The steps you have followed apply to the client credentials flow (application permissions), whereas your registered app is using delegate permissions. You are likely able to access other mailboxes because the user in which context you're running the app has the necessary Full access permissions.
As to the second question, IMAP is an outdated protocol and I wouldn't recommend using it. For integrating Exchange Online with other systems use the Graph API: https://learn.microsoft.com/en-us/graph/api/resources/mail-api-overview?view=graph-rest-1.0
Limiting IMAP permissions to specific Exchange Online mailboxes
 Due to the upcoming Basic Authentication Deprecation in Exchange Online – deadline of 10/1/22 , we have been working to change our web based ticket system (we were using basic authentication via IMAP) to use IMAP 4 with auth 2.0 authentication. We created an app using this link as a reference https://learn.microsoft.com/en-us/answers/questions/427049/office-365-oauth2-working-correctly-for-imap-not-w.html . We only want to give permission to access 1 emailbox so we followed these instructions here
Due to the upcoming Basic Authentication Deprecation in Exchange Online – deadline of 10/1/22 , we have been working to change our web based ticket system (we were using basic authentication via IMAP) to use IMAP 4 with auth 2.0 authentication. We created an app using this link as a reference https://learn.microsoft.com/en-us/answers/questions/427049/office-365-oauth2-working-correctly-for-imap-not-w.html . We only want to give permission to access 1 emailbox so we followed these instructions here
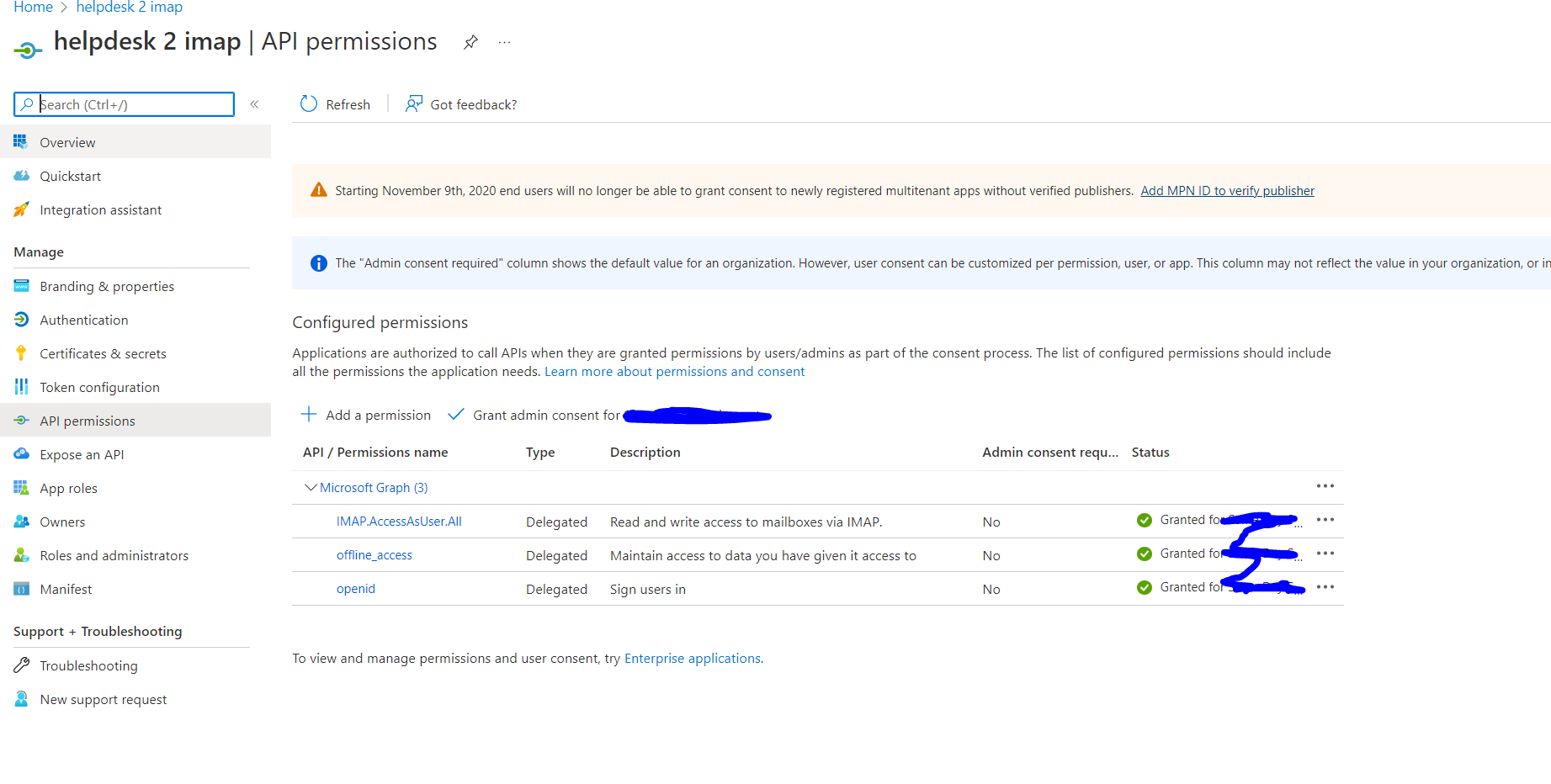
https://learn.microsoft.com/en-us/exchange/client-developer/legacy-protocols/how-to-authenticate-an-imap-pop-smtp-application-by-using-oauth . we followed where it states "Register service principals in Exchange" . We then set the Add-MailboxPermission to the mailbox we want to allow access to.
questions:
- The issue we are having is when we change the email box with the same token it still allows the connection. we only want access to 1 mailbox not all. How can we accomplish this?
- is IMAP via app Authentication the best workaround to integrate our web based ticket system to read emails ? I tried this solution but i came accross the same issue, we are able to read all mailboxes not just one. https://www.youtube.com/watch?v=AXssQL7LkRA
Exchange | Exchange Server | Management
Microsoft Security | Microsoft Graph
1 answer
Sort by: Most helpful
-
 Vasil Michev 119.7K Reputation points MVP Volunteer Moderator
Vasil Michev 119.7K Reputation points MVP Volunteer Moderator2022-08-24T15:43:32.09+00:00