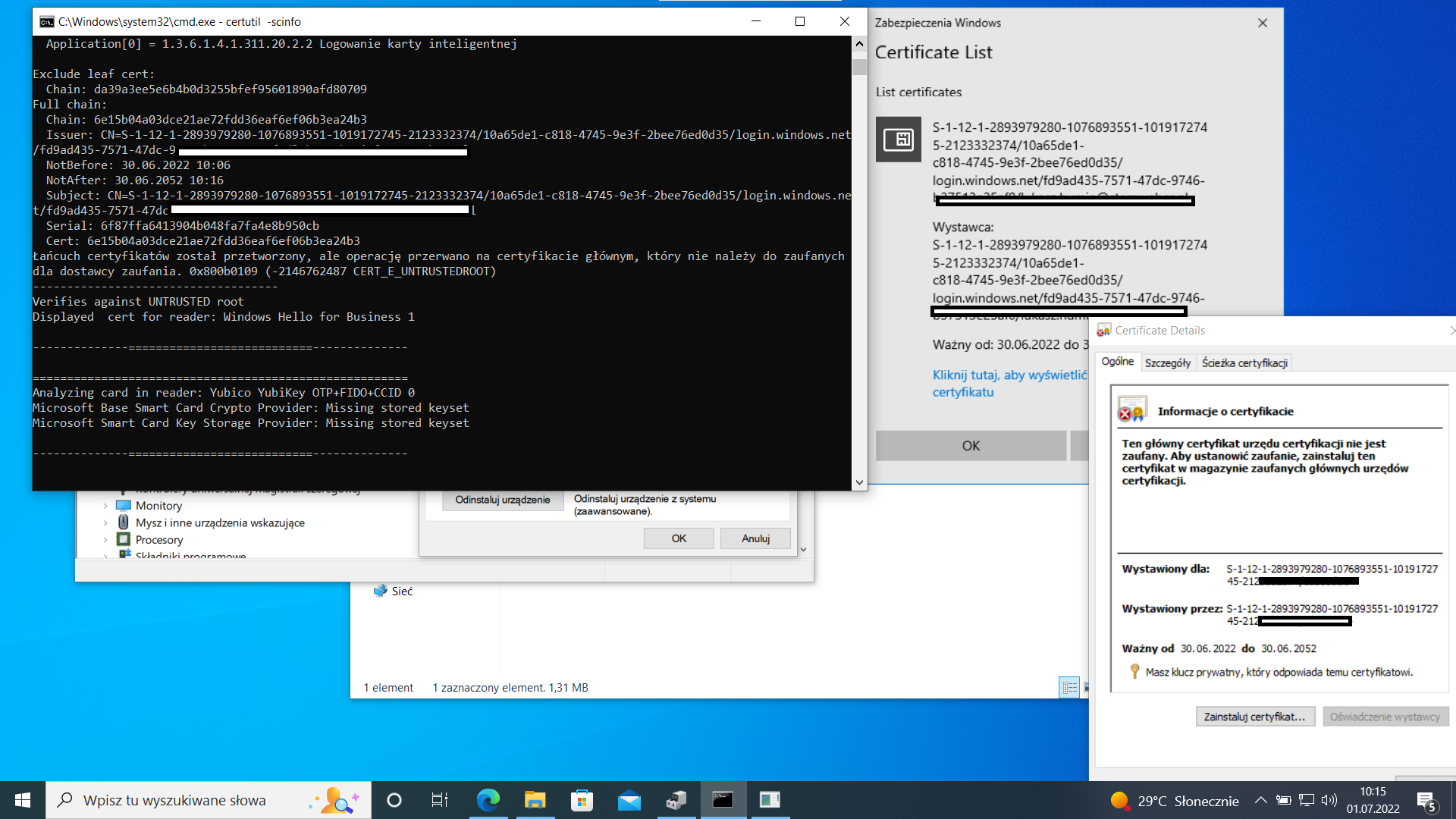
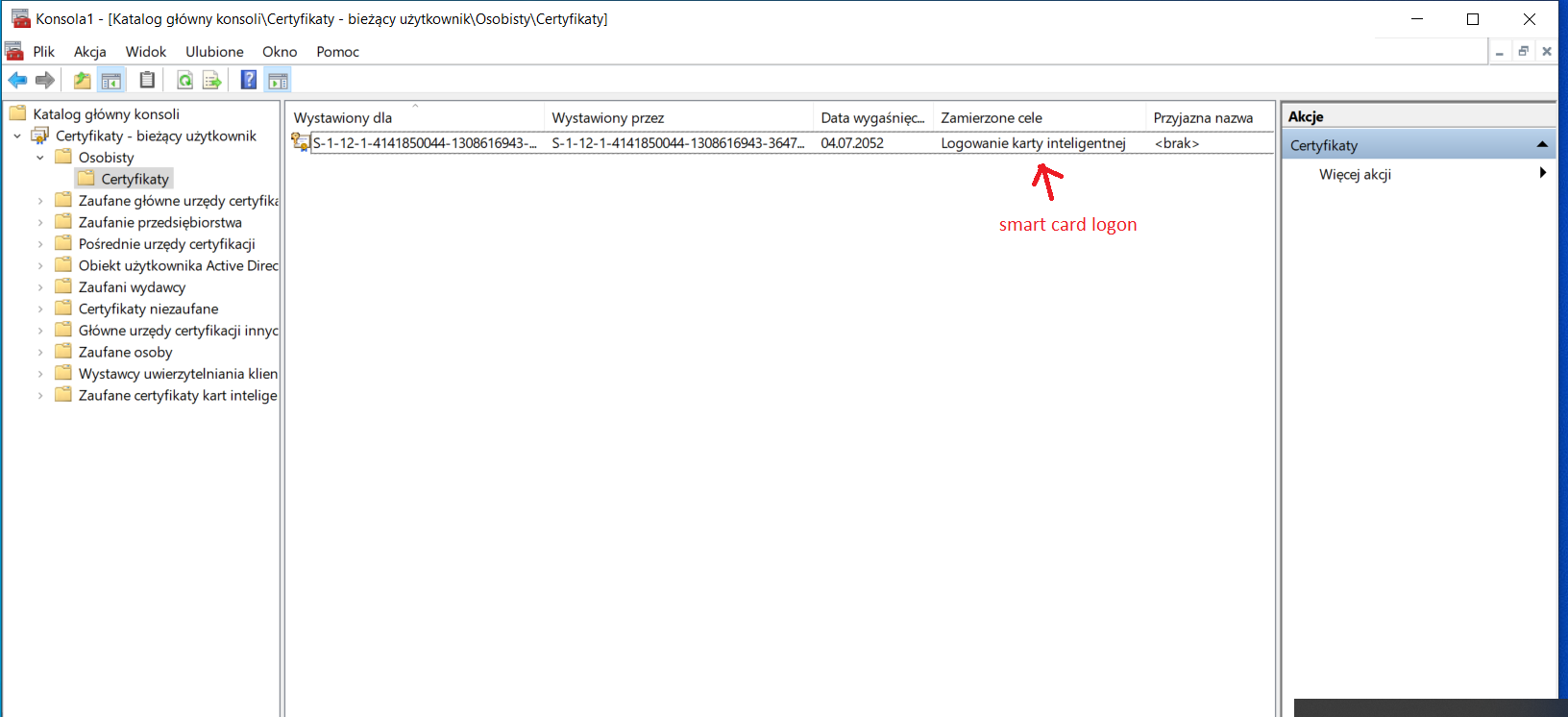
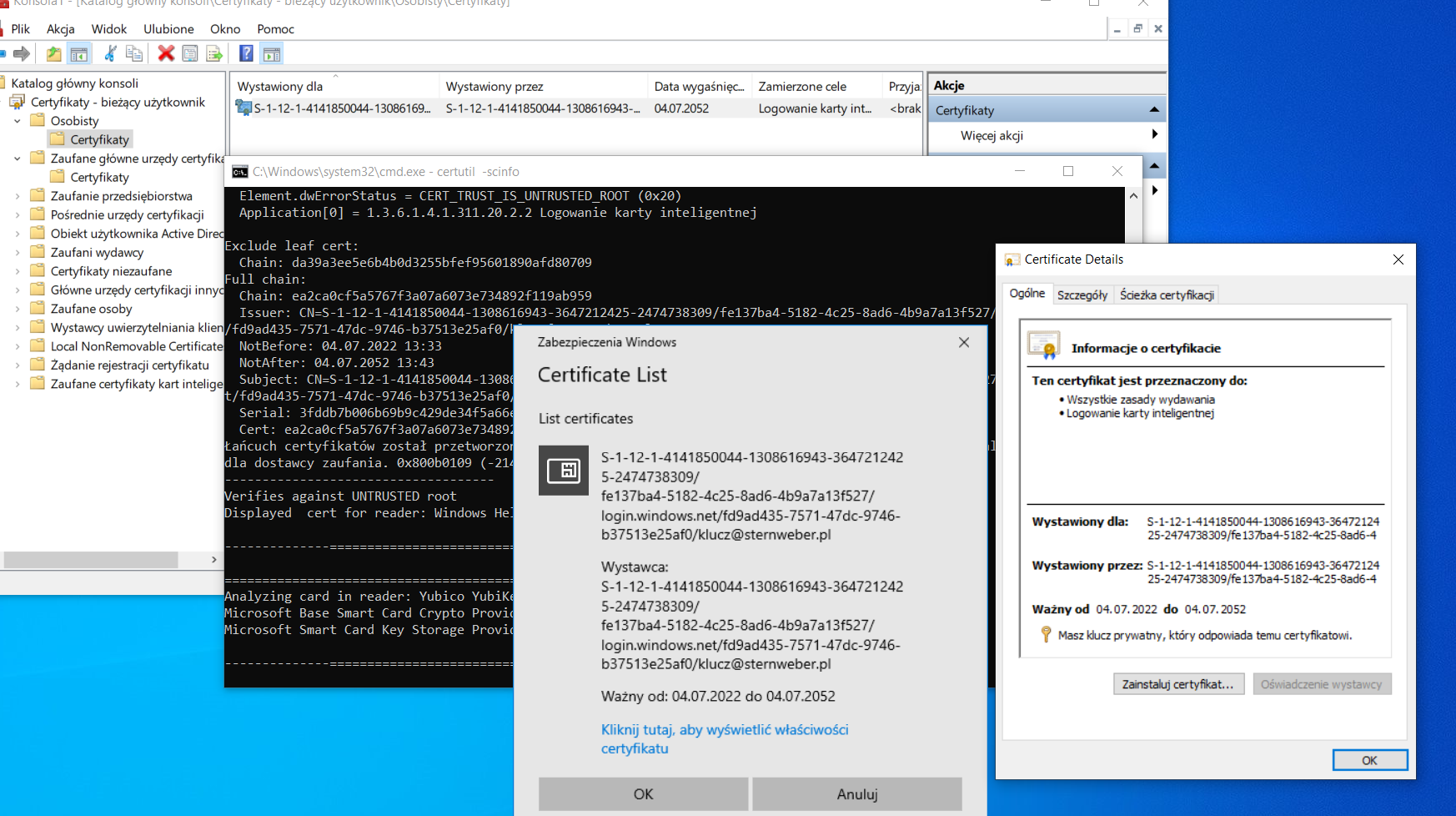
In your case , I understand that you are trying to logon to a windows 10 machine using Yubikey and have setup the Security Key as a valid authentication method in the users profile and on the portal . We have seen this error occuring if you do not have YubiKey drivers installed on the windows 10 box and are using any other driver or Microsoft provided general driver which helps read the smartcard. The issue mostly in this case would be that the driver is not able to read the smartcard for the certificates. In order to rule this out , could you please go to the device manager on windows box . Go to the startmenu and press the windows key -> Start > type devmgmt.msc and check the Smart card readers section . In my windows 10 machine it shows as below because I use a different smartcard. Ideally Windows update should automatically download the YubiKey smartcard driver but sometimes it may not happen.
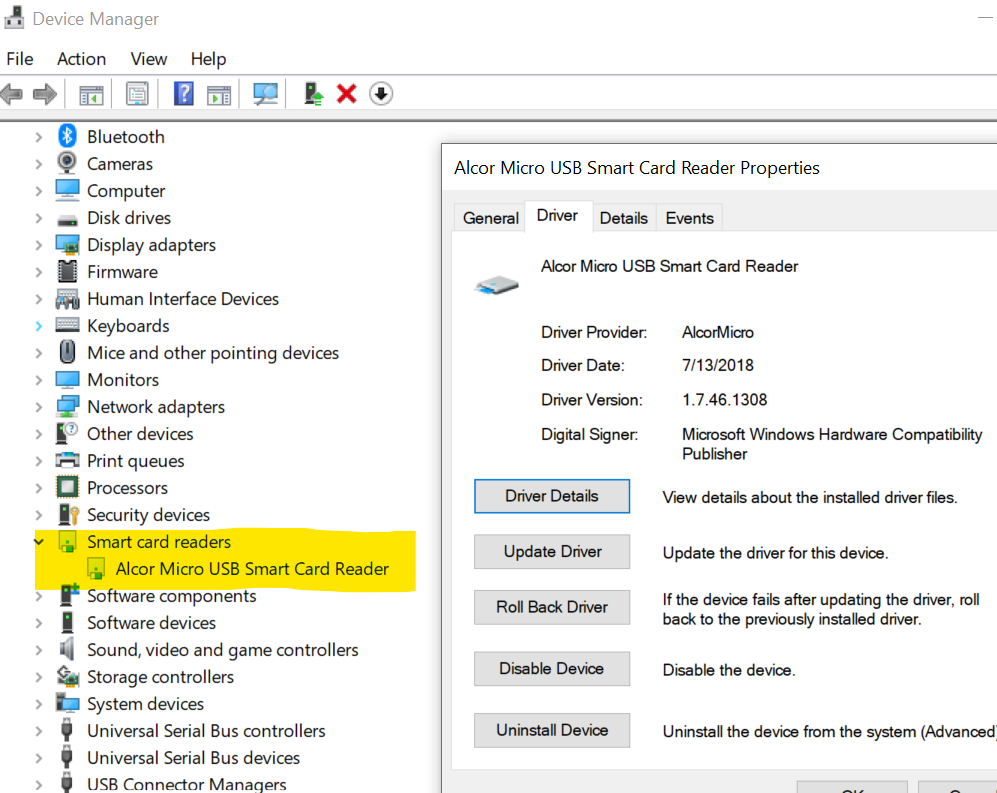
Similarly you should see Yubikey's drivers. Macke sure you are not using generic Microsoft Drivers. If you do not have Yubikey drivers then you can download the tools here . I would recommend you to also go through the article about how to go about installation of the driver.
If you are in a environment where your machine is in on-premise active directory and you have an internal PKI infrastructure then you will need to get your Yubikey a certificate issued from your corporate PKI server. Some functions may need intervention of your company IT admins if this is not a lab environment where you are trying this. You may manually import a certificate to the Yubikey .
I believe you have already enabled passwordless authentication using security key however I would still request you to verify it as per the article Passwordless security key sign-in - Azure Active Directory .
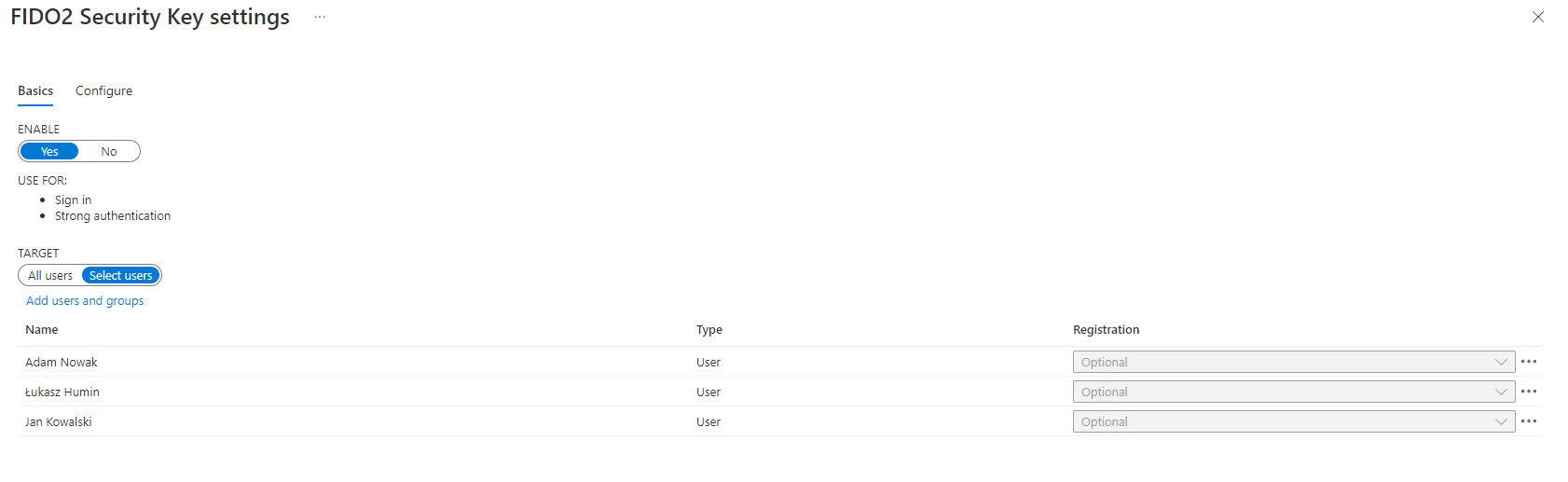
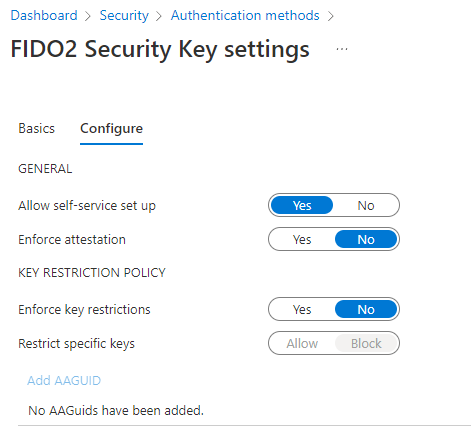
You could do that by going to Azure Active Directory > Security > Authentication methods > Authentication method policy. Under the method FIDO2 Security Key, choose the following options:
Enable - Yes or No
Target - All users or Select users
Save the configuration.
If you see an error when you try to save, the cause might be due to the number of users or groups being added. As a workaround, replace the users and groups you are trying to add with a single group, in the same operation, and then click Save again.
In case your machine is an on-premise machine please follow the prerequisite section of the article Enabling passwordless authentication using Security key for on-premise windows 10 machines. Out of all the unsupported scenarios in the above linked article, in your case I don't think any of it applies yet I have added it for reference. As mentioned in the article , the following scenarios aren't supported :
- Windows Server Active Directory Domain Services (AD DS)-joined (on-premises only devices) deployment.
- Remote Desktop Protocol (RDP), virtual desktop infrastructure (VDI), and Citrix scenarios by using a security key.
- S/MIME by using a security key.
- Run as by using a security key.
- Log in to a server by using a security key.
I hope the information is helpful in troubleshooting your issue. In case I have misunderstood your scenario or none of the solution works for you , please do let us know your findings in comments and we will continue to help you further. However, If the information is helpful , please do share what worked and do accept the post as answer which will help improve the discoverability of this thread for other members of the community searching for similar answers.
Thank you.
----------------------------------------------------------------------------------------------------------------------------------------------------------
- Please don't forget to click on
 whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators
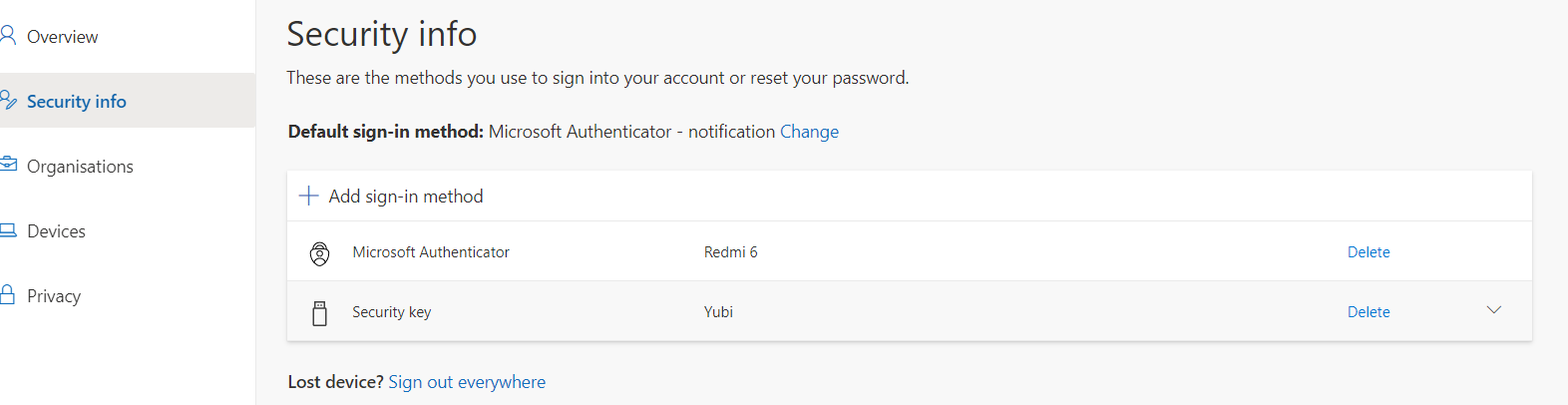
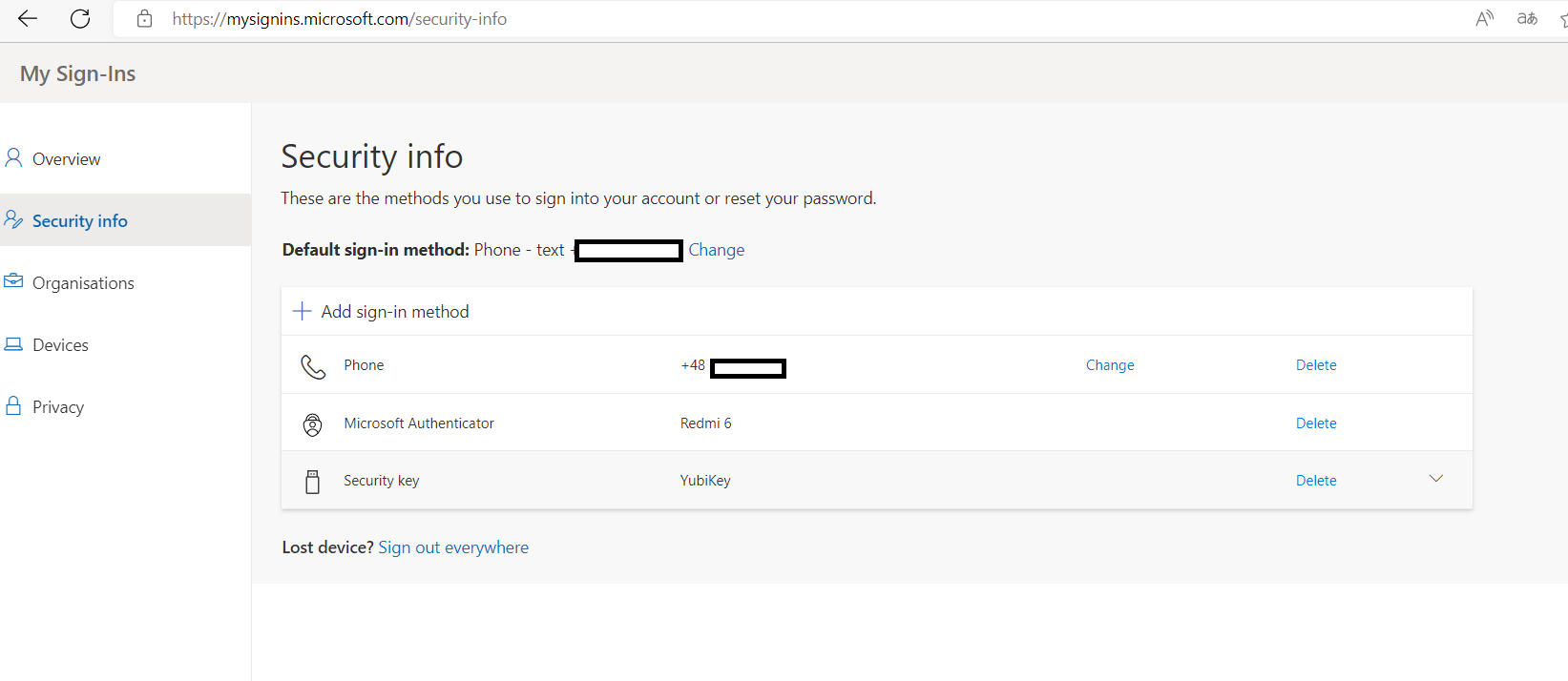
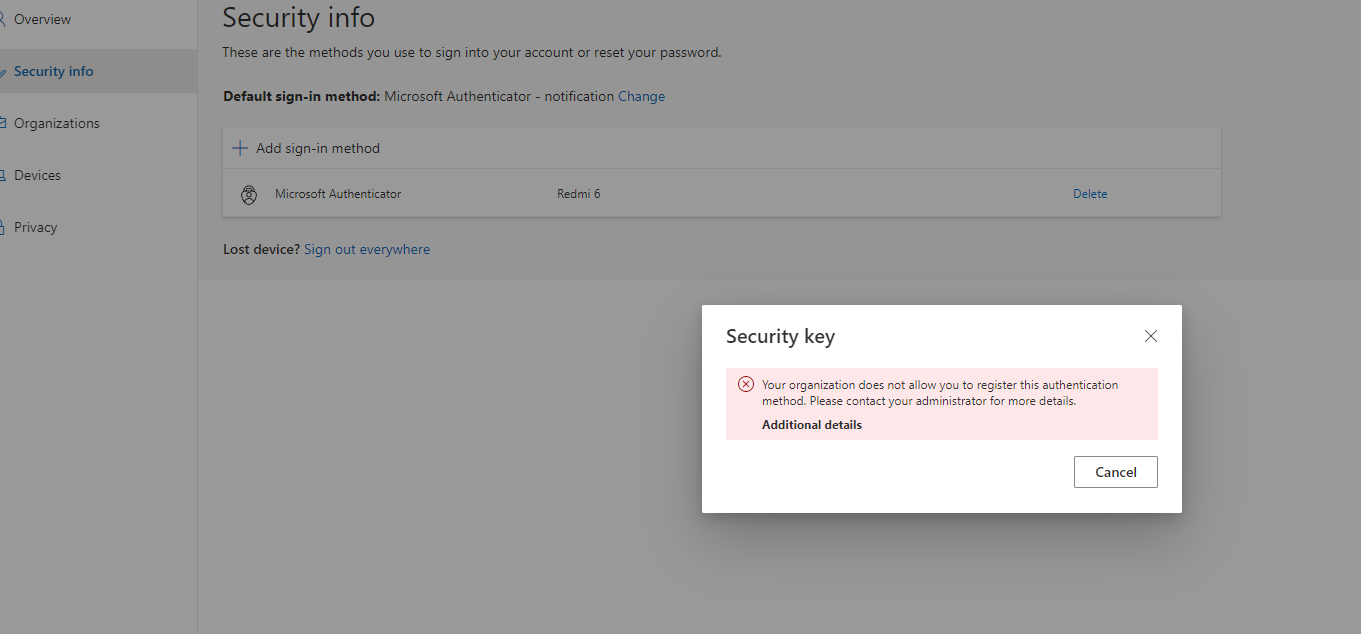
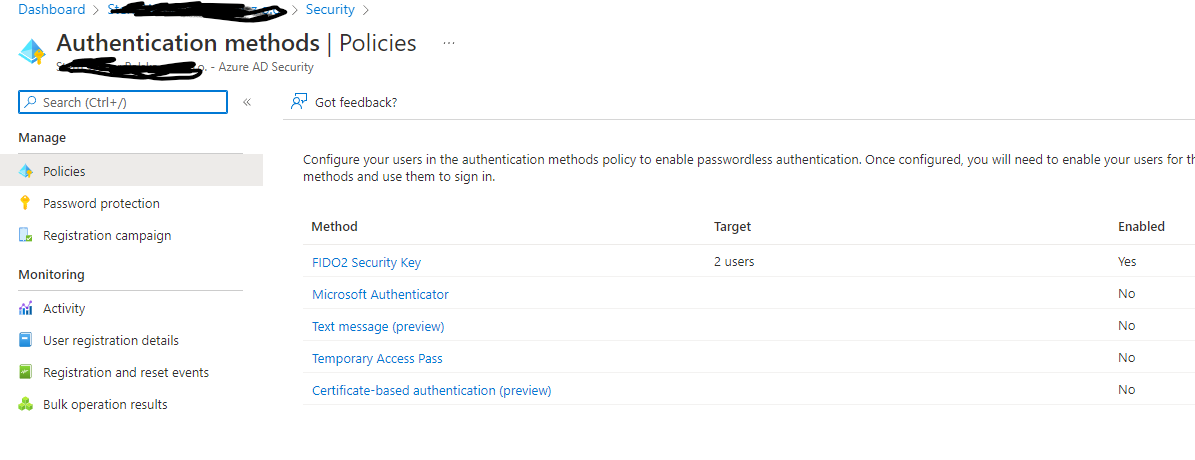 , and successfully added a Yubikey to one account on myprofile.microsoft.com
, and successfully added a Yubikey to one account on myprofile.microsoft.com