Step-by-Step: Extending On-Premise Active Directory to the Cloud with Windows Azure - 31 Days of Servers in the Cloud - Part 20 of 31
Extending an on-premise Windows Server Active Directory ( AD ) infrastructure into the cloud is an important topic to consider when planning the migration or implementation of cloud-based applications. Many existing applications require Active Directory for authentication and identity management. When migrating applications to the cloud, having a locally accessible Active Directory is an important factor to ensuring that AD authentication is fast and reliable.
What about Disaster Recovery of Active Directory?
Great point! Extending an on-premise Active Directory into the cloud can also provide a cost-effective option for protecting Active Directory in DR scenarios. In the event of a physical disaster or outage at your primary data center location, a VM running Active Directory in the Windows Azure cloud can provide uninterrupted access to Active Directory for cloud-based applications and other on-premise AD-integrated applications.
Active Directory Options in the Cloud
When planning for Active Directory in the Cloud with our Windows Azure cloud platform, there’s two options available:
- Windows Azure Active Directory – a cloud-based authentication service that is similar to on-premise Active Directory, but primarily intended for new applications that are being developed for the cloud ( ie., “Cloud-first” applications ).
- Windows Server Active Directory on Windows Azure VMs – this option provides the ability to host a full instance of Windows Server Active Directory, running on Windows Server 2008 R2 SP1 or Windows Server 2012, as a virtual machine in the Windows Azure cloud.
You can read more about both Active Directory cloud options at:
In this article, we’ll be stepping through the components involved with the second option listed above to extend an on-premise Active Directory infrastructure using Windows Server Active Directory on Windows Azure VMs.
In future articles, I’ll cover the configuration of Windows Azure Active Directory for providing authentication and identity management for “Cloud-first” applications.
Scenario: Extending Windows Server Active Directory into the Cloud
In the scenario described in this article, we’ll be connecting an existing on-premise network with a virtual network in the Windows Azure cloud via a secure Site-to-Site IPsec VPN tunnel. Once the tunnel is connected, the Windows Azure Virtual Network can be treated much like any another subnet on a Wide Area Network (WAN) when provisioning network services that will run in a Windows Azure Virtual Machine.

Scenario: Extending Active Directory into the Cloud
Prerequisites
The following is recommended to follow along with this article:
- A Windows Azure subscription with the Virtual Machines Preview enabled.
DO IT: Sign up for a FREE Trial of Windows Azure
NOTE: When activating your FREE Trial for Windows Azure, you will be prompted for credit card information. This information is used only to validate your identity and your credit card will not be charged, unless you explicitly convert your FREE Trial account to a paid subscription at a later point in time.
- Completion of the Getting Started tasks in the following article:
DO IT: Getting Started with Servers in the Cloud
- Prior experience with Windows Server Active Directory. This article also assumes that the reader is already somewhat familiar with configuring Windows Server 2012 Active Directory in an on-premise deployment. For a primer on What’s New in Windows Server 2012 Active Directory, join our Windows Server 2012 “Early Experts” study group and review the following study guide:
DO IT: Complete the “Early Experts” Installer Quest – Installing Active Directory
Steps: Extending Windows Server Active Directory into the Cloud
To complete the scenario described in this article for extending Windows Server Active Directory into the cloud, we will be using the following exercises:
- Configure On-Premise Active Directory Sites and Subnets
- Register DNS Servers in Windows Azure
- Build Windows Azure Virtual Network with Site-to-Site VPN connectivity
- Provision a new Replica Domain Controller in Windows Azure
Let’s get started!
Exercise 1 – Configure On-Premise Active Directory Sites and Subnets
The Windows Azure Virtual Network that we’ll be building in this article can be treated just like any other site on a Wide Area Network from an Active Directory sites and subnets perspective. Prior to installing and configuring Active Directory on a VM in the cloud, follow these steps to prepare your on-premise Active Directory for the new “virtual WAN location” that we’ll be building in the Windows Azure cloud:
- Launch the Active Directory Sites and Services tool.
We’ll be using the Active Directory Sites and Services tool to add a new AD site and subnet to our on-premise AD sites configuration. In Windows Server 2012, this tool can be launched in Server Manager by selecting Tools | Active Directory Sites and Services from the top navigation menu.
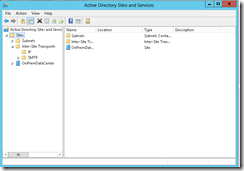
Active Directory Sites and Services tool
- Create a new AD Site for Windows Azure.
In the Active Directory Sites and Services window, right-click on the Sites folder in the left navigation pane and select New Site… from the pop-up menu.
In the New Object – Site dialog box, enter WindowsAzurein the Name: field and click on DEFAULTIPSITELINK in the Link Name list.
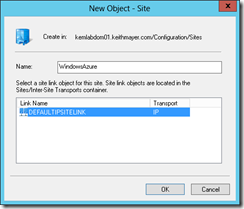
Creating a New AD Site for Windows Azure
Click the OK button to create a new AD site.
- Create a new AD Subnet for Windows Azure.
In the Active Directory Sites and Services window, right-click on the Subnets folder located below the Sites folder in the left navigation pane. Select New Subnet… from the pop-up menu.
In the Prefix: field, enter the IPv4 subnet in which the Windows Server Active Directory replica domain controller in this scenario will be located using CIDR notation: 10.0.2.0/24
Click on the WindowsAzure AD site in the Select a site object for this prefix list to associate this new subnet with the WindowsAzure AD site.
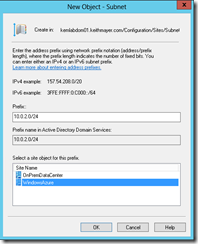
Creating a New AD Subnet for Windows Azure
Click the OK button to create the new AD Subnet for Windows Azure.
The on-premise Windows Server Active Directory infrastructure is now prepared for adding a new Replica Domain Controller as a Windows Azure VM, and you can continue on with the next exercise.
Exercise 2: Register DNS in Windows Azure
In this exercise, we’ll be registering our existing on-premise Active Directory-integrated DNS server with Windows Azure. We’ll also be registering the cloud-based Active Directory-integrated DNS server that will be provisioned in Exercise 4 as a Replica Domain Controller using Windows Azure VMs. By registering these DNS servers with Windows Azure, we will be able to associate them with our Windows Azure Virtual Network in Exercise 3, so that this DNS server information will be provided to all VMs that are provisioned on the Windows Azure Virtual Network.
- Launch the Windows Azure Management Portal.
Sign-in to the Windows Azure Management Portal with the credentials that you used when registering for the FREE 90-Day Windows Azure Trial.
Windows Azure Management Portal
- Register the On-Premise Active Directory-integrated DNS Server.
Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
In the NEW menu, select Networks | Virtual Network | Register DNS Server. In the Name field, type OnPremDNS01. In the DNS Server IP Address field, type the IPv4 address associated with the on-premise DNS Server in this scenario: 10.1.0.2
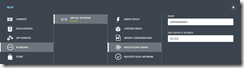
Register On-Premise DNS Server
Click the Register DNS Server button to register this DNS Server with Windows Azure.
- Register the Cloud-based Active Directory-integrated DNS Server.
Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
In the NEW menu, select Networks | Virtual Network | Register DNS Server. In the Name field, type CloudDNS02. In the DNS Server IP Address field, type the IPv4 address associated with the cloud DNS Server that will be provisioned in Exercise 4: 10.0.2.4
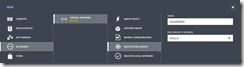
Register Cloud-Based DNS Server
Click the Register DNS Server button to register this DNS Server with Windows Azure.
The on-premise and cloud-based DNS servers are now registered with Windows Azure, and you may continue with the next exercise.
Exercise 3: Build Windows Azure Virtual Network with Site-to-Site VPN Connectivity
In this exercise, we’ll be building a Windows Azure Virtual Network to provide a virtual networking environment for running VMs on the Windows Azure cloud. We’ll also be connecting this virtual network to the on-premise data center network in this scenario by provisioning a Site-to-Site VPN gateway.
- Launch the Windows Azure Management Portal.
Sign-in to the Windows Azure Management Portal with the credentials that you used when registering for the FREE 90-Day Windows Azure Trial.
Windows Azure Management Portal
- Define the Windows Azure Virtual Network.
- Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
- In the NEW menu, select Networks | Virtual Network | Custom Create to launch the Create a Virtual Network wizard.
- On the Virtual Network Details page, enter a description name for the new Virtual Network, such as WindowsAzureNetwork01 and select the Affinity Group previously defined in the Getting Started steps listed in the prerequisite section of this article.
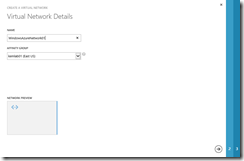
Virtual Network Details
Click the button to continue.
button to continue.
- On the Address Space and Subnets page, click on the CIDR button located at the top-right of the page and complete the fields to reflect the address space and subnets in our scenario for the Windows Azure cloud-based Virtual Network as illustrated in the following diagram:
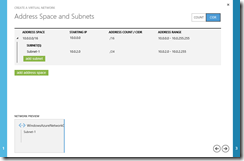
Virtual Network Address Space and Subnets
Click the button to continue.
button to continue.
- On the DNS Servers and Local Network page, select OnPremDNS01 and CloudDNS02 ( in this order ) as DNS Servers to associate with the new Windows Azure Virtual Network and any Virtual Machines defined in the future on this virtual network.
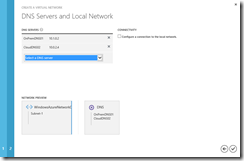
DNS Servers to associate with the Windows Azure Virtual Network
Do not click any additional buttons on the page at this time. Instead, continue with the next step in this exercise.
- Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
- Define Site-to-Site VPN Connectivity.
- On the DNS Servers and Local Network page, check the checkbox option for Configure a connection to the local network.
- In the Gateway Subnet field, enter the subnet in this scenario on which the Windows Azure VPN Gateway will be located: 10.0.1.0/24.
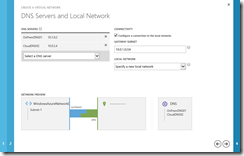
Virtual Network Connection to a Local Network
Click the button to continue.
button to continue.
- On the Specify a New Local Network page, complete the following fields with the related On-Premise network values from this scenario:
Name: OnPremNetwork01
VPN Device IP Address: 1.1.1.1
Address Space: 10.1.0.0/16
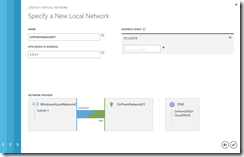
Specify a New Local Network
NOTE: To establish a Site-to-Site VPN connection with the Windows Azure Gateway, your on-premise VPN device is required to be located as an edge device ( ie., not located behind a NAT firewall ) and must have a valid public IPv4 address assigned to the external interface.
Click the button to begin provisioning the new Windows Azure Virtual Network definition.
button to begin provisioning the new Windows Azure Virtual Network definition.
- On the DNS Servers and Local Network page, check the checkbox option for Configure a connection to the local network.
- Provision the Windows Azure Site-to-Site VPN Gateway.
- Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
- Click on the name of the new virtual network, WindowsAzureNetwork01, to navigate to the details of the virtual network.
- On the WindowsAzureNetwork01 Dashboard page, click on the +CREATE GATEWAY button located on the bottom toolbar and click the Yes button to create the Windows Azure Site-to-Site VPN Gateway.
Provisioning the Windows Azure VPN Gateway
VPN Gateway creation on Windows Azure may require a few minutes to complete. Wait for this process to finish before proceeding with the next step.
- Click on the NETWORKS link in the left navigation pane of the Windows Azure Management Portal and then click the +NEW button located on the bottom toolbar.
- Provision the On-Premise Site-to-Site VPN Gateway.
Provisioning an on-premise Site-to-Site VPN Gateway varies by VPN device manufacturer and model. Check with your VPN device documentation for the specific steps involved in provisioning IPsec site-to-site VPN connectivity.
When working through the steps for provisioning your on-premise VPN device, you will need the following information from Windows Azure to complete the configuration:
- The public IPv4 address of the Windows Azure VPN Gateway.
You can view the public IPv4 address of the Windows Azure VPN Gateway on the WindowsAzureNetwork01 Dashboard page after Windows Azure has completed creating the gateway. The address is listed as the Gateway IP Address.
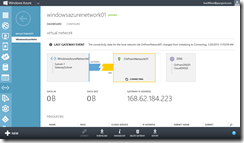
Public IPv4 Address of the Windows Azure VPN Gateway
In my example above, the public IPv4 address for my gateway is 168.62.184.223. Note that this public IPv4 address is provisioned uniquely for each Windows Azure gateway, so the public IPv4 address for your gateway will be different.
- The credentials for authenticating the Site-to-Site VPN connection.
Windows Azure Site-to-Site VPN capabilities use Pre-shared Keys to authenticate VPN connections. You can retrieve the key for authenticating your VPN connection by clicking on the MANAGE KEY button on the bottom toolbar of the WindowsAzureNetwork01 Dashboard page.
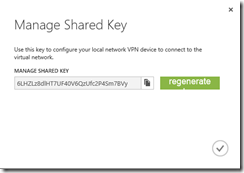
Windows Azure VPN Pre-shared Key
Click on the Clipboard button located to the right of the pre-shared key to copy this key to your local PC clipboard.
Click the button when done to close this window.
button when done to close this window.
- A sample configuration script for IPsec site-to-site VPN connectivity between Windows Azure and your on-premise VPN device.
To download a sample configuration script, click the DOWNLOAD button on the bottom toolbar of the WindowsAzureNetwork01 Dashboard page.
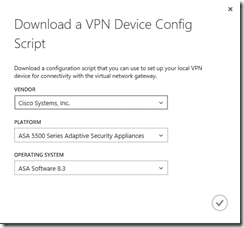
Download a VPN Device Config Script
Select the Vendor, Model, and Operating System that most closely matches your on-premise VPN device and click the button to download the sample configuration script.
button to download the sample configuration script.
- Using your VPN device documentation as a reference, merge the VPN device public IPv4 address, pre-shared key and sample configuration script retrieved in the steps above with your existing on-premise VPN device configuration.
NOTE: As part of this process, you may also need to update the routing tables on your internal routers such that attempts to route to the WindowsAzureNetwork01 address space ( 10.0.0.0 / 16 ) are routed to the internal interface of your on-premise VPN gateway ( 10.1.0.1 )
Once you’ve completed these steps successfully, the Site-to-Site VPN Gateway should show with a Connected status on the WindowsAzureNetwork01 Dashboard page in the Windows Azure Management Portal.
- The public IPv4 address of the Windows Azure VPN Gateway.
Exercise 4: Provision a New Replica Domain Controller in Windows Azure
In this exercise, you will provision a new Windows Server 2012 VM on the Windows Azure cloud platform. During this exercise, this VM will also be promoted to an additional Replica Domain Controller in the Windows Server Active Directory currently hosted on-premise.
- Sign-in to the Windows Azure Management Portal with the logon credentials used when you signed up for your Free 90-Day Windows Azure Trial.
- Select Virtual Machines located on the side navigation panel on the Windows Azure Management Portal page.
- Click the +NEW button located on the bottom navigation bar and select Compute | Virtual Machines | From Gallery.
- In the Virtual Machine Operating System Selection list, select Windows Server 2012, December 2012 and click the
 button.
button.
- On the Virtual Machine Configuration page, complete the fields as follows:
- Virtual Machine Name: CloudAD02
- New Password and Confirm Password fields: Choose and confirm a new local Administrator password.
- Size: Small (1 core, 1.75GB Memory)
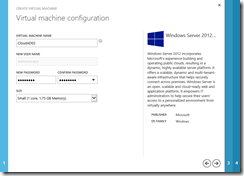
Virtual Machine Configuration
Click the button to continue.
button to continue.
Note: It is suggested to use secure passwords for Administrator users and service accounts, as Windows Azure virtual machines could be accessible from the Internet knowing just their DNS. You can also read this document on the Microsoft Security website that will help you select a secure password: https://www.microsoft.com/security/online-privacy/passwords-create.aspx.
- On the Virtual Machine Mode page, complete the fields as follows:
- Standalone Virtual Machine: Selected
- DNS Name: XXXcloudad02.cloudapp.net (where XXX are your unique initials to make this public cloudapp.net DNS name unique). This public DNS name will be used to establish a Remote Desktop connection to this VM for configuration purposes.
- Storage Account: Select the Storage Account defined in the Getting Started steps from the Prerequisites section above.
- Region/Affinity Group/Virtual Network: Select WindowsAzureNet01 – the Virtual Network defined in Exercise 3 above.
- Virtual Network Subnets: Select Subnet-1 (10.0.2.0/24)
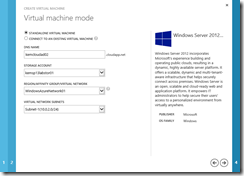
Virtual Machine Mode
Click the button to continue.
button to continue.
- On the Virtual Machine Options page, click the
 button to begin provisioning the new virtual machine.
button to begin provisioning the new virtual machine.
As the new virtual machine is being provisioned, you will see the Status column on the Virtual Machines page of the Windows Azure Management Portal cycle through several values including Stopped, Stopped (Provisioning), and Running (Provisioning) . When provisioning for this new Virtual Machine is completed, the Status column will display a value of Running and you may continue with the next step in this guide.
- After the new virtual machine has finished provisioning, click on the name ( CloudAD02 ) of the new Virtual Machine displayed on the Virtual Machines page of the Windows Azure Management Portal.
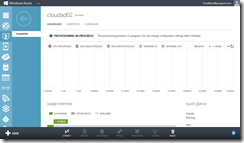
Virtual Machine Details for CloudAD02
- On the virtual machine details page for CloudAD02, scroll down the page and make note of the Internal IP Address displayed on this page. This IP address should be listed as 10.0.2.4.
If a different internal IP address is displayed, the virtual network and/or virtual machine configuration was not completed correctly. In this case, click the DELETE button located on the bottom toolbar of the virtual machine details page for CloudAD02, and go back to Exercise 3 to confirm that all steps were completed correctly.
- On the virtual machine details page for CloudAD02, click the Attach button located on the bottom navigation toolbar and select Attach Empty Disk. Complete the following fields on the Attach an empty disk to the virtual machine form:
- Name: CloudAD02-Data01
- Size: 10 GB
- Host Cache Preference: None
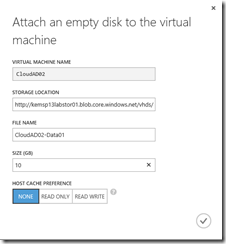
Attach an empty disk to the virtual machine
Click the button to create and attach the a new virtual hard disk to virtual machine CloudAD02.
button to create and attach the a new virtual hard disk to virtual machine CloudAD02.
- On the virtual machine details page for CloudAD02, click the Connect button located on the bottom navigation toolbar and click the Open button to launch a Remote Desktop Connection to the console of this virtual machine.
Connect to Virtual Machine via Remote Desktop
Logon at the console of your virtual machine with the local Administrator credentials defined in Step 5 above.
- From the Remote Desktop console of CloudAD02, create a new partition on the additional data disk attached above in Step 10 and format this partition as a new F: NTFS volume. This volume will be used for NTDS DIT database, log and SYSVOL folder locations.
If you need additional guidance to complete this step, feel free to leverage the following study guide for assistance: Windows Server 2012 “Early Experts” Challenge – Configure Local Storage
- Using the Server Manager tool, install Active Directory Domain Services and promote this server to a Replica Domain Controller in an existing Active Directory domain with the following parameters:
- Active Directory domain name: DNS name of on-premise Active Directory domain.
- Active Directory site name: WindowsAzure
- Volume Location for NTDS database, log and SYSVOL folders: F:
If you need additional guidance to complete this step, feel free to leverage the following study guide for assistance: Windows Server 2012 “Early Experts” Challenge – Install and Administer Active Directory
What’s Next? Keep Learning!
Continue our learning on Windows Azure and Windows Server 2012 with these great FREE resources:
- Learn more about Windows Azure Virtual Machines and Virtual Networks with 31 Days of Servers in the Cloud …
DO IT: Read 31 Days of Servers in the Cloud
- Learn more about Windows Server 2012 with our “Early Experts” study group and prepare for the new MCSA on Windows Server 2012 certification exams …
DO IT: Become a Windows Server 2012 “Early Expert”!
How are you planning to use Windows Azure?
Do you have a unique or interesting use case for Windows Azure Virtual Machines and Virtual Networks in the cloud? Be sure to leave your ideas, suggestions and feedback in the Comments section below!
Keith
Comments
Anonymous
January 01, 2003
Hi Jose, Sure thing. Once two domain controllers are setup ( one in Azure and one Onsite ) across a site-to-site VPN tunnel, they become peer DC's that replicate changes back and forth. For performance, you'd probably want to point your local clients to use their local DC so that you're not doing AD authentication over the site-to-site tunnel unless you local DC becomes unavailable for some reason. Hope this helps! KeithAnonymous
January 01, 2003
Hi Keith Very good description you have here. Can you help me with the VPN setup mentioned in 5d. What do I need to set this up ? Søren PCAnonymous
January 01, 2003
Hi Tabish, Yes - once the Site-to-Site VPN network is established, you may add a Windows Server 2012 domain controller in the cloud to your existing domain using the same process you'd use to add a Windows Server 2012 domain controller on-premises. While Windows Server 2012 domain controllers can co-exist in a Windows Server 2003 domain, you will not be able to take advantage of some of the new AD features in Windows Server 2012 until the domain and forest levels are updated. In addition, if you only have Windows Server 2003 domain controllers currently, you'll want to run ADPREP from another machine that is running Windows Server 2008 or later - it doesn't have to be a DC, just a member server in the domain will do. The Windows Server 2012 version of ADPREP does not work with Windows Server 2003. Hope this helps! Best regards, KeithAnonymous
January 01, 2003
Hi Søren, In our pre-release Preview offering of Windows Azure Virtual Networks, we're supporting Cisco ASA and Juniper on-premise VPN gateways, so you'll need one of those devices currently to test with. Broader device support is planned with other partner VPN solutions as well. In addition, your on-premise VPN device will need to have support for IPsec site-to-site tunnels and have a public ( non-NAT'd ) IPv4 address for its external interface. Hope this helps! KeithAnonymous
January 01, 2003
The comment has been removedAnonymous
January 01, 2003
My On Premise AD is on 2003 Is it possible to have a replica domain controller on WS2012 in Azure ?Anonymous
March 07, 2013
Hi Keith, Thanks for your excellent description. Please, help me to draw network diagram for my on premise and azure cloud. I am not able to understand how to proceed. I have to deploy IIS / SQL / SharePoint Production servers on Azure. Our Staging servers will be in on premise, so let me know:- Should I keep DC on both places? How on premise user will connect to Azure servers/application and their authentication will be verified? How remote users will be able to connect Azure application? I am totally confused, plz help me... regards, KumarAnonymous
March 14, 2013
Can I have AD on Windows Azure and use my local server like a mirror for the AD?Anonymous
September 17, 2014
Step-by-Step: Extending On-Premise Active Directory to the Cloud with Windows Azure - 31 Days of Servers in the Cloud - Part 20 of 31 - KeithMayer.com - Site Home - TechNet Blogs