Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
There are two ways to authenticate to Azure SignalR Service resources: Microsoft Entra ID and access key. Microsoft Entra ID offers superior security and ease of use compared to the access key method.
With Microsoft Entra ID, you don't need to store tokens in your code, reducing the risk of potential security vulnerabilities. We highly recommend using Microsoft Entra ID for your Azure SignalR Service resources whenever possible.
Important
Disabling local authentication can have the following consequences:
- The current set of access keys is permanently deleted.
- Tokens signed with the current set of access keys become unavailable.
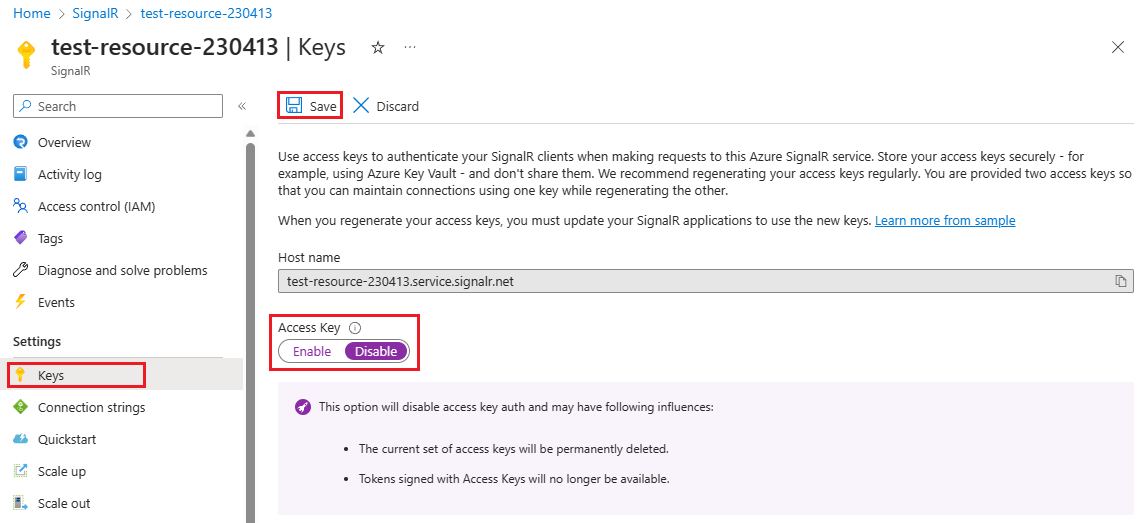
Use the Azure portal
In this section, you learn how to use the Azure portal to disable local authentication.
In the Azure portal, go to your Azure SignalR Service resource.
In the Settings section of the menu sidebar, select Keys.
For Access Key, select Disable.
Select the Save button.
Use an Azure Resource Manager template
You can disable local authentication by setting the disableLocalAuth property to true, as shown in the following Azure Resource Manager template:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"resource_name": {
"defaultValue": "test-for-disable-aad",
"type": "String"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.SignalRService/SignalR",
"apiVersion": "2022-08-01-preview",
"name": "[parameters('resource_name')]",
"location": "eastus",
"sku": {
"name": "Premium_P1",
"tier": "Premium",
"size": "P1",
"capacity": 1
},
"kind": "SignalR",
"properties": {
"tls": {
"clientCertEnabled": false
},
"features": [
{
"flag": "ServiceMode",
"value": "Default",
"properties": {}
},
{
"flag": "EnableConnectivityLogs",
"value": "True",
"properties": {}
}
],
"cors": {
"allowedOrigins": ["*"]
},
"serverless": {
"connectionTimeoutInSeconds": 30
},
"upstream": {},
"networkACLs": {
"defaultAction": "Deny",
"publicNetwork": {
"allow": [
"ServerConnection",
"ClientConnection",
"RESTAPI",
"Trace"
]
},
"privateEndpoints": []
},
"publicNetworkAccess": "Enabled",
"disableLocalAuth": true,
"disableAadAuth": false
}
}
]
}
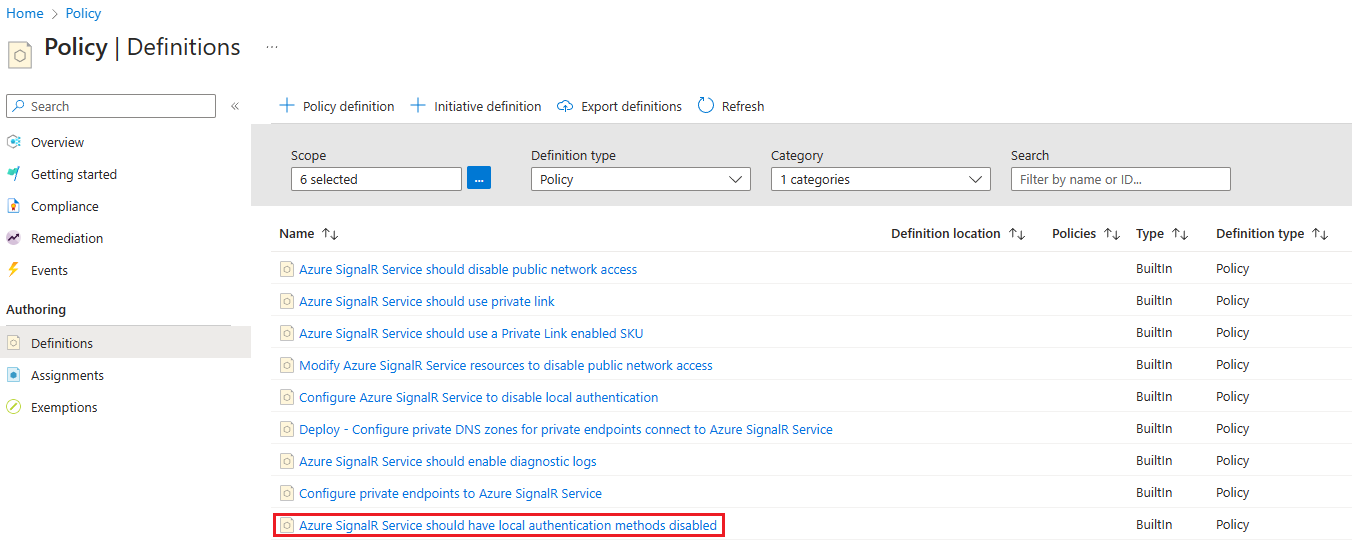
Use an Azure policy
To enforce disabling of local authentication for all Azure SignalR Service resources in an Azure subscription or a resource group, you can assign the following Azure policy: Azure SignalR Service should have local authentication methods disabled.
Next steps
See the following articles to learn about authentication methods: