Hi @Ramakrishnan Venkataraman ,
Welcome to the Microsoft Q&A Platform. Thank you for reaching out & I hope you are doing well.
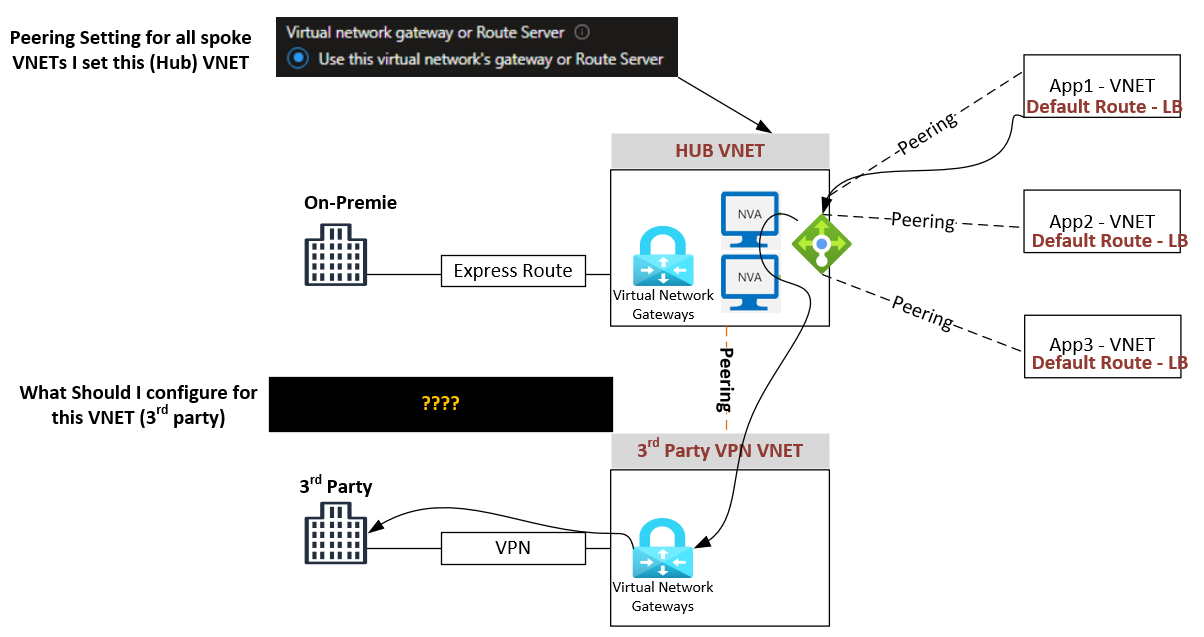
I understand that you are trying to build architecture as follows: Spoke-->Hub1-->Hub2-->OnPrem(3rd Party)
I am posting a summary of the discussions for the wider community's reach.
As suggested by @msrini-MSFT , the best way to go forward is to leverage Azure vWAN.
https://learn.microsoft.com/en-us/azure/virtual-wan/virtual-wan-route-table-nva-portal
We generally don't recommend multiple-Hub architectures.
Other than vWAN, you can also consider VPN-ExpressRoute Gateway co-existence with a single Hub
- Refer : https://learn.microsoft.com/en-us/azure/expressroute/how-to-configure-coexisting-gateway-portal#configure-a-site-to-site-vpn-to-connect-to-sites-not-connected-through-expressroute
- Your scenario comes under "Configure a Site-to-Site VPN to connect to sites not connected through ExpressRoute"
To address your queries,
Question 1
Question 3
- A Vnet, if it has a Virtual Network Gateway, then we cannot create a peering with another Vnet that has a Virtual Network Gateway with "Use Remote Gateways" enabled.
- "Use Remote Gateways" will be disabled.
- So, you cannot configure the peering to route traffic from HubVnet to 3rdPartyVPNVnet from the platform level.
Question 2
- This is not recommended.
- While one can make this work by adding manual routes, and deploying another NVA in 3rdPartyVPNVnet, it will be complex and difficult to manage
I see you have an InfoSec requirement that you need to have these Vnets isolated.
- Even with vWAN, and proper configuration of the Route table in vWAN, you can achieve this.
- https://learn.microsoft.com/en-us/azure/virtual-wan/how-to-virtual-hub-routing
As stated, you cannot configure the platform(Peering) to make a VM route traffic to two Gateways.
- The only way I can think of doing this is with the use of a Firewall/NVA in 3rdPartyVPNVnet
- You can set up routing between this Firewall and your existing NVA to exchange traffic.
- Ideally, this should work.
You confirmed you were able to follow the above action plan and make this work using the use of a Firewall/NVA (Palo Alto firewall)
Thanks,
Kapil
----------------------------------------------------------------------------------------------------------------
Please don’t forget to close the thread by clicking "Accept the answer" wherever the information provided helps you, as this can be beneficial to other community members.