Hi @Anonymous • Thank you for reaching out.
Refresh tokens issued to SPAs cannot be controlled via B2C Sessions Management and are valid for 24 hours only. So, in your case, you need to make sure that the offline_access scope is not present in the authentication request to make sure the refresh token is not issued.
As documented under Security implications of refresh tokens in the browser, Without refresh tokens or third-party cookies, the authorization code flow (as recommended by the OAuth security best current practices draft) becomes onerous when new or additional tokens are required. A full page redirect or popup is needed for every single token, every time a token expires (every hour usually, for the Microsoft identity platform tokens).
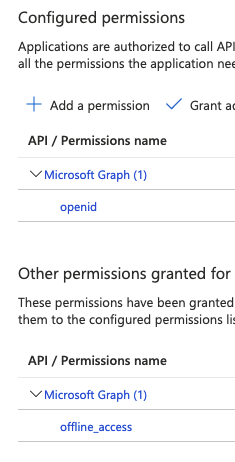
Please check if you have added the offline_access scope for the application registered in the Azure AD B2C tenant. If it is added and consented as shown below, try removing the permission and send the authentication request again.
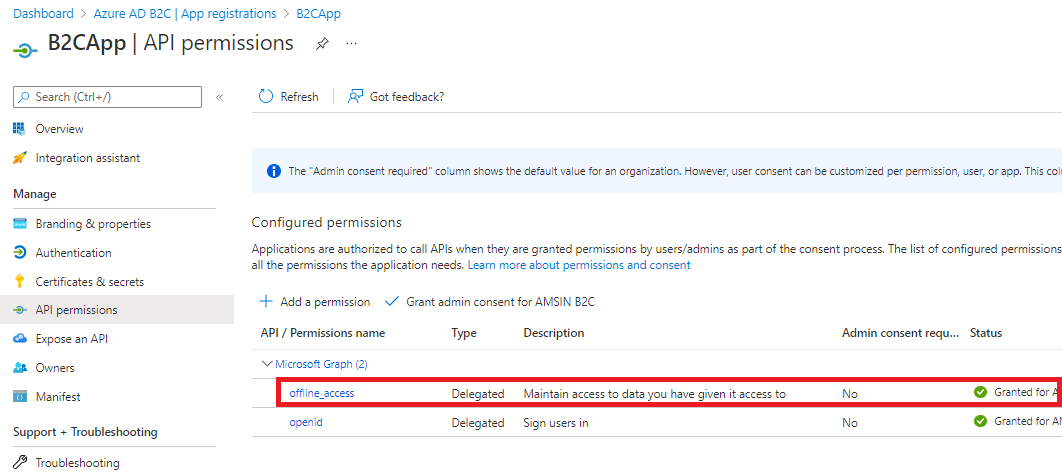
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.