This article describes how to achieve Trusted Internet Connections (TIC) 3.0 compliance for internet-facing Azure applications and services. It provides solutions and resources to help government organizations meet TIC 3.0 compliance. It also describes how to deploy the required assets and how to incorporate the solutions into existing systems.
Note
Microsoft provides this information to Federal Civilian Executive Branch (FCEB) departments and agencies as part of a suggested configuration to facilitate participation in the Cybersecurity and Infrastructure Security Agency (CISA) Cloud Log Aggregation Warehouse (CLAW) capability. The suggested configurations are maintained by Microsoft and are subject to change.
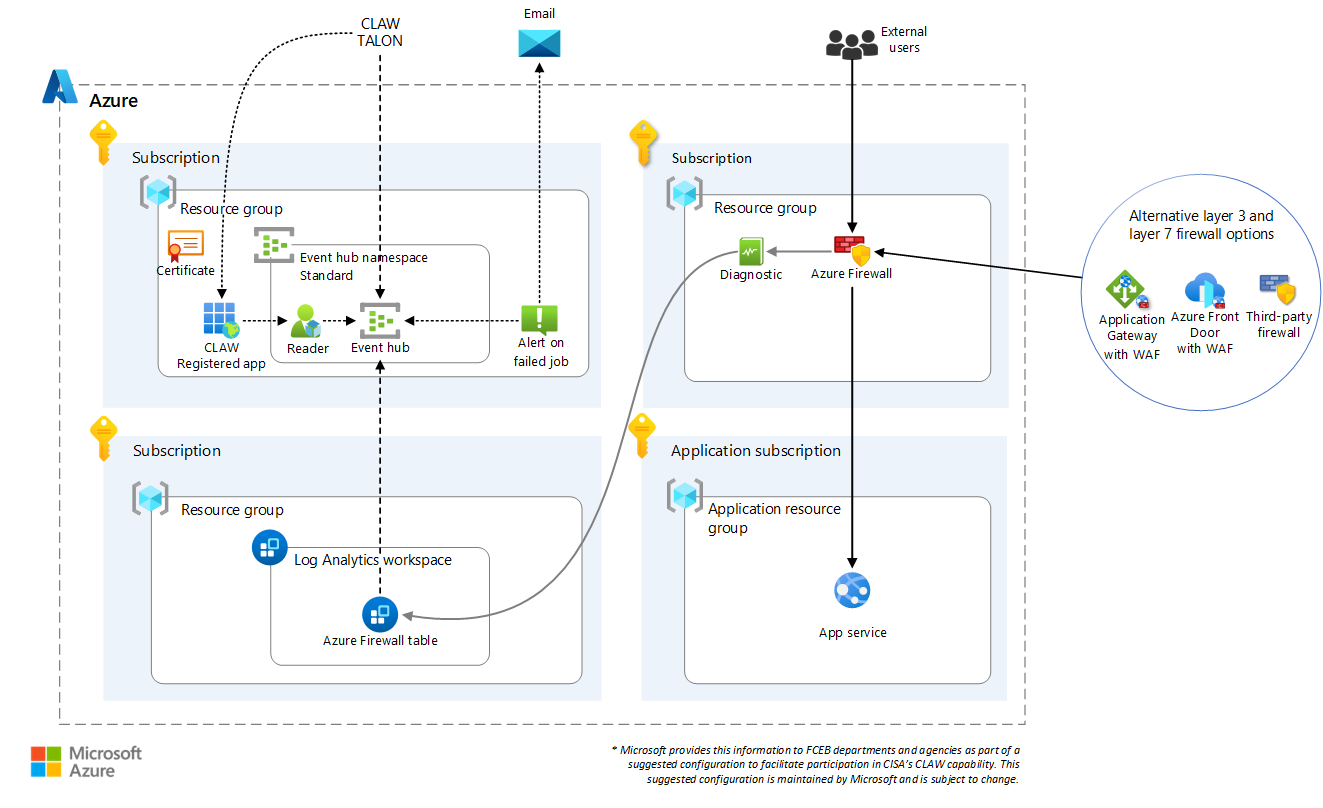
Architecture
Download a Visio file of this architecture.
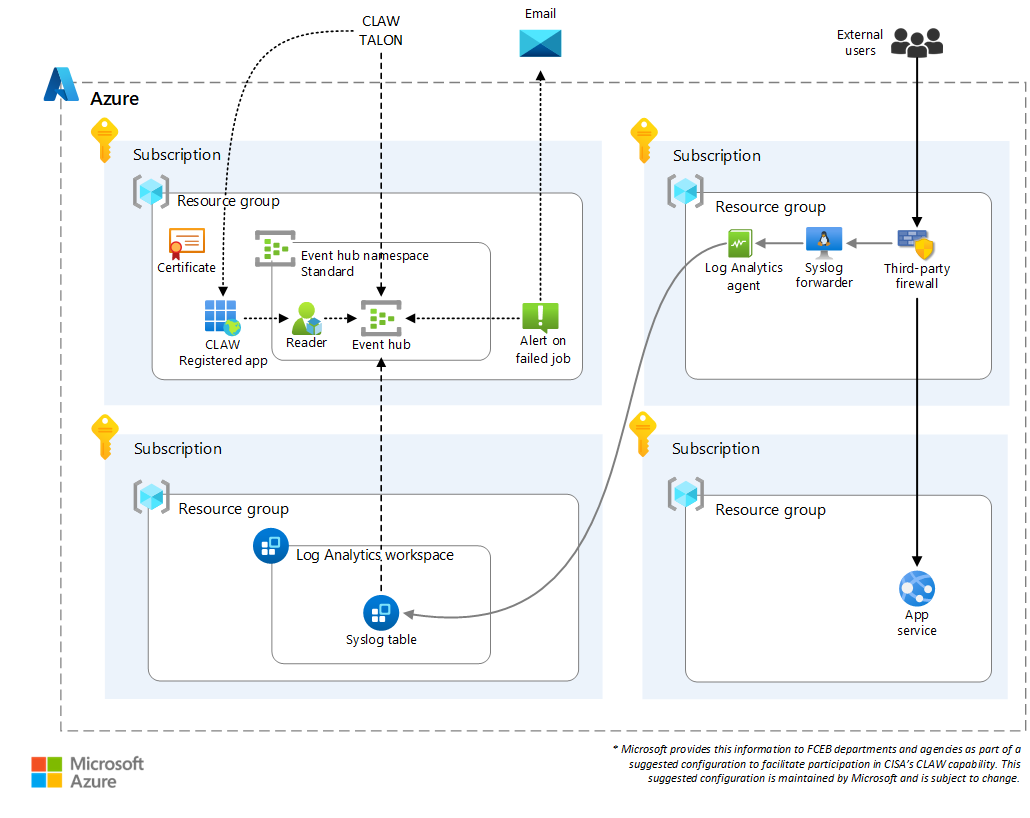
Dataflow
- Firewall
- The firewall can be any layer 3 or layer 7 firewall.
- Azure Firewall and some third-party firewalls, also known as Network Virtual Appliances (NVAs), are layer 3 firewalls.
- Azure Application Gateway with Web Application Firewall (WAF) and Azure Front Door with WAF are layer 7 firewalls.
- This article provides deployment solutions for Azure Firewall, Application Gateway with WAF, and Azure Front Door with WAF deployments.
- The firewall enforces policies, collects metrics, and logs connection transactions between web services and the users and services that access the web services.
- The firewall can be any layer 3 or layer 7 firewall.
- Firewall logs
- Azure Firewall, Application Gateway with WAF, and Azure Front Door with WAF send logs to the Log Analytics workspace.
- Third-party firewalls send logs in Syslog format to the Log Analytics workspace via a Syslog forwarder virtual machine.
- Log Analytics workspace
- The Log Analytics workspace is a repository for logs.
- It can host a service that provides custom analysis of the network traffic data from the firewall.
- Service principal (registered application)
- Azure Event Hubs Standard
- CISA TALON
Components
- Firewall. Your architecture will use one or more of the following firewalls. (For more information, see the Alternatives section of this article.)
- Azure Firewall is a cloud-native, intelligent network firewall security service that provides enhanced threat protection for cloud workloads that run on Azure. It's a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. It's available in two performance tiers: Standard and Premium. Azure Firewall Premium includes all the functionality of Azure Firewall Standard and provides additional features like Transport Layer Security (TLS) inspection and an intrusion detection and prevention system (IDPS).
- Application Gateway with WAF is a regional web traffic load balancer that enables you to manage traffic to your web applications. WAF provides enhanced centralized protection of your web applications from common exploits and vulnerabilities.
- Azure Front Door with WAF is a global web traffic load balancer that enables you to manage traffic to your web applications. It provides content delivery network (CDN) capabilities to speed up and modernize your applications. WAF provides enhanced centralized protection of your web applications from common exploits and vulnerabilities.
- A third-party firewall is an NVA that runs on an Azure virtual machine and uses firewall services from non-Microsoft vendors. Microsoft supports a large ecosystem of third-party vendors that provide firewall services.
- Logging and authentication.
- Log Analytics is a tool that's available in the Azure portal that you can use to edit and run log queries against Azure Monitor Logs. For more information, see Overview of Log Analytics in Azure Monitor.
- Azure Monitor is a comprehensive solution for collecting, analyzing, and acting on telemetry.
- Microsoft Entra ID provides identity services, single sign-on, and multifactor authentication across Azure workloads.
- A service principal (registered application) is an entity that defines the access policy and permissions for a user or application in a Microsoft Entra tenant.
- Event Hubs Standard is a modern big data streaming platform and event ingestion service.
- CISA TALON is a CISA-operated service that runs on Azure. TALON connects to your Event Hubs service, authenticates by using a CISA-supplied certificate that's associated with your service principal, and collects logs for CLAW consumption.
Alternatives
There are a few alternatives that you can use in these solutions:
- You can separate log collection into areas of responsibility. For example, you can send Microsoft Entra logs to a Log Analytics workspace that's managed by the identity team, and send network logs to a different Log Analytics workspace that's managed by the network team.
- The examples in this article each use a single firewall, but some organizational requirements or architectures require two or more. For example, an architecture can include an Azure Firewall instance and an Application Gateway instance with WAF. Logs for each firewall must be collected and made available for CISA TALON to collect.
- If your environment requires internet egress from Azure-based virtual machines, you can use a layer 3 solution like Azure Firewall or a third-party firewall to monitor and log the outbound traffic.
Scenario details
TIC 3.0 moves TIC from on-premises data collection to a cloud-based approach that better supports modern applications and systems. It improves performance because you can directly access Azure applications. With TIC 2.x, you need to access Azure applications via a TIC 2.x Managed Trusted Internet Protocol Service (MTIPS) device, which slows down the response.
Routing application traffic through a firewall and logging that traffic is the core functionality demonstrated in the solutions presented here. The firewall can be Azure Firewall, Azure Front Door with WAF, Application Gateway with WAF, or a third-party NVA. The firewall helps to secure the cloud perimeter and saves logs of each transaction. Independently of the firewall layer, the log collection and delivery solution requires a Log Analytics workspace, a registered application, and an event hub. The Log Analytics workspace sends logs to the event hub.
CLAW is a CISA managed service. In late 2022, CISA released TALON. TALON is a CISA managed service that uses Azure native capabilities. An instance of TALON runs in each Azure region. TALON connects to event hubs that are managed by government agencies to pull agency firewall and Microsoft Entra logs into CISA CLAW.
For more information on CLAW, TIC 3.0, and MTIPS, see:
- Trusted Internet Connections guidance
- TIC 3.0 core guidance documents
- National Cybersecurity Protection System (NCPS) documents
- EINSTEIN
- Managed Trusted Internet Protocol Services (MTIPS)
Potential use cases
TIC 3.0 compliance solutions are commonly used by federal organizations and government agencies for their Azure-based web applications and API services.
Considerations
These considerations implement the pillars of the Azure Well-Architected Framework, which is a set of guiding tenets that you can use to improve the quality of a workload. For more information, see Microsoft Azure Well-Architected Framework.
- Evaluate your current architecture to determine which of the solutions presented here provides the best approach to TIC 3.0 compliance.
- Contact your CISA representative to request access to CLAW.
- Use the Deploy to Azure buttons in this article to deploy one or more of the solutions in a test environment. Doing so should help you become familiar with the process and the deployed resources.
- See TIC 3.0 compliance for internet-facing applications, a complementary article that provides more details and assets for TIC 3.0:
- Additional information about achieving compliance.
- ARM templates to simplify deployment.
- Information to assist with integrating existing resources into the solution.
- The types of logs collected for each service layer and Kusto queries for reviewing logs collected by CISA. You can use the queries for your organization's security requirements.
Reliability
Reliability ensures your application can meet the commitments you make to your customers. For more information, see Overview of the reliability pillar.
- Azure Firewall Standard and Premium integrate with availability zones to increase availability.
- Application Gateway v2 supports autoscaling and availability zones to increase reliability.
- Multi-region implementations that include load balancing services like Azure Front Door can improve reliability and resiliency.
- Event Hubs Standard and Premium provide Geo-disaster recovery pairing that enables a namespace to fail over to a secondary region.
Security
Security provides assurances against deliberate attacks and the abuse of your valuable data and systems. For more information, see Overview of the security pillar.
- When you register an enterprise application, a service principal is created. Use a naming scheme for service principals that indicates the purpose of each one.
- Perform audits to determine the activity of service principals and the status of service principal owners.
- Azure Firewall has standard policies. WAFs associated with Application Gateway and Azure Front Door have managed rule sets to help secure your web service. Start with these rule sets and build organizational policies over time based on industry requirements, best practices, and government regulations.
- Event Hubs access is authorized via Microsoft Entra managed identities and a certificate that's provided by CISA.
Cost optimization
Cost optimization is about reducing unnecessary expenses and improving operational efficiencies. For more information, see Overview of the cost optimization pillar.
The cost of each solution scales down as the resources increase. The pricing in this Azure pricing calculator example scenario is based on the Azure Firewall solution. If you change the configuration, costs might increase. With some plans, costs increase as the number of ingested logs increase.
Note
Use the Azure pricing calculator to get up-to-date pricing that's based on the resources that are deployed for the selected solution.
Operational excellence
Operational excellence covers the operations processes that deploy an application and keep it running in production. For more information, see Overview of the operational excellence pillar.
- Azure Monitor alerts are built into the solutions to notify you when an upload fails to deliver logs to CLAW. You need to determine the severity of the alerts and how to respond.
- You can use ARM templates to speed up the deployment of TIC 3.0 architectures for new applications.
Performance efficiency
Performance efficiency is the ability of your workload to scale to meet the demands placed on it by users in an efficient manner. For more information, see Performance efficiency pillar overview.
- Azure Firewall, Application Gateway, Azure Front Door, and Event Hubs performance scales as usage increases.
- Azure Firewall Premium allows more TCP connections than Standard and provides increased bandwidth.
- Application Gateway v2 automatically ensures that new instances are spread across fault domains and update domains.
- Azure Front Door provides caching, compression, traffic acceleration, and TLS termination to improve performance.
- Event Hubs Standard and Premium provide auto-inflate to scale up as load increases.
Deploy an Azure Firewall solution
The following solution uses Azure Firewall to manage traffic entering your Azure application environment. The solution includes all resources for generating, collecting, and delivering logs to CLAW. It also includes an app service to track the types of telemetry collected by the firewall.
The solution includes:
- A virtual network that has separate subnets for the firewall and servers.
- A Log Analytics workspace.
- Azure Firewall with a network policy for internet access.
- Azure Firewall diagnostic settings that send logs to the Log Analytics workspace.
- A route table that's associated with the application resource group to route the app service to the firewall for the logs it generates.
- A registered application.
- An event hub.
- An alert rule that sends an email if a job fails.
For the sake of simplicity, all resources are deployed to a single subscription and virtual network. You can deploy the resources in any combination of resource groups or across multiple virtual networks.
Post-deployment tasks
After deployment, your environment performs the firewall capabilities and logging connections. To meet compliance with TIC 3.0 policies for network telemetry collection, you need to ensure that the logs make it to CISA CLAW. The post-deployment steps finish the tasks to enable compliance. To complete these steps, you need to coordinate with CISA because CISA needs to supply a certificate to associate with your service principal. For step-by-step details, see Post-deployment tasks.
You need to manually perform the following tasks after deployment. You can't complete them by using an ARM template.
- Obtain a public key certificate from CISA.
- Create a service principal (application registration).
- Add the public key certificate to the application registration.
- Assign the application the Azure Event Hubs Data Receiver role at the Event Hubs namespace scope.
- Activate the feed by sending the Azure tenant ID, application (client) ID, event hub namespace name, event hub name, and consumer group name to CISA.
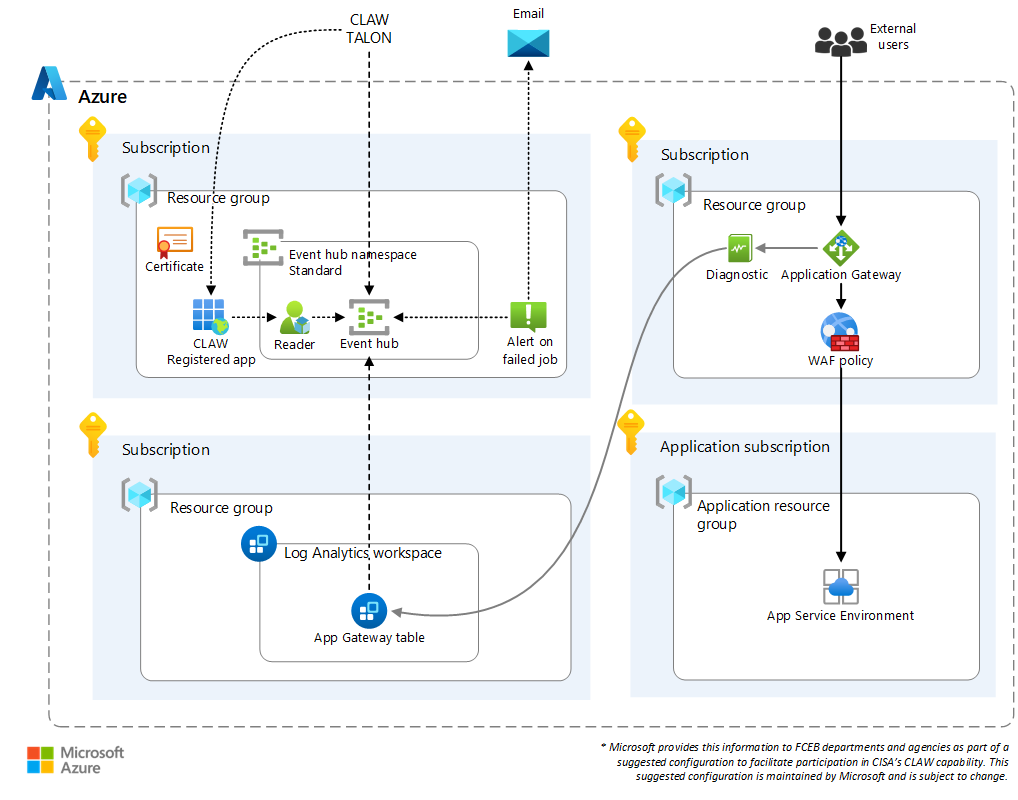
Deploy a solution that uses Application Gateway with WAF
The following solution uses Application Gateway with WAF to manage traffic entering your Azure application environment. The solution includes all resources for generating, collecting, and delivering logs to CLAW. It also includes an app service to track the types of telemetry collected by the firewall.
The solution includes:
- A virtual network that has separate subnets for the firewall and servers.
- A Log Analytics workspace.
- An Application Gateway v2 instance with WAF. The WAF is configured with bot and Microsoft managed policies.
- Application Gateway v2 diagnostic settings that send logs to the Log Analytics workspace.
- A registered application.
- An event hub.
- An alert rule that sends an email if a job fails.
For the sake of simplicity, all resources are deployed to a single subscription and virtual network. You can deploy the resources in any combination of resource groups or across multiple virtual networks.
Post-deployment tasks
After deployment, your environment performs the firewall capabilities and logging connections. To meet compliance with TIC 3.0 policies for network telemetry collection, you need to ensure that the logs make it to CISA CLAW. The post-deployment steps finish the tasks to enable compliance. To complete these steps, you need to coordinate with CISA because CISA needs to supply a certificate to associate with your service principal. For step-by-step details, see Post-deployment tasks.
You need to manually perform the following tasks after deployment. You can't complete them by using an ARM template.
- Obtain a public key certificate from CISA.
- Create a service principal (application registration).
- Add the public key certificate to the application registration.
- Assign the application the Azure Event Hubs Data Receiver role at the Event Hubs namespace scope.
- Activate the feed by sending the Azure tenant ID, application (client) ID, event hub namespace name, event hub name, and consumer group name to CISA.
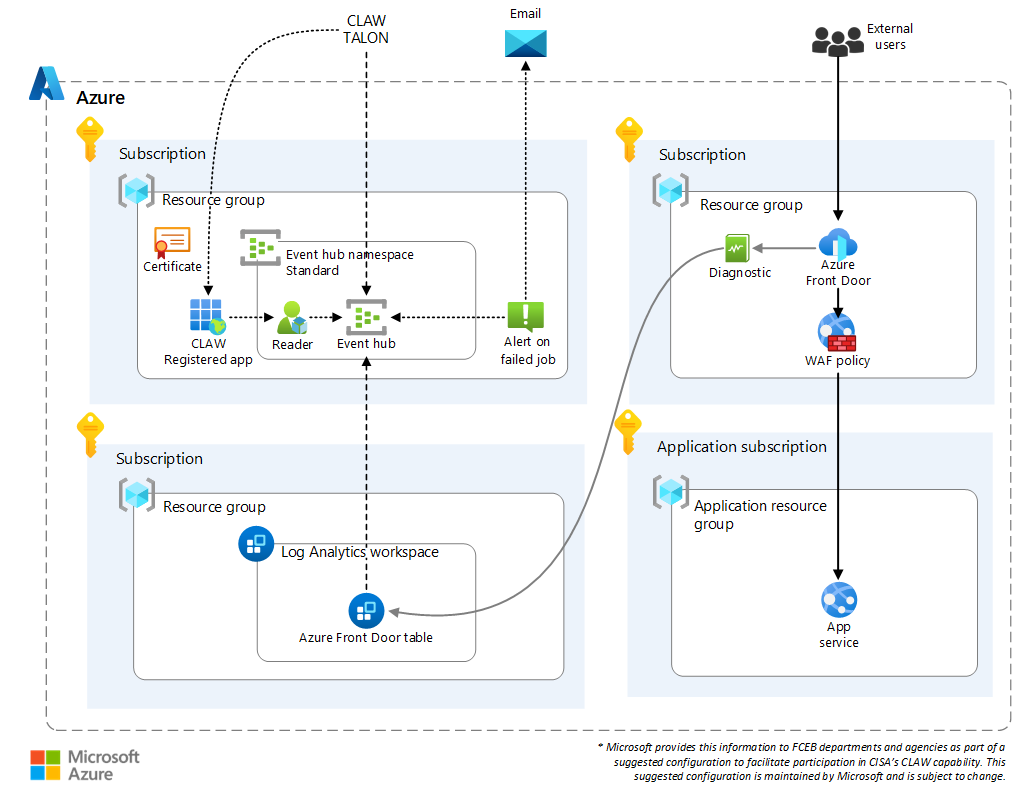
Deploy a solution that uses Azure Front Door with WAF
The following solution uses Azure Front Door with WAF to manage traffic entering your Azure application environment. The solution includes all resources for generating, collecting, and delivering logs to CLAW. It also includes an app service to track the types of telemetry collected by the firewall.
The solution includes:
- A virtual network that has separate subnets for the firewall and servers.
- A Log Analytics workspace.
- An Azure Front Door instance with WAF. The WAF is configured with bot and Microsoft managed policies.
- Azure Front Door diagnostic settings that send logs to the Log Analytics workspace.
- A registered application.
- An event hub.
- An alert rule that sends an email if a job fails.
For the sake of simplicity, all resources are deployed to a single subscription and virtual network. You can deploy the resources in any combination of resource groups or across multiple virtual networks.
Post-deployment tasks
After deployment, your environment performs the firewall capabilities and logging connections. To meet compliance with TIC 3.0 policies for network telemetry collection, you need to ensure that the logs make it to CISA CLAW. The post-deployment steps finish the tasks to enable compliance. To complete these steps, you need to coordinate with CISA because CISA needs to supply a certificate to associate with your service principal. For step-by-step details, see Post-deployment tasks.
You need to manually perform the following tasks after deployment. You can't complete them by using an ARM template.
- Obtain a public key certificate from CISA.
- Create a service principal (application registration).
- Add the public key certificate to the application registration.
- Assign the application the Azure Event Hubs Data Receiver role at the Event Hubs namespace scope.
- Activate the feed by sending the Azure tenant ID, application (client) ID, event hub namespace name, event hub name, and consumer group name to CISA.
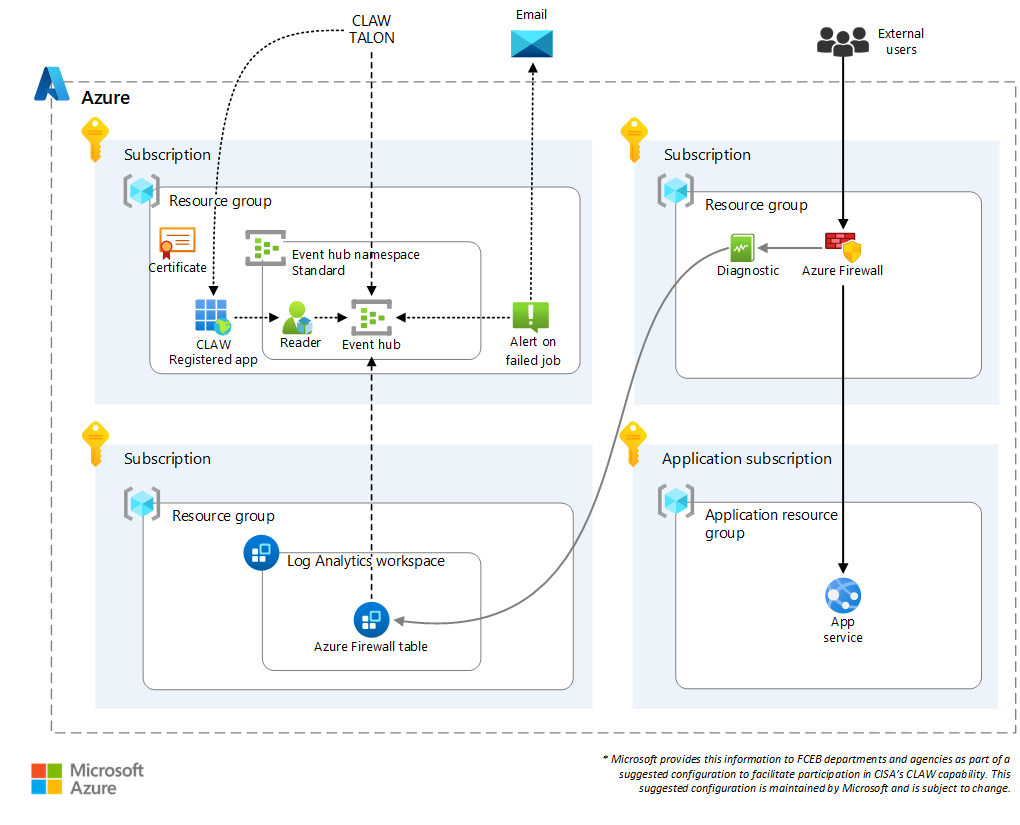
Third-party firewall (NVA) solution
Note
Deployment resources aren't provided for this solution. It's included only to provide guidance.
The following solution illustrates how you can use a third-party firewall to manage traffic entering your Azure application environment and implement TIC 3.0 compliance. Third-party firewalls require the use of a Syslog forwarder virtual machine. Its agents need to be registered with the Log Analytics workspace. The third-party firewall is configured to export its logs in Syslog format to the Syslog forwarder virtual machine. The agent is configured to send its logs to the Log Analytics workspace. After the logs are in the Log Analytics workspace, they're sent to Event Hubs and processed as they are in the other solutions described in this article.
Post-deployment tasks
After deployment, your environment performs the firewall capabilities and logging connections. To meet compliance with TIC 3.0 policies for network telemetry collection, you need to ensure that the logs make it to CISA CLAW. The post-deployment steps finish the tasks to enable compliance. To complete these steps, you need to coordinate with CISA because CISA needs to supply a certificate to associate with your service principal. For step-by-step details, see Post-deployment tasks.
You need to manually perform the following tasks after deployment. You can't complete them by using an ARM template.
- Obtain a public key certificate from CISA.
- Create a service principal (application registration).
- Add the public key certificate to the application registration.
- Assign the application the Azure Event Hubs Data Receiver role at the Event Hubs namespace scope.
- Activate the feed by sending the Azure tenant ID, application (client) ID, event hub namespace name, event hub name, and consumer group name to CISA.
Contributors
This article is maintained by Microsoft. It was originally written by the following contributors.
Principal author:
- Paul Lizer | Senior Cloud Solution Architect
Other contributor:
- Mick Alberts | Technical Writer
To see non-public LinkedIn profiles, sign in to LinkedIn.
Next steps
- TIC 3.0 core guidance documents
- National Cybersecurity Protection System (NCPS) documents
- EINSTEIN
- Managed Trusted Internet Protocol Services (MTIPS)
- Azure Trusted Internet Connection - Extended
- Federal App Innovation - TIC 3.0
- What is Azure Firewall?
- Azure Firewall documentation
- What is Azure Application Gateway?
- Azure Front Door
- Introduction to Azure WAF
- Overview of Log Analytics in Azure Monitor
- What is Azure Event Hubs?
- Overview of alerts in Azure
- Application and service principal objects in Microsoft Entra ID
- Use the portal to create a Microsoft Entra application and service principal that can access resources
- Register an application with the Microsoft identity platform
- Assign Azure roles using the Azure portal
- Create resource groups
- How to find your Microsoft Entra tenant ID
- Collect Syslog data sources with the Log Analytics agent
- Parse text data in Azure Monitor logs
- Introduction to flow logging for network security groups
- What are managed identities for Azure resources?
- Deploy and configure Azure Firewall using the Azure portal