Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you use the Microsoft Entra admin center to add an enterprise application that uses the OpenID Connect (OIDC) standard for Single sign-on (SSO). After you configure SSO, your users can sign in by using their Microsoft Entra credentials.
We recommend you use a nonproduction environment to test the steps in this page.
Prerequisites
To configure OIDC-based SSO, you need:
- A Microsoft Entra user account. If you don't already have one, you can Create an account for free.
- One of the following roles:
- Cloud Application Administrator
- Application Administrator
- owner of the service principal
Add the application from the Microsoft Entra app Gallery
When you add an enterprise application that uses the OIDC standard for SSO, you select a setup button. When you select the button, you complete the sign-up process for the application.
To configure OIDC-based SSO for an application:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
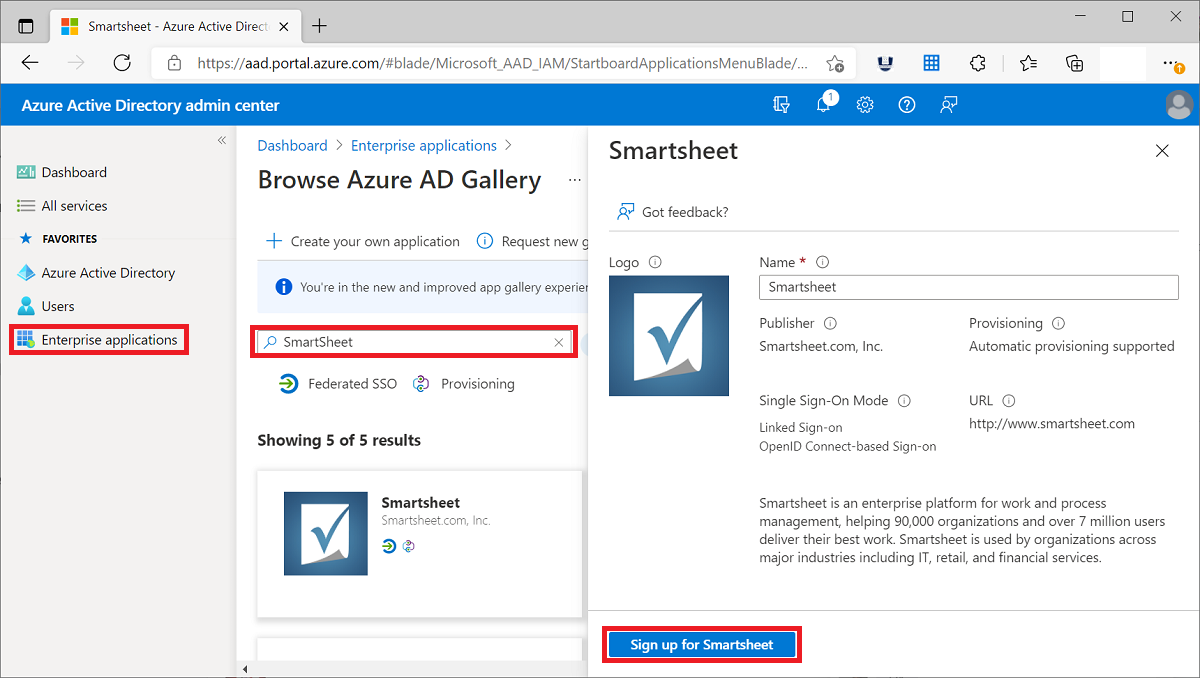
Browse to Entra ID > Enterprise apps > All applications.
In the All applications pane, select New application.
The Browse Microsoft Entra Gallery pane opens and displays tiles for cloud platforms, on-premises applications, and featured applications. Applications listed in the Featured applications section have icons indicating whether they support federated SSO and provisioning. Search for and select the application. In this example, SmartSheet is being used.
Select Sign-up. Sign in with the user account credentials from Microsoft Entra ID. If you already have a subscription to the application, then user details and tenant information is validated. If the application isn't able to verify the user, then it redirects you to sign up for the application service.
Select Consent on behalf of your organization and then select Accept. The application is added to your tenant and the application home page appears. To learn more about user and admin consent, see Understand user and admin consent.