Microsoft Entra SSO integration with CITI Program
This article teaches you how to integrate CITI Program with Microsoft Entra ID. CITI Program identifies education and training needs in the communities we serve and provides high-quality, peer-reviewed, web-based educational materials to meet those needs. When you integrate CITI Program with Microsoft Entra ID, you can:
- Control in Microsoft Entra ID who has access to CITI Program.
- Enable your users to be automatically signed in to CITI Program with their Microsoft Entra accounts.
- Manage your accounts in one central location.
You configure and test Microsoft Entra single sign-on for CITI Program in a test environment. CITI Program supports SP-initiated single sign-on and Just-In-Time user provisioning.
Note
The identifier of this application is a fixed string value so only one instance can be configured in one tenant.
Prerequisites
To integrate Microsoft Entra ID with CITI Program, you need:
- CITI Program Single Sign-On (SSO) enabled subscription. Note that SSO is a paid service with CITI Program.
- A Microsoft Entra user account. If you don't already have one, you can Create an account for free.
- One of the following roles: Application Administrator, Cloud Application Administrator, or Application Owner.
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
Add application and assign a test user
Before configuring single sign-on, you need to add the CITI Program application from the Microsoft Entra gallery and assign a test user account. Then, you can test the single sign-on configuration.
Add CITI Program from the Microsoft Entra gallery
Add CITI Program from the Microsoft Entra application gallery to configure single sign-on with CITI Program. For more information on how to add an application from the gallery, see the Quickstart: Add application from the gallery.
Create and assign Microsoft Entra test user
Follow the guidelines in the create and assign a user account article to create a test user account.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, and assign roles. The wizard also provides a link to the single sign-on configuration pane. Learn more about Microsoft 365 wizards..
Configure Microsoft Entra SSO
Complete the following steps to enable Microsoft Entra single sign-on.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > CITI Program > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, select the pencil icon for Basic SAML Configuration to edit the settings.
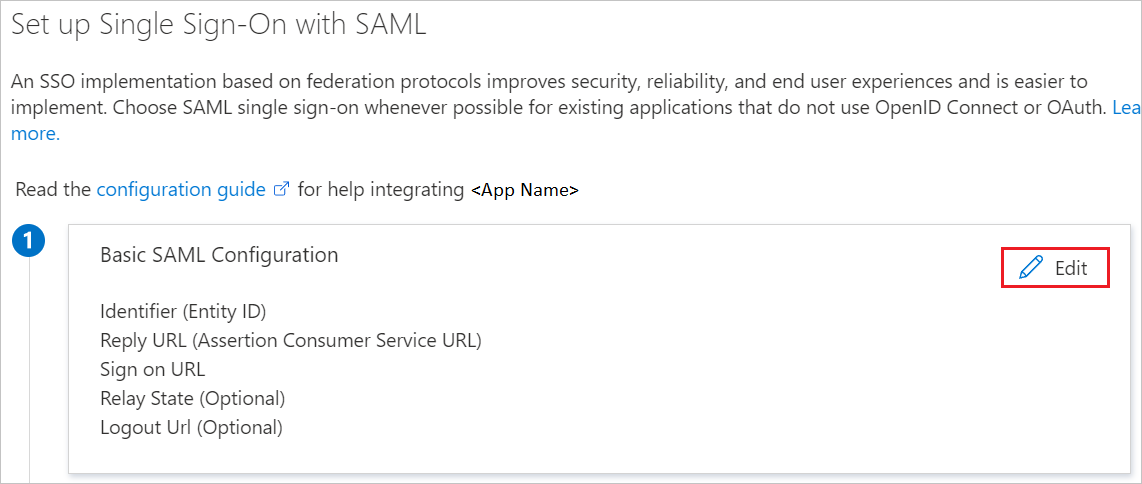
On the Basic SAML Configuration section, perform the following steps:
a. In the Identifier (Entity ID) textbox, use the URL:
https://www.citiprogram.org/shibbolethb. In the Reply URL (Assertion Consumer Service URL) textbox, use the URL:
https://www.citiprogram.org/Shibboleth.sso/SAML2/POSTc. In the Sign on URL textbox, use the URL:
https://www.citiprogram.org/portalNote
At the end of the configuration, you may update the Sign on URL with the SSO link provided by CITI Program Support.
The CITI Program application expects the SAML assertions in a specific format, which requires you to add custom attribute mappings to your SAML token attributes configuration. The following screenshot shows the list of default attributes.
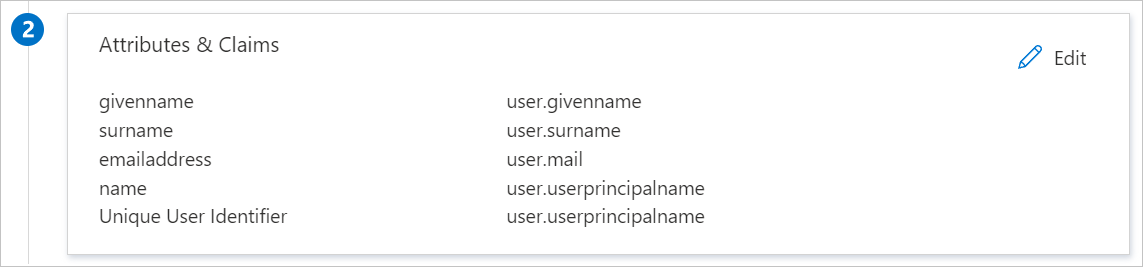
CITI Program application expects urn:oid named attributes to be passed back in the SAML response, shown below. These are all required. You may rename or remove the default attributes to configure them.
Name Source Attribute urn:oid:1.3.6.1.4.1.5923.1.1.1.6 user.userprincipalname urn:oid:0.9.2342.19200300.100.1.3 user.mail urn:oid:2.5.4.42 user.givenname urn:oid:2.5.4.4 user.surname If you wish to pass additional information in the SAML response, CITI Program can also accept the following optional attributes.
Name Source Attribute urn:oid:2.16.840.1.113730.3.1.241 user.displayname urn:oid:2.16.840.1.113730.3.1.3 user.employeeid urn:oid:1.3.6.1.4.1.22704.1.1.1.8 [other user attribute] Note
The Source Attribute is what is generally recommended but not necessarily a rule. For example, if user.mail is unique and scoped, it can also be passed as urn:oid:1.3.6.1.4.1.5923.1.1.1.6.
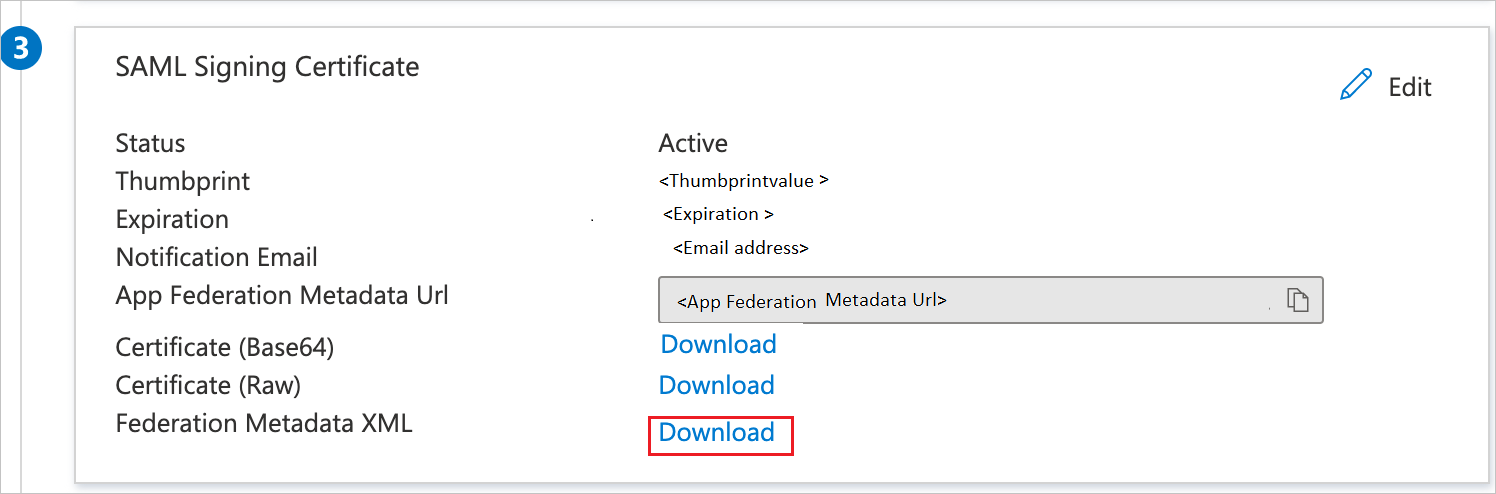
On the Set-up single sign-on with SAML page, in the SAML Signing Certificate section, find the App Federation Metadata Url and copy it, or the Federation Metadata XML and select Download to download the certificate.
On the Set up CITI Program section, copy the appropriate URL(s) based on your requirement.
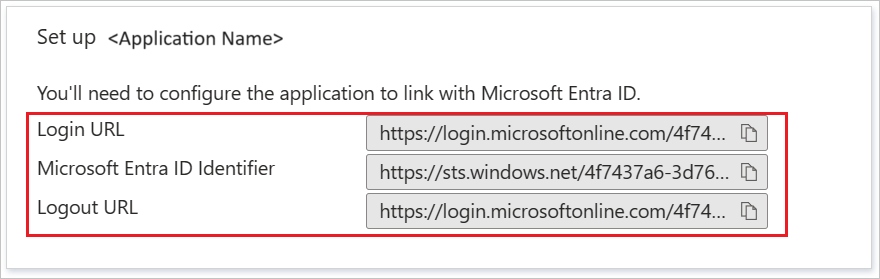
Configure CITI Program SSO
To configure single sign-on on CITI Program side, you need to send the copied App Federation Metadata Url or the downloaded Federation Metadata XML to CITI Program Support. This is required to have the SAML SSO connection set properly on both sides. Also, provide any additional scopes or domains for your integration.
Test SSO
In this section, you test your Microsoft Entra single sign-on configuration with the following options.
Click on Test this application, this will redirect to CITI Program Sign-on URL, where you can initiate the login flow.
Go to CITI Program Sign-on URL directly and initiate the login flow from there.
You can use Microsoft My Apps. Clicking the CITI Program tile in the My Apps will redirect to CITI Program Sign-on URL. For more information, see Microsoft Entra My Apps.
CITI Program supports just-in-time user provisioning. First-time SSO users will be prompted to either:
Link their existing CITI Program account in case they already have one
Or Create a new CITI Program account, which is automatically provisioned
Additional resources
- CITI Program SSO Technical Information
- What is single sign-on with Microsoft Entra ID?
- Plan a single sign-on deployment
Related content
Once you configure CITI Program you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real-time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Cloud App Security.