Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Arc-enabled System Center Virtual Machine Manager (SCVMM) empowers System Center customers to connect their VMM environment to Azure and perform VM self-service operations from Azure portal. Azure Arc-enabled SCVMM extends the Azure control plane to SCVMM managed infrastructure, enabling the use of Azure security, governance, and management capabilities consistently across System Center managed estate and Azure.
Azure Arc-enabled SCVMM also allows you to manage your hybrid environment consistently and perform self-service VM operations through Azure portal. For Microsoft Azure Pack customers, this solution is intended as an alternative to perform VM self-service operations.
Azure Arc-enabled SCVMM allows you to:
- Perform various VM lifecycle operations such as start, stop, pause, and delete VMs on SCVMM managed VMs directly from Azure.
- Empower developers and application teams to self-serve VM operations on demand using Azure role-based access control (RBAC).
- Browse your VMM resources (VMs, templates, VM networks, and storage) in Azure, providing you with a single pane view for your infrastructure across both environments.
- Discover and onboard existing SCVMM managed VMs to Azure.
- Install the Azure Connected Machine agent at scale on SCVMM VMs to govern, protect, configure, and monitor them.
- Build automation and self-service pipelines using Python, Java, JavaScript, Go, and .NET SDKs; Terraform, ARM, and Bicep templates; Azure REST APIs, CLI, and PowerShell.
- Leverage Azure Arc benefits such as Windows Server management for VMs with Software Assurance licenses, and pay-as-you-go billing for Extended Security Updates for Windows Server and SQL Server VMs.
For updates on the capabilities and enhancements of Azure Arc, see the Tech Community blog for Azure Arc.
How does it work?
To Arc-enable an SCVMM management server, deploy Azure Arc resource bridge in the VMM environment. Azure Arc resource bridge is a virtual appliance that connects VMM management server to Azure. Azure Arc resource bridge enables you to represent the SCVMM resources (clouds, VMs, templates etc.) in Azure and do various operations on them.
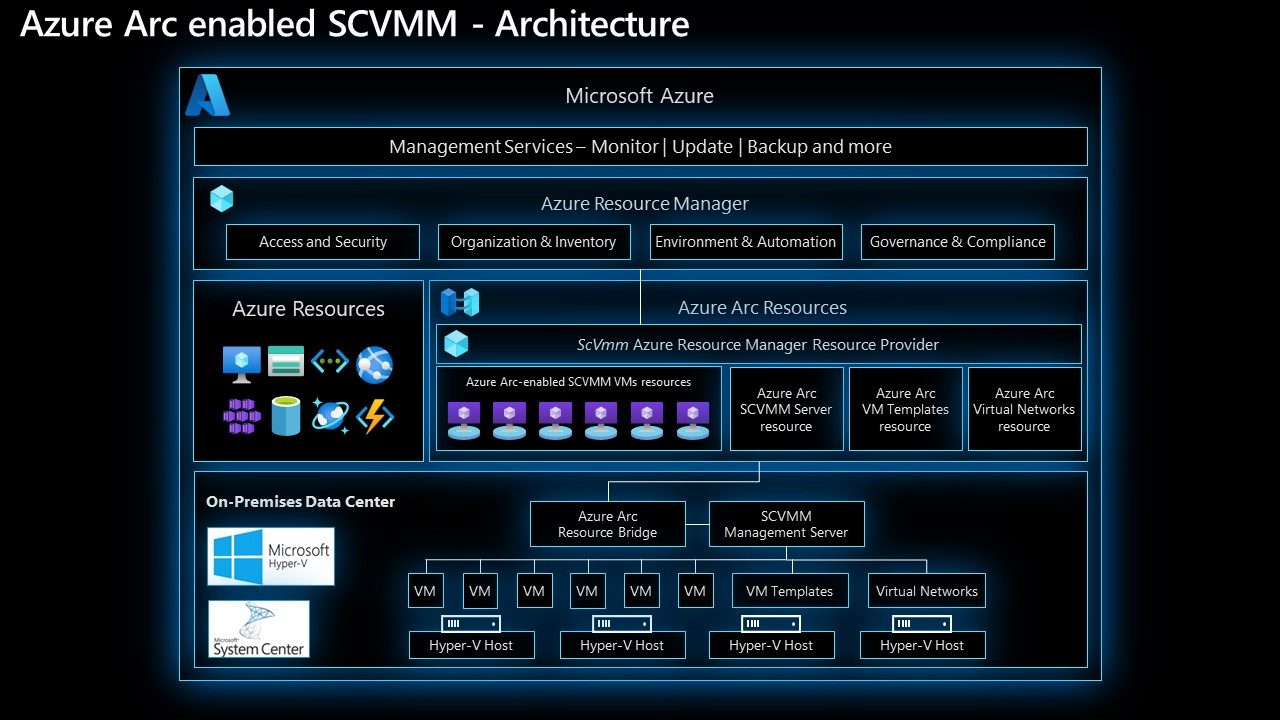
Architecture
The following image shows the architecture for the Azure Arc-enabled SCVMM:
To download architecture diagrams in high resolution, visit Jumpstart Gems.
How is Azure Arc-enabled SCVMM different from Azure Arc-enabled servers
- Azure Arc-enabled servers interact on the guest operating system level, with no awareness of the underlying infrastructure fabric and the virtualization platform that they're running on. Since Azure Arc-enabled servers also support bare-metal machines, there might, in fact, not even be a host hypervisor in some cases.
- Azure Arc-enabled SCVMM is a superset of Azure Arc-enabled servers that extends management capabilities beyond the guest operating system to the VM itself. This provides lifecycle management and CRUD (Create, Read, Update, and Delete) operations on an SCVMM VM. These lifecycle management capabilities are exposed in the Azure portal and look and feel just like a regular Azure VM. Azure Arc-enabled SCVMM also provides guest operating system management, in fact, it uses the same components as Azure Arc-enabled servers.
You have the flexibility to start with either option, and incorporate the other one later without any disruption. With both options, you'll enjoy the same consistent experience.
Note
For guidance on choosing the right Azure Arc service for your virtual machines, see Choose the right Azure Arc service for machines.
Supported scenarios
The following scenarios are supported in Azure Arc-enabled SCVMM:
SCVMM administrators can connect a VMM instance to Azure and browse the SCVMM virtual machine inventory in Azure.
Administrators can use the Azure portal to browse SCVMM inventory and register SCVMM cloud, virtual machines, VM networks, and VM templates into Azure.
Administrators can provide app teams/developers fine-grained permissions on those SCVMM resources through Azure RBAC.
App teams can use Azure interfaces (portal, CLI, PowerShell, SDKs, Terraform, Bicep, ARM templates, or REST API) to manage the lifecycle of on-premises VMs they use for deploying their applications (CRUD, Start/Stop/Restart).
Administrators can install Azure Connected Machine agent on SCVMM-managed VMs at-scale and can perform the following actions:
- Govern:
- Assign Azure machine configurations to audit settings inside the machine.
- Protect:
- Protect non-Azure servers with Microsoft Defender for Endpoint, included through Microsoft Defender for Cloud, for threat detection, for vulnerability management, and to proactively monitor for potential security threats. Microsoft Defender for Cloud presents the alerts and remediation suggestions from the threats detected.
- Use Microsoft Sentinel to collect security-related events and correlate them with other data sources.
- Configure:
- Use Azure Automation for frequent and time-consuming management tasks using PowerShell and Python runbooks. Assess configuration changes for installed software, Microsoft services, Windows registry and files, and Linux daemons using the Azure Monitor agent for change tracking and inventory.
- Use Azure Update Manager to manage operating system updates for Windows and Linux servers. Automate onboarding and configuration of a set of Azure services when you use Azure Automanage.
- Perform post-deployment configuration and automation tasks using supported Arc-enabled servers VM extensions for non-Azure Windows or Linux machine.
- Monitor:
- Monitor operating system performance and discover application components to monitor processes and dependencies with other resources using VM insights.
- Collect other log data, such as performance data and events, from the operating system or workloads running on the machine with the Azure Monitor Agent. This data is stored in a Log Analytics workspace.
Log data collected and stored in a Log Analytics workspace from the hybrid machine contains properties specific to the machine, such as a Resource ID, to support resource-context log access.
Watch this video to learn more about Azure monitoring, security, and update services across hybrid and multicloud environments.
- Govern:
Administrators can install the Azure Connected Machine agent at scale and leverage Azure Arc benefits such as Windows Server management for VMs with Software Assurance licenses, and pay-as-you-go billing for Extended Security Updates for Windows Server and SQL Server VMs.
Unsupported scenarios
Azure Arc-enabled SCVMM doesn't support:
- Azure-based management of VMware vCenter VMs managed by SCVMM. To onboard VMware VMs to Azure Arc, we recommend you to use Azure Arc-enabled VMware vSphere.
- Azure-based management of Azure Local VMs managed by SCVMM. To onboard Azure Local VMs to Azure Arc, we recommend you to use Azure Arc VM management capabilities of Azure Local.
Supported VMM versions
Azure Arc-enabled SCVMM works with VMM 2025, 2022, and 2019 versions and supports SCVMM management servers with a maximum of 15,000 VMs.
Supported regions
For the most up-to-date information about regional availability of Azure Arc-enabled SCVMM, see Product Availability by Region page.
Data Residency
Azure Arc-enabled SCVMM stores customer data. By default, customer data stays within the region the customer deploys the service instance in. For region with data residency requirements, customer data is always kept within the same region.
Next steps
- Plan your Azure Arc-enabled SCVMM deployment by reviewing the support matrix.
- Once ready, connect your SCVMM management server to Azure Arc using the onboarding script.
- Deliver operations Management disciplines using hybrid and multicloud tools in Cloud adoption Framework.
- Cloud Adoption Framework introduces Azure hybrid and multicloud products on Azure.