Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Front Door is a globally distributed content delivery network (CDN) that provides lower latency and faster delivery of your web application and content. Moreover, Front Door allows for your content to be available with the highest levels of resiliency, and provides a wide range of features including an advanced application load balancer, traffic acceleration, and security.
Consider deploying Front Door in front of any publicly facing web application.
Well-architected solutions on Azure
The Azure Well-Architected Framework describes five pillars of architectural excellence. Azure Front Door helps you to address each of the five pillars by using its built-in features and capabilities.
Performance efficiency
Front Door provides several features to help to accelerate the performance of your application.
- Caching: Front Door provides a powerful content delivery network (CDN) to cache content at the network edge. Almost all web applications contain cacheable content. Static assets like images and JavaScript files are cacheable. Also, many APIs return responses that can be cached, even for a short duration. Caching helps to improve the performance of your application, and to reduce the load on your application servers.
- Compression: Many response types can be compressed, which can improve your application's response time.
- Global traffic acceleration: Front Door's global traffic acceleration capabilities help to improve the performance of dynamic web applications by routing requests through Microsoft's high-speed backbone network.
- TLS termination: Connections to Front Door terminate at the closest Front Door point of presence (PoP). TLS decryption is performed by the PoP. The biggest performance hit when doing TLS decryption is the initial handshake. To improve performance, the server doing the decryption caches TLS session IDs and manages TLS session tickets. If TLS connections are terminated at the Front Door PoP, all requests from the same client can use the cached values. If it's done on the origin servers, then each time the client's requests go to a different server the client must reauthenticate. The use of TLS tickets can help mitigate this issue, but they aren't supported by all clients and can be difficult to configure and manage.
Security
Front Door's security capabilities help to protect your application servers from several different types of threats.
- End-to-end TLS: Front Door supports end-to-end TLS encryption. Front Door TLS/SSL offload terminates the TLS connection, decrypts the traffic at the Azure Front Door, and re-encrypts the traffic before forwarding it to the backend.
- Managed TLS certificates: Front Door can issue and manage certificates, ensuring that your applications are protected by strong encryption and trust.
- Custom TLS certificates: If you need to bring your own TLS certificates, Front Door enables you to use a managed identity to access the key vault that contains the certificate.
- Web application firewall: Front Door's web application firewall (WAF) provides a range of security capabilities to your application. Managed rule sets scan incoming requests for suspicious content. Bot protection rules identify and respond to traffic from bots. Geo-filtering and rate limiting features protect your application servers from unexpected traffic.
- Protocol blocking: Front Door only accepts traffic on the HTTP and HTTPS protocols, and will only process valid requests with a known
Hostheader. Because of this behavior, your application is protected against many types of attacks across a range of protocols. - DDoS protection: Because of Front Door's architecture, it can also absorb large distributed denial of service (DDoS) attacks and prevent the traffic from reaching your application.
- Private Link origins: Private Link integration helps you to protect your backend applications, ensuring that traffic can only reach your application by passing through Front Door and its security protections.
When you have strict network security requirements, you can use Azure Front Door to manage inbound HTTP and HTTPS traffic to your application, and use Azure Firewall to control non-HTTP and egress traffic.
Reliability
By using Front Door, you can create resilient, highly available solutions.
- Load balancing and failover: Front Door is a global load balancer. Front Door monitors the health of your origin servers, and if an origin becomes unavailable, Front Door can route requests to an alternative origin. You can also use Front Door to spread traffic across your origins to reduce the load on any one origin server.
- Anycast routing: Front Door itself has a large number of PoPs, each of which can serve traffic for any request. Anycast routing steers traffic to the closest available Front Door PoP, and if a PoP is unavailable, clients are automatically routed to the next closest PoP.
- Caching: By using the Front Door cache, you reduce the load on your application servers. If your servers are unavailable, Front Door might be able to continue to serve cached responses until your application recovers.
Cost optimization
Front Door can help you to reduce the cost of running your Azure solution.
- Caching: By enabling caching, content is returned from global Front Door edge nodes. This approach reduces global bandwidth charges and improves performance.
- Compression: When Front Door compresses your responses, it can reduce the bandwidth charges for your solution.
- Spread traffic across origins: Use Front Door to reduce the need to scale your application servers, or overprovision the capacity of your servers for traffic spikes. Each Front Door PoP can return cached content if it's available, which reduces the load on your application servers. You can also spread traffic across multiple backend servers, reducing the load on each individual server.
- Shared profile: You can use a single Front Door profile for many different applications. When you configure multiple applications in Front Door, you share the cost across each application, and you can reduce the configuration you need to perform.
Operational excellence
Front Door can help to reduce the operational burden of running a modern internet application, and enable you to make some kinds of changes to your solution without modifying your applications.
- Managed TLS certificates: Front Door can issue and manage certificates. This feature means you don't need to manage certificate renewals, and you reduce the likelihood of an outage that's caused by using an invalid or expired TLS certificate.
- Wildcard TLS certificates: Front Door's support for wildcard domains, including DNS and TLS certificates, enables you to use multiple hostnames without reconfiguring Front Door for each subdomain.
- HTTP/2: Front Door can help you to modernize your legacy applications with HTTP/2 support without modifying your application servers.
- Rules engine: The Front Door rules engine enables you to change the internal architecture of your solution without affecting your clients.
- Infrastructure as code: You can also deploy and configure Front Door by using infrastructure as code (IaC) technologies including Bicep, Terraform, ARM templates, Azure PowerShell, and the Azure CLI.
Solution architecture
When you deploy a solution that uses Azure Front Door, you should consider how your traffic flows from your client to Front Door, and from Front Door to your origins.
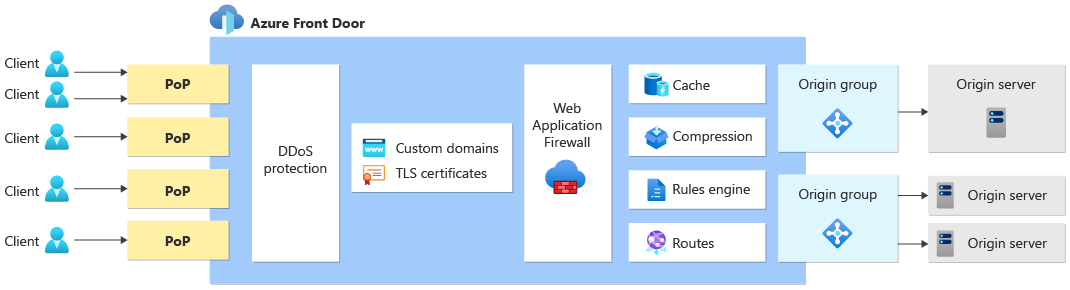
The following diagram illustrates a generic solution architecture using Front Door:
Client to Front Door
Traffic from the client first arrives at a Front Door PoP. Front Door has a large number of PoPs distributed worldwide, and Anycast routes the clients to their closest PoP.
When the request is received by Front Door's PoP, Front Door uses your custom domain name to serve the request. Front Door performs TLS offload by using either a Front Door-managed TLS certificate or a custom TLS certificate.
The PoP performs many functions based on the configuration you specify in your Front Door profile, including:
- Protecting your solution against many types of DDoS attacks.
- Scanning the request for known vulnerabilities, by using the Front Door WAF.
- Returning cached responses to improve performance, if they're stored at the Front Door PoP and are valid for the request.
- Compressing responses to improve performance.
- Returning HTTP redirect responses directly from Front Door.
- Selecting the best origin to receive the traffic based on the routing architecture.
- Modifying a request by using the rules engine.
After Front Door finishes processing the inbound request, it either responds directly to the client (for example, when it returns a cached result) or forwards the request to the origin.
Front Door to origin
Front Door can send traffic to your origin in two different ways: by using Private Link, and by using public IP addresses.
The premium SKU of Front Door supports sending traffic to some origin types by using Private Link. When you configure Private Link for your origin, traffic uses private IP addresses. This approach can be used to ensure that your origin only accepts traffic from your specific Front Door instance, and you can block traffic that came from the internet.
When the Front Door PoP sends requests to your origin by using a public IP address, it initiates a new TCP connection. Because of this behavior, your origin server sees the request originating from Front Door's IP address instead of the client.
Whichever approach you use to send traffic to your origin, it's usually a good practice to configure your origin to expect traffic from your Front Door profile, and to block traffic that doesn't flow through Front Door. For more information, see Secure traffic to Azure Front Door origins.
Response processing
Front Door's PoP also processes the outbound response. Response processing might include the following steps:
- Saving a response to the PoP's cache to accelerate later requests.
- Modifying a response header by using the rules engine.
Analytics and reporting
Because Front Door processes all incoming requests, it has visibility of all traffic flowing through your solution. You can use Front Door's reports, metrics and logs, to understand your traffic patterns.
Tip
When you use Front Door, some requests might not be processed by your origin server. For example, Front Door's WAF might block some requests, and it might return cached responses for other requests. Use Front Door's telemetry to understand your solution's traffic patterns.
Next steps
Learn how to create a Front Door profile.