Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra ID supports applying sensitivity labels to Microsoft 365 groups when those labels are published in the Microsoft Purview portal or the Microsoft Purview compliance portal and the labels are configured for groups and sites.
Sensitivity labels can be applied to groups across apps and services such as Outlook, Microsoft Teams, and SharePoint. For more information, see Support for sensitivity labels from the Purview documentation.
Important
To configure this feature, there must be at least one active Microsoft Entra ID P1 license in your Microsoft Entra organization.
Enable sensitivity label support in PowerShell
To apply published labels to groups, you must first enable the feature. These steps enable the feature in Microsoft Entra ID. The Microsoft Graph PowerShell SDK comes in two modules, Microsoft.Graph and Microsoft.Graph.Beta.
All Microsoft operated regions should choose Microsoft. All other regions should choose their operator if one is listed.
Open a PowerShell prompt on your computer and install the Graph modules required to run the cmdlets.
Install-Module Microsoft.Graph -Scope CurrentUser Install-Module Microsoft.Graph.Beta -Scope CurrentUserConnect to your tenant.
Connect-MgGraph -Scopes "Directory.ReadWrite.All"Fetch the current group settings for the Microsoft Entra organization and display the current group settings.
$grpUnifiedSetting = Get-MgBetaDirectorySetting | Where-Object { $_.Values.Name -eq "EnableMIPLabels" } $grpUnifiedSetting.ValuesIf no group settings were created for this Microsoft Entra organization, you get an empty screen. In this case, you must first create the settings. Follow the steps in Microsoft Entra cmdlets for configuring group settings to create group settings for this Microsoft Entra organization.
Note
If the sensitivity label was enabled previously, you see
EnableMIPLabels = True. In this case, you don't need to do anything. Also make sure thatEnableGroupCreation = Falseif you don't want non-admin users to be able to create groups. See Template settings for details.Apply the new settings.
$params = @{ Values = @( @{ Name = "EnableMIPLabels" Value = "True" } ) } Update-MgBetaDirectorySetting -DirectorySettingId $grpUnifiedSetting.Id -BodyParameter $paramsVerify that the new value is present.
$Setting = Get-MgBetaDirectorySetting -DirectorySettingId $grpUnifiedSetting.Id $Setting.Values
If you receive a Request_BadRequest error, it's because the settings already exist in the tenant. When you try to create a new property:value pair, the result is an error. In this case, follow these steps:
- Issue a
Get-MgBetaDirectorySetting | FLcmdlet and check the ID. If several ID values are present, use the one where you see theEnableMIPLabelsproperty on the Values settings. - Issue the
Update-MgBetaDirectorySettingcmdlet by using the ID that you retrieved.
You also need to synchronize your sensitivity labels to Microsoft Entra ID. For instructions, see Enable sensitivity labels for containers and synchronize labels.
Assign a label to a new group in the Microsoft Entra admin center
Sign in to the Microsoft Entra admin center as at least a Groups Administrator.
Select Microsoft Entra ID.
Select Groups > All groups > New group.
On the New Group page, select Microsoft 365. Then fill out the required information for the new group and select a sensitivity label from the list.
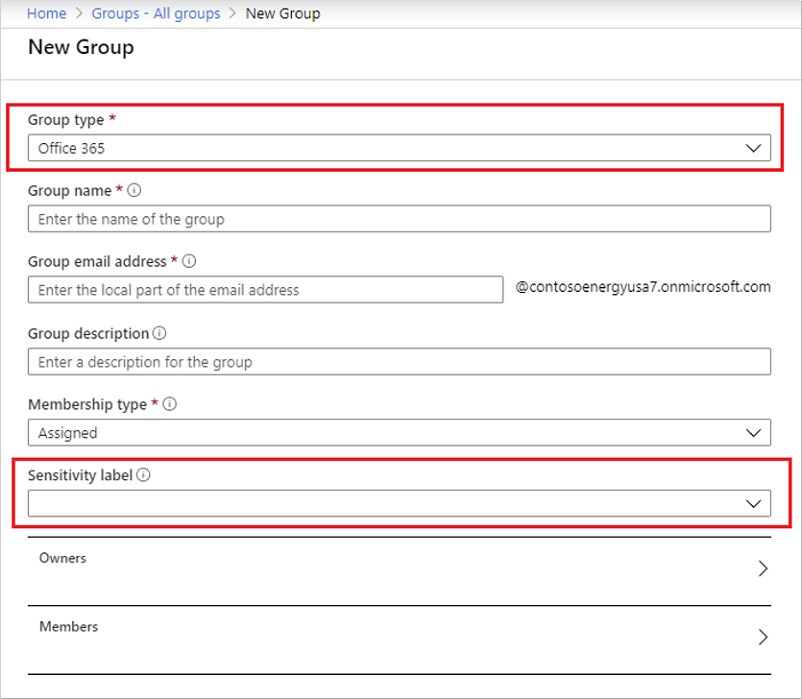
Select Create to save your changes.
Your group is created and the site and group settings associated with the selected label are then automatically enforced.
Assign a label to an existing group in the Microsoft Entra admin center
Sign in to the Microsoft Entra admin center as at least a Groups Administrator.
Select Microsoft Entra ID.
Select Groups.
From the All groups page, select the group that you want to label.
On the selected group's page, select Properties and select a sensitivity label from the list.
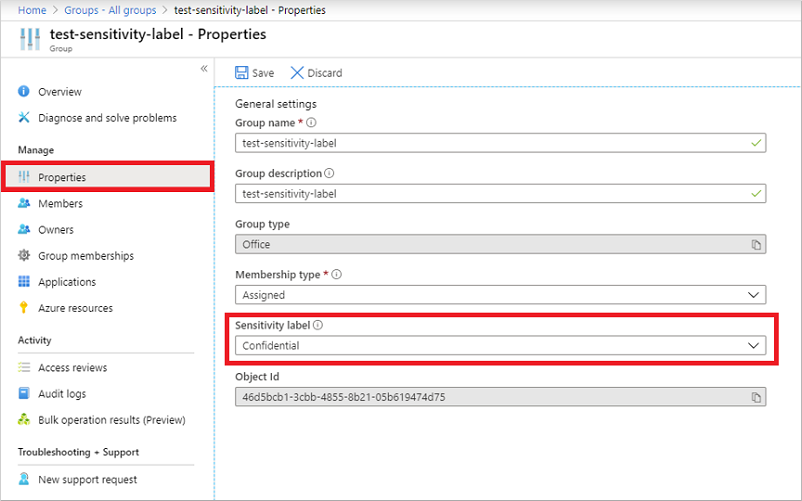
Select Save to save your changes.
Remove a label from an existing group in the Microsoft Entra admin center
- Sign in to the Microsoft Entra admin center as at least a Groups Administrator.
- Select Microsoft Entra ID.
- Select Groups > All groups.
- On the All groups page, select the group that you want to remove the label from.
- On the Group page, select Properties.
- Select Remove.
- Select Save to apply your changes.
Use classic Microsoft Entra classifications
After you enable this feature, the "classic" classifications for groups appear only on existing groups and sites. You should use them for new groups only if you create groups in apps that don't support sensitivity labels. Your admin can convert them to sensitivity labels later, if needed. Classic classifications are the old classifications you set up previously. When this feature is enabled, those classifications aren't applied to groups.
Troubleshooting issues
This section offers troubleshooting tips for common issues.
Sensitivity labels aren't available for assignment on a group
The sensitivity label option appears for groups only when all the following conditions are met:
- The organization has an active Microsoft Entra ID P1 license.
- The feature is enabled and
EnableMIPLabelsis set to True in the Microsoft Graph PowerShell module. - The sensitivity labels are published in the Microsoft Purview portal or the Microsoft Purview compliance portal for this Microsoft Entra organization.
- Labels are synchronized to Microsoft Entra ID with the
Execute-AzureAdLabelSynccmdlet in the Security & Compliance PowerShell module. It can take up to 24 hours after synchronization for the label to be available to Microsoft Entra ID. - The sensitivity label scope must be configured for Groups & Sites.
- The group is a Microsoft 365 group.
- The current signed-in user:
- Has sufficient privileges to assign sensitivity labels. The user must be the group owner or at least a Groups Administrator.
- Must be within the scope of the sensitivity label publishing policy.
Make sure all the preceding conditions are met to assign labels to a group.
The label you want to assign isn't in the list
If the label you're looking for isn't in the list:
- The label might not be published in the Microsoft Purview portal or the Microsoft Purview compliance portal. Also, the label might no longer be published. Check with your administrator for more information.
- The label might be published, but it isn't available to the user who is signed in. Check with your administrator for more information on how to get access to the label.
Change the label on a group
Labels can be swapped at any time by using the same steps as assigning a label to an existing group:
- Sign in to the Microsoft Entra admin center as at least a Groups Administrator.
- Select Microsoft Entra ID.
- Select Groups > All groups, and then select the group that you want to label.
- On the selected group's page, select Properties and select a new sensitivity label from the list.
- Select Save.
Group setting changes to published labels aren't updated on the groups
When you make changes to group settings for a published label in the Microsoft Purview portal or the Microsoft Purview compliance portal, those policy changes aren't automatically applied on the labeled groups. After the sensitivity label is published and applied to groups, Microsoft recommends that you don't change the group settings for the label in the portal.
If you must make a change, use a PowerShell script to manually apply updates to the affected groups. This method makes sure that all existing groups enforce the new setting.