iPad / iPhone Certificate Issuance
Hey all, Rob here again. It’s been a while since I have written a blog post, and this one was too interesting to pass up.
I recently worked a case around deploying certificates to Apple iPhones and iPads to secure their network communications. The investigation uncovered that Apple devices can get certificates via the Simple Certificate Enrollment Protocol (SCEP), also known in the Microsoft world as Network Device Enrollment Service (NDES) in Windows Server 2008/R2.
Extreme Disclaimer Warning!!!
Microsoft obviously does not directly support Apple products of any kind. Your first stop when troubleshooting or configuring any Apple product is:
https://www.apple.com/support/
Now that that is out of the way, let’s continue.
I was unable to find any true corporate support information on Apple’s webpage for the iPad or iPhone, only sales goo. If someone has a proper support link and phone number please send it along so I can update this post. Obviously, we’d rather have you talking to Apple about the iPhone or iPad as they are the authority on how those products should consume certificates.
Strangely, Apple doesn’t appear to document a step-by-step process for certificate enrollment, so on behalf of some Microsoft customers we had to figure it out. Bear in mind, there may be some changes to this article later.
Most of this blog is going to be covering the setup and configuration options with NDES to support the solution. If you have worked with MSCEP in the past, not much has changed other than some new registry keys to manage SCEP certificate enrollment. Enrolling for certificates against the old Windows Server 2003 SCEP-Add On utility does not work with Apple devices so Windows Server 2008 or later is required.
NDES Requirements:
- Only available on the Enterprise Edition of the Windows Server 2008 or Windows Server 2008 R2 operating systems.
- Can be installed on the same server as the CA, or on another member server. If you install it on another member server you can configure NDES to use a Windows Server 2003 CA.
- Requires the installation of the Certification Authority Web Enrollment role service on the NDES Server.
Installation:
The Installation of NDES is straight forward, however the steps below assume that you are installing the NDES role for an Enterprise Certification Authority rather than for a Standalone CA. If you are installing this for a Standalone CA certain settings should be skipped. I would encourage you to review the NDES whitepaper for more information.
1. Launch Server Manager.
2. Click on Add Roles.
3. Click the Next button.
4. Check Active Directory Certificate Services.
5. Click the Next button twice.
6. If you are installing the NDES Server on a separate server from the CA, uncheck Certification Authority.
7. Check Certification Authority Web Enrollment, and Network Device Enrollment Service.
NOTE: If you see a dialog box about adding required role services for Web Server (IIS), click the Add Required Role Services button.
8. Click the Next button.
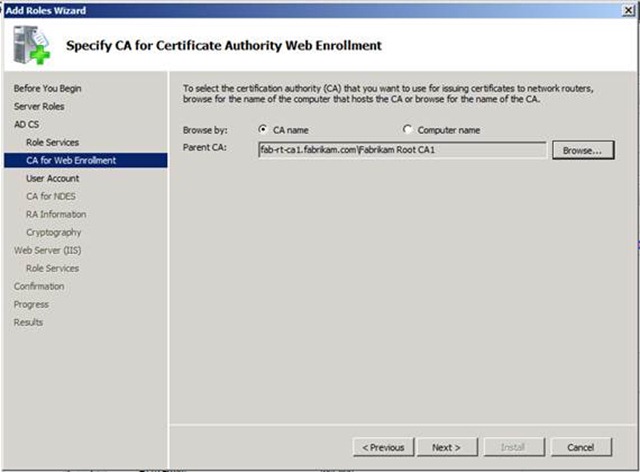
9. If you are not installing the role on a CA, you will be prompted with the screen shown below. You will need to select the Enterprise CA that should be used for the CA Web Enrollment pages. Click the browse button, and select the appropriate CA. If you want to use CA Web Enrollment Pages on a non-CA, see this blog about web enrollment proxy.
10. Click the Next button.
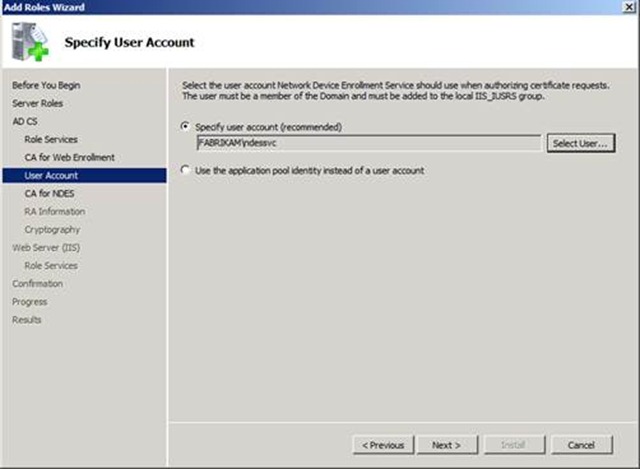
11. Provide a user account under which to run the IIS application pool account for the NDES web application. It is strongly recommended that you create a domain based service account. This account must be given the Enroll permissions on the certificate template(s) that NDES will use. This gives you the ability to lock down the certificate template so that only devices that use NDES can enrollment for certificates based on this template.
NOTE: The service account used MUST be added to the IIS_USRS group before attempting to use the account in the wizard.
12. Click the Next button.
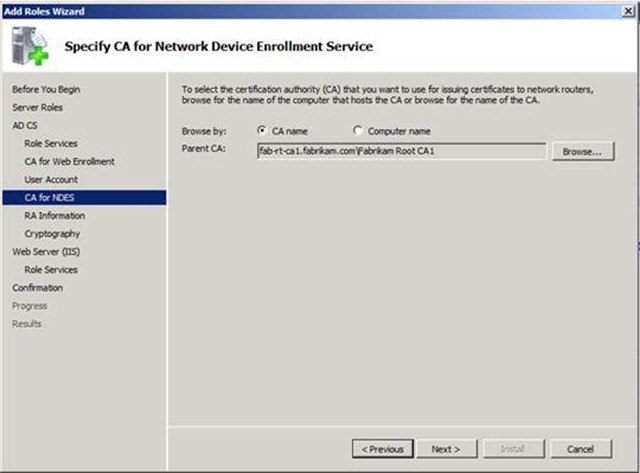
13. If you are installing NDES on a server other than the CA, you will be presented with the below screen to select the CA that the NDES web application will submit the requests it receives. Click the Browse button, and select the appropriate CA.
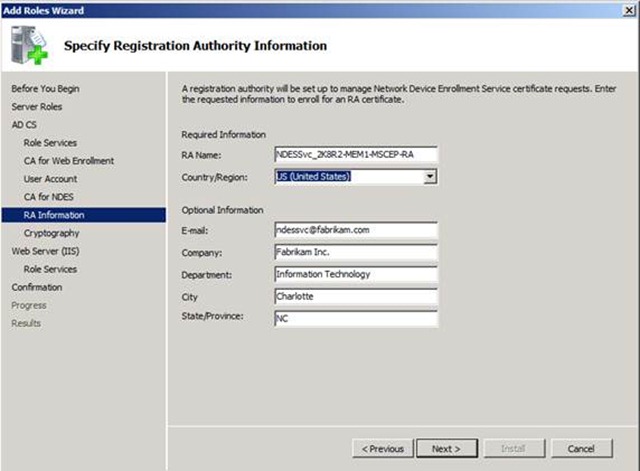
14. The next step is to provide information for the Registration Authority certificate to be issued to the web application pool account that we defined at step 11.
NOTE: The RA Name can be anything you like. The default is the computer’s name concatenated with ”–MSCEP-RA”. This becomes the subject line of the RA certificates.
15. Click the Next button.
16. Select the Signature and Encryption key CSPs to be used, as well as the Key length for the Registration Authority certificates. The default will work fine. If you later decide that you want to change this, review the following blog by Jonathan Stephens.
17. Click the Next button twice.
18. Click the Install button.
NDES Configuration settings:
NDES configuration settings are stored in the registry. I cover some of the more commonly modified registry keys; for a complete listing of configuration settings please read the NDES Whitepaper.
The base registry key location NDES reads is:
HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP
All the registry values referenced below are set in this registry key.
Template Settings
Use these settings to customize the certificate templates used by NDES.
SignatureTemplate (REG_SZ)
EncryptionTemplate (REG_SZ)
GeneralPurposeTemplate (REG_SZ)
These three registry keys hold the LDAP name of the template that should be issued for each type of key that the SCEP client could possibly request. There are three types of keys that can be specificed.
SignatureTemplate: The private key can only be used for creating a digital signature. In the certificate template configuration, this is denoted by the Purpose, Signature, on the Request Handling tab.
EncryptionTemplate: The private key can be used for encryption. In the certificate template configuration, this is denoted by the Purpose, Encryption, on the Request Handling tab.
GeneralPurposeTemplate: The private key can be used for both encryption and for creating a digital signature. In the certificate template configuration, this is denoted by the Purpose, Signature and encryption, on the Request Handling tab.
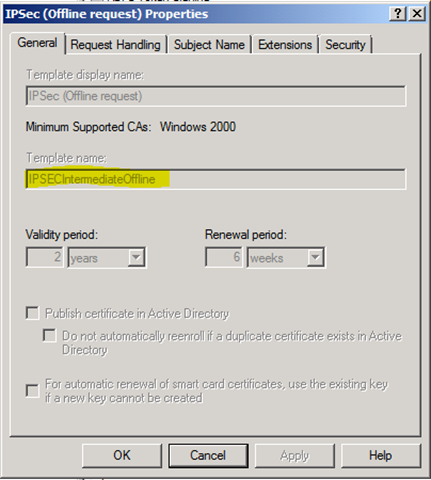
Here is a screen shot of a certificate template to show where the template name is that needs to be populated in the registry values. In the below figure it is IPSecIntermediateOffline (the default template used by NDES).
NOTE: If you decide to use a custom certificate template there are more requirements:
The NDES application pool identity needs enroll permissions on the template; this is set on the Security tab when looking at the properties of the template.
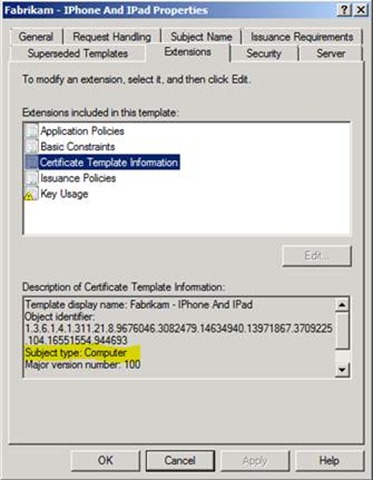
The template must be valid for computer and not user accounts. You can find out the template type by looking at the properties of the template and clicking on the Extensions tab. Then select the extension Certificate Template Information and you will see Subject type: Computer.
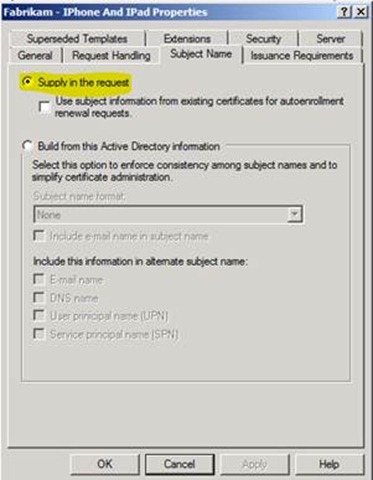
Template Subject Name should be set to Supply in the request. This can be seen by click on the Subject Name tab.
Now, let’s continue to look at the NDES configuration settings.
Password Settings
Use these settings to configure some of the password behavior in NDES.
Key: HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP
Value: PasswordValidity
Type: REG_DWORD
Data: Default 60 (decimal)
PasswordValidity sets the amount of time (in minutes) for which the NDES admin-supplied password is valid. The default value is 60 minutes, but most admins change this value to something that accommodates the time it takes to communicate the password to the device owner. The device owner enters this password on the device in order to enroll for a certificate.
A good value might be 0x78h (120 decimal). This will give the owner of the device 2 hours to get through the iPhone configuration utility and set the challenge password. If the validity period expires, and the device owner has failed to obtain a certificate, then the SCEP Admin will need to generate a new challenge for the user.
Key: HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP\PasswordMax
Value: PasswordMax
Type: REG_DWORD
Data: Default 5
PasswordMax sets the number of passwords that the service will track once the NDES admin starts generating passwords. This means that the NDES Admin can get X unique passwords generated at one time. Once the number has been reached the NDES admin will not be able to generate any further passwords until the old ones have been utilized by a device or the password validity has expired.
You can change the behavior of NDES to force the service to use only one password for all client certificate enrollments. This is used with the UseSinglePassword registry value added in the following hotfix:
959193 Two improvements are available that shorten the time that is required to manage SCEP certificates by using the Network Device Enrollment Service in Windows Server 2008
https://support.microsoft.com/kb/959193
IIS configuration change:
By default, IIS 7/7.5 security is too restrictive to permit these Apple devices to enroll via SCEP. With the out-of-the-box settings enrollment will fail with the following error in the Application event log:
Log Name: Application
Source: Microsoft-Windows-NetworkDeviceEnrollmentService
Date: {DATE}
Event ID: 11
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: {COMPUTERNAME}
Description:
The Network Device Enrollment Service received an http message without the "Operation" tag, or with an invalid "Operation" tag.
The IIS logs will show the following line when the iPad device attempts to send its certificate enrollment to the NDES server:
2010-11-04 12:43:38 10.28.40.27 GET /certsrv/mscep/mscep.dll operation=PKIOperation&message=MIAGCSqGSIb3DQEHAqCAMIACAQExCzAJGSIb3DQEHAaCAJIAEggSTMIAG%0 . . . {Shortened for the blog} . . . EMPlcwhmd8c1XAAAAAAAAA%3D%3D%0A 80 - 10.188.117.101 Settings/1.0+CFNetwork/467.12+Darwin/10.3.1 404 15 0 812
This is a 404.15 (Request Filtering: Denied because query string too long) error and it means that the amount of data being sent in the HTTP URL is larger than what is allowed by default. In the scenario above, the iPad was sending a string over 2700 characters, but the default size allowed by the request filtering is 1024. This is so in order to mitigate against buffer overrun attacks. To change the value you will use the following IIS appcmd.exe command:
%systemroot%\system32\inetsrv\appcmd.exe set config
/section:system.webServer/security/requestFiltering /requestLimits.maxQueryString:"3072"
/commit:apphost
The command above has been wrapped for clarity.
Generating the enrollment challenge password:
Alright, now that you have gone through the effort of configuring NDES you can generate the challenge so that you can add it to the iPhone / iPad configuration.
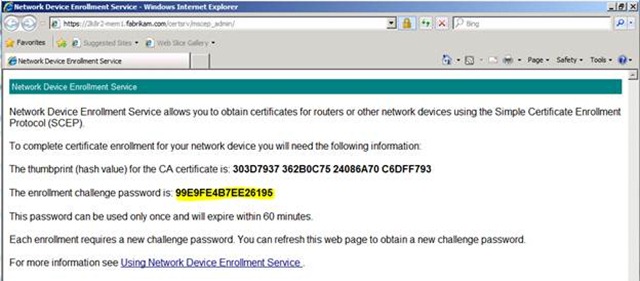
1. Launch Internet Explorer and go to:
https:// <NDES Server’s DNS FQDN> /CertSrv/MSCEP_Admin/.
So you would type something like:
https://2k8r2-mem1.fabrikam.com/CertSrv/MSCEP_Admin.
2. You will then see the following screen with the provided challenge:
Now you are ready to put the challenge password into the iPhone configuration utility.
iPhone / iPad configuration:
Alright, now we get to the “fun” section. As stated earlier, we do not support any of the applications or features shown in this section. If you try things the exact way that I show in this blog and it fails or if the utility is totally different a year from now, or whatever: don’t call us, call Apple. This blog post is about giving our best effort to be helpful, not for Microsoft to become Apple’s support and documentation channel.
Download and install the iPhone Configuration Utility 3.1 for Windows (never mind the name, it is for iPads also). Now you have an application where you can configure the SCEP settings. After this you will have to deploy the configuration settings to the iPhone / iPad device. Don’t ask us how to do this; Like Melinda, I don’t own any Apple devices for a repro and my customers had to figure it out. Or, step up to the Genius Bar.
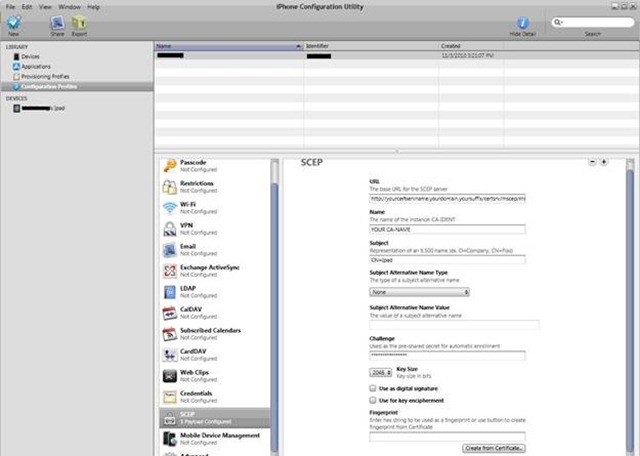
Below is the configuration utility screen with highlighting of the SCEP configuration settings.
Here are the settings you should use:
URL: https://yourNDESServerName.domain.com/certsrv/mscep/mscep.dll
The URL field should be the DNS name of the NDES server. So if the NDES server name is 2k8r2-mem1.fabrikam.com then the URL should be: https://2k8r2-mem1.fabrikam.com/certsrv/mscep/mscep.dll
NAME: YOUR CA-NAME
This should be the CA’s name from which you are requesting a certificate. Keep in mind that most CA names are really friendly names and usually are different than the CA’s computer name. For example: Fabrikam Issuing CA1.
Subject: O=Fabrikam,OU=IT,CN=Robs IPad
This is the subject field of the certificate issued to the iPhone/iPad device. It’s is backwards from the usual canonical form you are familiar with but that is the way Apple wants it.
Subject Alternative Name Type:
Leave this blank, unless you need some kind of Subject Alternative Name (SAN) on the issued certificate. If you plan on using a subject alternative name, then you will need to run the following commands on the CA before issuing certificates.
CertUtil -SetReg Policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
net stop certsvc & net start certsvc
NOTE: These instructions are counter to Microsoft's security best practices with regard to allowing SANs in certificates. Administrators are normally discouraged from enabling the EDITF_ATTRIBUTESUBJECTALTNAME2 EditFlag on an Enterprise CA because of the risk of impersonation attacks. This flag allows a user to specify arbitrary names in a certificate request; an ability that can be abused by persons with malicious intent. In this case, however, the certificate request is being generated by a third party configuration utility, so an Administrator will no control over how the SAN information is included in the request. In order to get this solution to work, the decision was made to accept the possible risk in favor of functionality. In your own enterprise, the results of such a choice may be different.
The actual risk only exists with those certificate templates that are configured to accept subject information in the request. If the certificate subject is built using information from Active Directory, the subject name information in the request is ignored. The risk can be further mitigated by modifying the permissions on the templates used by NDES so that only the NDES service account is permitted to enroll. The EditFlag is global to the CA, however, so any certificate templates enabled on the CA and configured to accept subject information in the request represent a potential vector of attack.
For more information on Microsoft's security best practices for allowing SANs in certificates, review this information.
Challenge:
This is the password that is given to you from the NDES administrator. If you are the NDES administrator this is the password that you get from visiting the site: https://yourNDESServerName.domain.com/certsrv/mscep_admin/
Key Size:
This is the key size of the certificate you are requesting. This value has to be set to the value set in the certificate template.
Use as digital signature and Use for key encipherment checkboxes:
Checking / unchecking of these values determines which certificate template is specified by NDES when sending the request to the CA. These are directly related to the registry value settings of SignatureTemplate, EncryptionTemplate, and GeneralPurposeTemplate. What boxes to check depends on the application that needs the certificate.
Fingerprint:
Leave this blank.
Final Thoughts
Hopefully between this blog and the configuration utility you will be able to successfully issue certificate to the iPhone or iPad. Please keep in mind that we have not discussed anything advanced with NDES, nor have we talked about how to secure this powerful service. Please review the NDES Whitepaper to learn more about these topics.
Oh….and one last thing. If you have problems or issues with the iPad or iPhone, call Apple.
Rob “I know the turtle neck comments are coming” Greene