Hi @John evans • Thank you for reaching out.
The amr claim in the ID token can be used to identify whether the user has performed MFA or not. The type of this claim is Array and it contains the information about all the authentication methods performed by the user during the authentication process.
This claim is only available in version 1.0 tokens and not in 2.0 tokens (applicable to both ID and Access tokens). It is in the product roadmap to include the amr claim in version 2.0 tokens as well but there is no ETA as of now.
So when requesting the ID token you need to make sure the authentication request is sent at the V1 endpoint. Below are the authentication request examples (Implicit flow) to V1 and V2 endpoints:
- V1 Endpoint:
https://login.microsoftonline.com/your_tenant.onmicrosoft.com/oauth2/authorize?client_id=your_app_id&response_type=id_token&redirect_uri=your_reply_url&state=1234&response_mode=fragment&resource=https://graph.microsoft.com&nonce=1234&scope=openid - V2 Endpoint:
https://login.microsoftonline.com/your_tenant.onmicrosoft.com/oauth2/v2.0/authorize?client_id=your_app_id&response_type=id_token&redirect_uri=your_reply_url&state=1234&response_mode=query&scope=https://graph.microsoft.com/.default
When the authentication is performed via V1 endpoint, the token version is always version 1.0. Please refer to the screenshot of the decoded version 1.0 id token below, to see how this claim looks like:
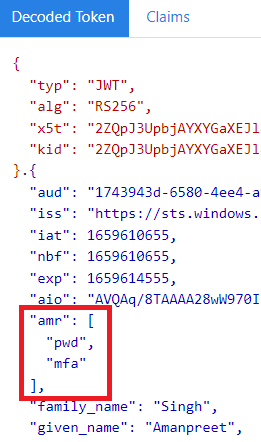
Read more: https://learn.microsoft.com/en-us/azure/active-directory/develop/access-tokens (look for amr claim)
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
