Hello @Maitra-v, Anirban ,
Thanks for the question and using MS Q&A platform.
Flat-namespace blob containers don't have real folders, and don't support file or folder-level security. If you create a storage account with a Hierarchical namespace you gain the ability to grant file and folder-level ACLs for Azure Active Directory principals.
Note: Shared Key and SAS authorization grants access to a user (or application) without requiring them to have an identity in Azure Active Directory (Azure AD). With these two forms of authentication, Azure RBAC and ACLs have no effect.
Azure RBAC and ACL both require the user (or application) to have an identity in Azure AD. Azure RBAC lets you grant "coarse-grain" access to storage account data, such as read or write access to all of the data in a storage account, while ACLs let you grant "fine-grained" access, such as write access to a specific directory or file.
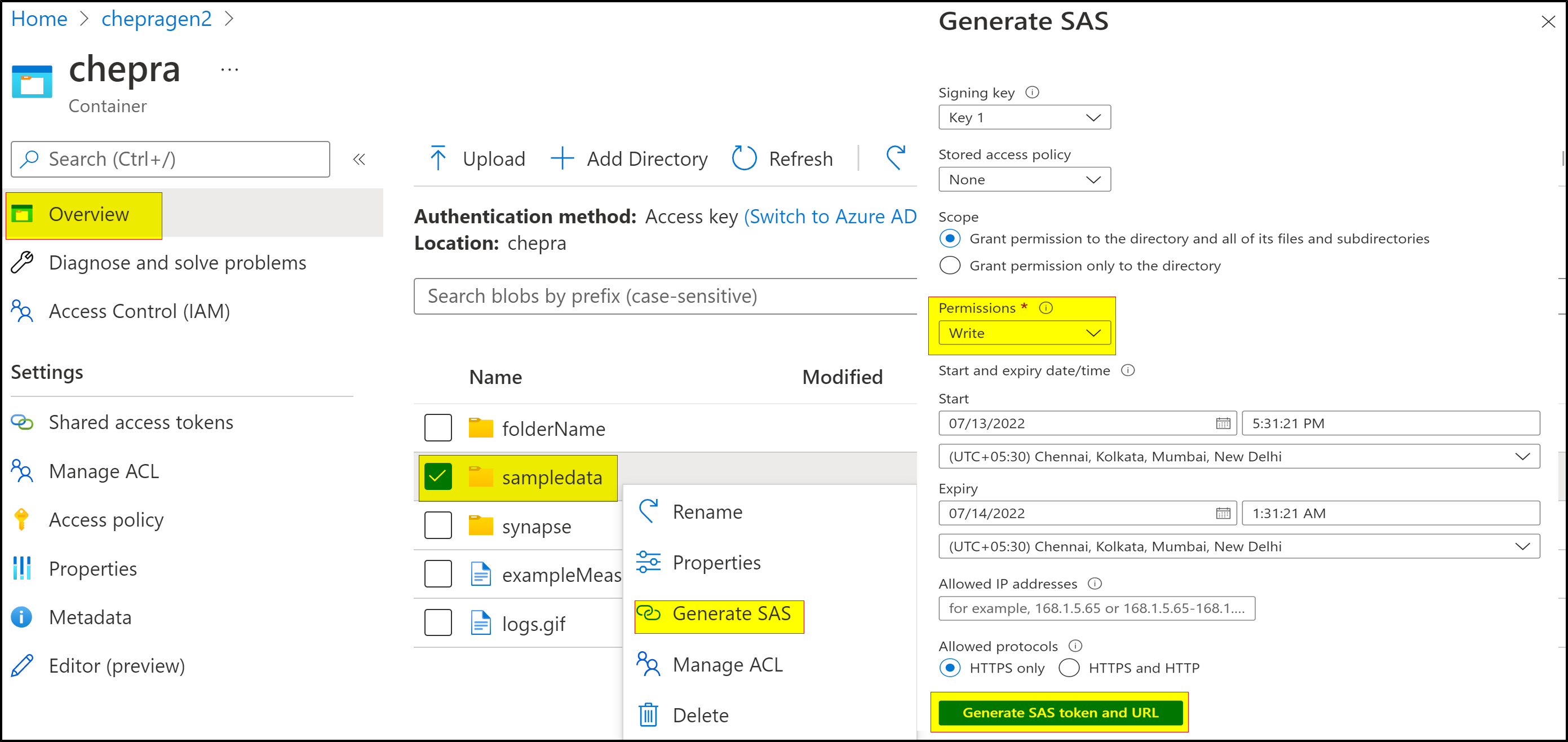
This article - Access control model in Azure Data Lake Storage Gen2 focuses on Azure RBAC and ACLs, and how the system evaluates them together to make authorization decisions for storage account resources.
Hope this will help. Please let us know if any further queries.
------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators
