Failing at the final hurdle when running IaC deployments for Logics Apps (Standard).
I have a standard logic app where a number of work flows have a 'Get secret' task from a key vault. The following is true of the setup:
- The logic app, key vault and the key vault API connector are in the same resource group
- The logic app is a contributor in the resource group
- The logic app has access policies for Get, List and Set in the key vault.
As I am just working this out, I am currently deploying:
- The logic app using the logic app extension through VSCode. The connections.json file has the correct connectionRuntimeURL as the logic app:
connections.json:
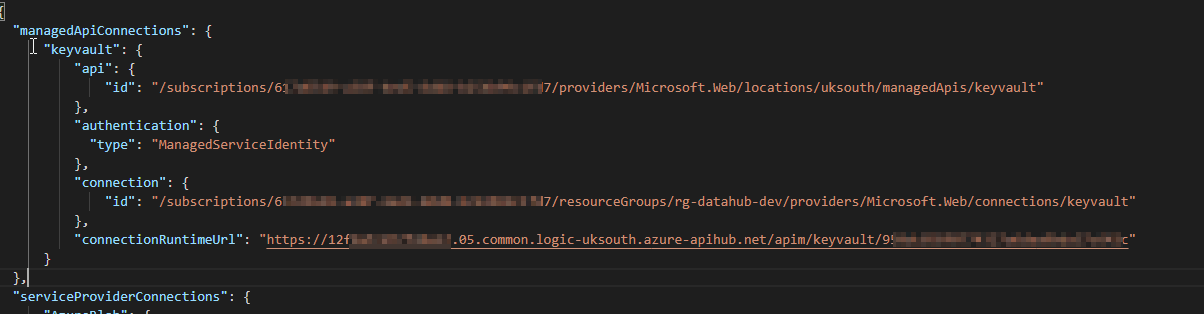 ]2
]2
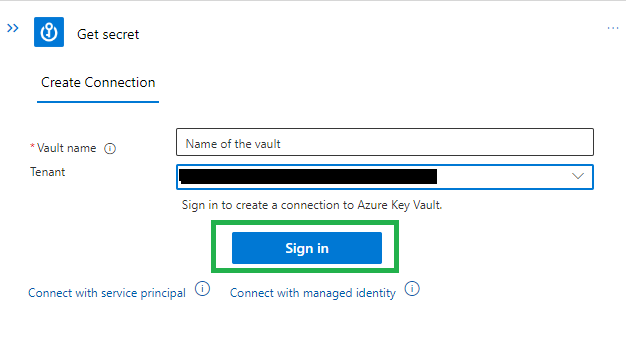
Screen shot connection UI in protal:
After deploying the app through VSCode, I think run a manual ARM template deployment through the UI for the connection.
Here is the template (with some name redcations):
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"logicAppSystemAssignedIdentityTenantId": {
"defaultValue": "14xxxxxxxxxxxxxxxxxxxxxxxxxxf",
"type": "String"
},
"logicAppSystemAssignedIdentityObjectId": {
"type": "String"
},
"connections_keyvault_name": {
"defaultValue": "keyvault",
"type": "String"
},
"keyvault_name": {
"defaultValue": "kv-datahub-dev",
"type": "String"
},
"location": {
"defaultValue": "uksouth",
"type": "String"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.Web/connections",
"apiVersion": "2016-06-01",
"name": "[parameters('connections_keyvault_name')]",
"location": "[parameters('location')]",
"kind": "V2",
"properties": {
"displayName": "hub-key-vault",
"statuses": [
{
"status": "Ready"
}
],
"parameterValueType": "Alternative",
"alternativeParameterValues": {
"vaultName": "[parameters('keyvault_name')]"
},
"createdTime": "2022-07-01T14:08:48.8022575Z",
"changedTime": "2022-07-01T15:12:36.3050611Z",
"api": {
"name": "[parameters('connections_keyvault_name')]",
"displayName": "Azure Key Vault",
"description": "Azure Key Vault is a service to securely store and access secrets.",
"iconUri": "[concat('https://connectoricons-prod.azureedge.net/releases/v1.0.1574/1.0.1574.2782/', parameters('connections_keyvault_name'), '/icon.png')]",
"brandColor": "#0079d6",
"id": "[concat('/subscriptions/6xxxxxxxxxxxxxxxxxxxxxxx7/providers/Microsoft.Web/locations/uksouth/managedApis/', parameters('connections_keyvault_name'))]",
"type": "Microsoft.Web/locations/managedApis"
},
"testLinks": []
}
},
{
"type": "Microsoft.Web/connections/accessPolicies",
"apiVersion": "2016-06-01",
"name": "[concat(parameters('connections_keyvault_name'),'/',parameters('logicAppSystemAssignedIdentityObjectId'))]",
"location": "[parameters('location')]",
"dependsOn": [
"[resourceId('Microsoft.Web/connections', parameters('connections_keyvault_name'))]"
],
"properties": {
"principal": {
"type": "ActiveDirectory",
"identity": {
"tenantId": "[parameters('logicAppSystemAssignedIdentityTenantId')]",
"objectId": "[parameters('logicAppSystemAssignedIdentityObjectId')]"
}
}
}
}
]
}
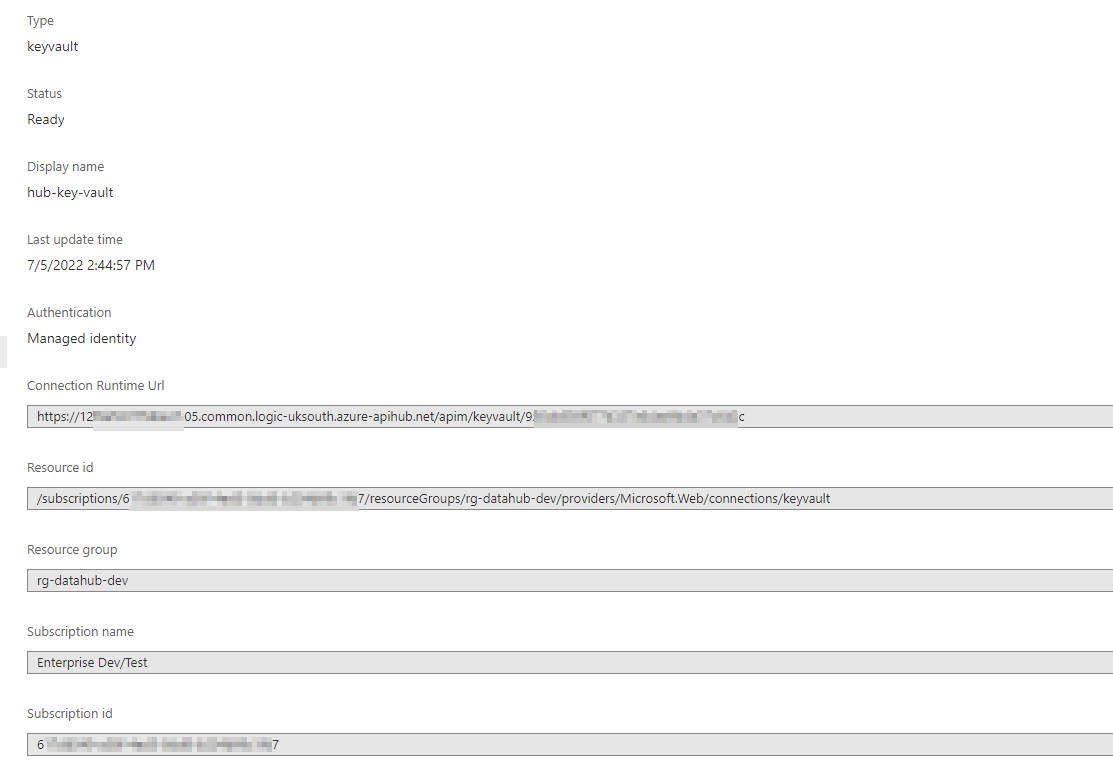
After deployment, the connection is showing as connected:
 ]5
]5
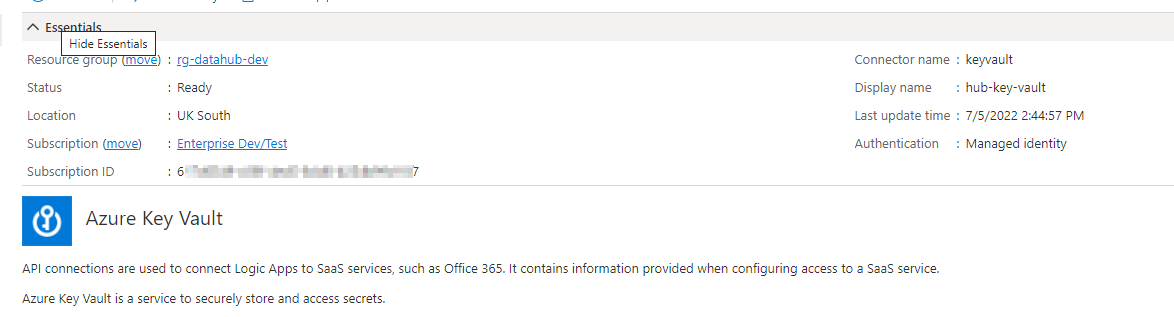
Any the authorisation correctly showing Managed Identity (again, the logic app has been granted access to the key vault & access policies in the KV):
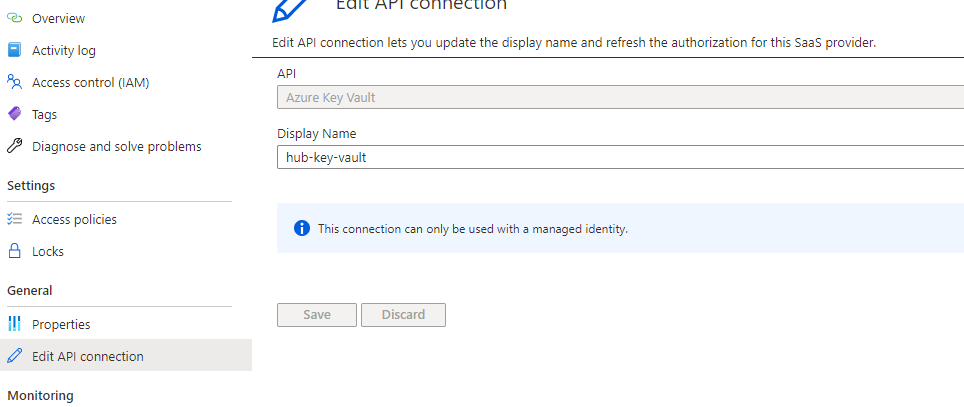
However, in the designer despite showing a valid API connection, no secrets are listed:
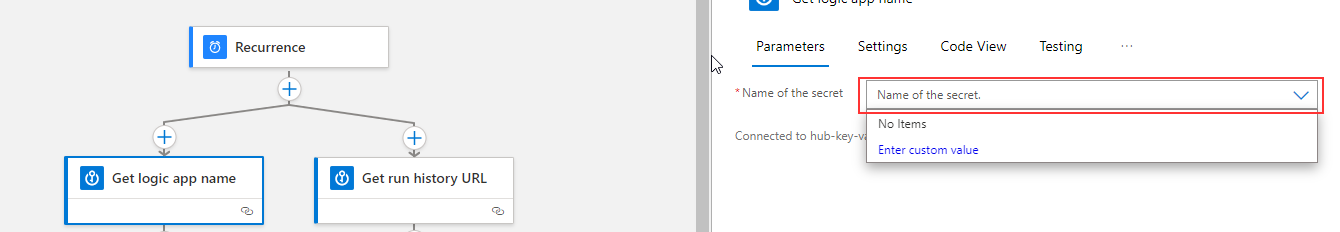
When running a test of the workflow, the error generated refers to a missing access token.
{
"status": 401,
"message": "The connection does not contain an access token. Please edit the connection and login.",
"error": {
"message": "The connection does not contain an access token. Please edit the connection and login."
},
"source": "keyvault-uks.azconn-uks-002.p.azurewebsites.net"
}
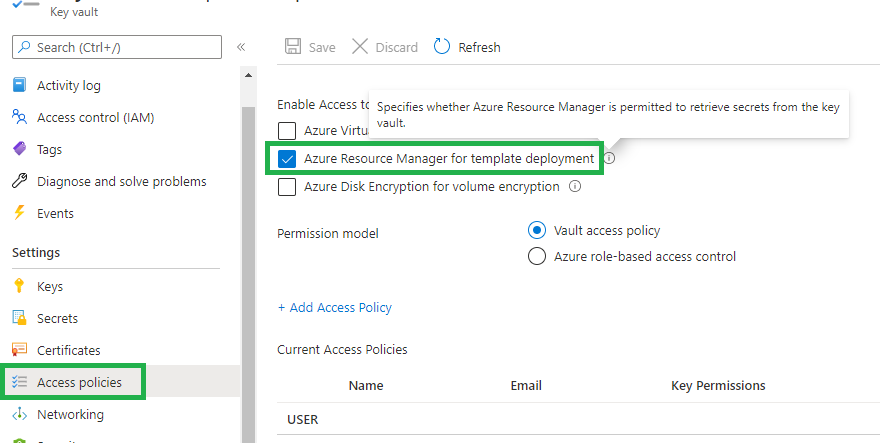
Now given access is granted via Managed Identity, at this point I am stumped and could do with a steer - I imagine it's something in my connections ARM template.

 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is How
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is How  ]
]
 ]
]