Store Vulnerability Assessment scan results in a storage account accessible behind firewalls and VNets
Applies to:
Azure SQL Database
Azure SQL Managed Instance
Azure Synapse Analytics
If you're limiting access to your storage account in Azure for certain VNets or services, you'll need to enable the appropriate configuration so that Vulnerability Assessment (VA) scanning for SQL Databases or Azure SQL Managed Instances have access to that storage account.
Note
These settings are not required when using Express Configuration.
Prerequisites
The SQL Vulnerability Assessment service needs permission to the storage account to save baseline and scan results.
Use SQL Server managed identity:
- The SQL Server must have a managed identity.
- The storage account must have a role assignment for the SQL Managed Identity as Storage Blob Data Contributor.
- When you apply the settings, the VA fields storageContainerSasKey and storageAccountAccessKey must be empty (configuration using storage account key or storage SAS key is not valid for this scenario).
When you use the Azure portal to save SQL VA settings, Azure checks if you have permission to assign a new role assignment for the managed identity as Storage Blob Data Contributor on the storage. If permissions are assigned, Azure uses SQL Server managed identity, otherwise Azure uses the key method (which is not supported for this scenario).
Note
- User assigned managed identities are not supported for this scenario.
- If using Azure Storage lifecycle management policies, avoid moving files on the container used by VA to the archive access tier. Reading scan results or baseline configurations stored in archive access tier isn't supported.
Enable Azure SQL Database VA scanning access to the storage account
If you've configured your VA storage account to only be accessible by certain networks or services, you'll need to ensure that VA scans for your Azure SQL Database are able to store the scans on the storage account. You can use the existing storage account, or create a new storage account to store VA scan results for all databases on your logical SQL server.
Note
The vulnerability assessment service can't access storage accounts protected with firewalls or VNets if they require storage access keys.
Go to your Resource group that contains the storage account and access the Storage account pane. Under Settings, select Firewall and virtual networks.
Ensure that Allow trusted Microsoft services access to this storage account is checked.

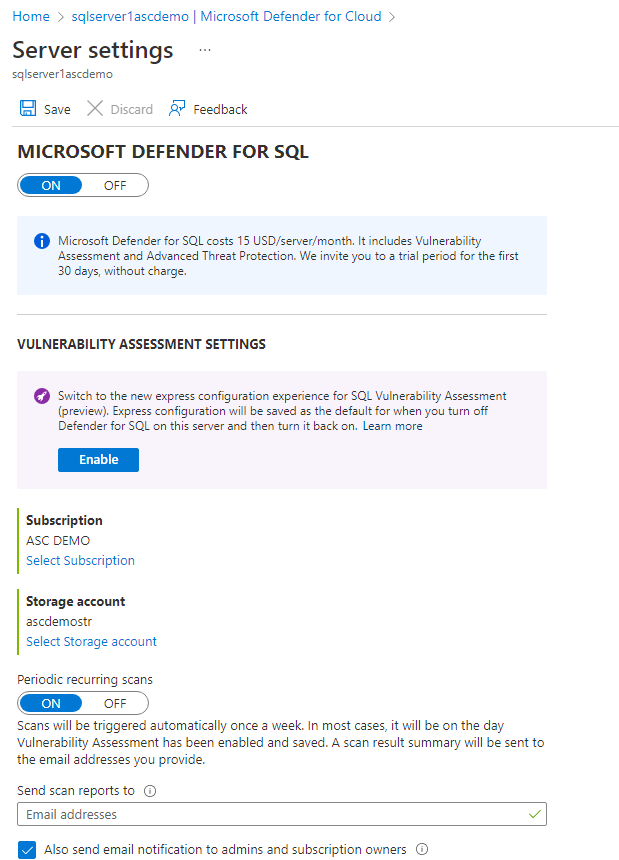
To find out which storage account is being used, do the following steps:
- Go to your SQL server pane in the Azure portal.
- Under Security, select Defender for Cloud.
- Select Configure.
Store VA scan results for Azure SQL Managed Instance in a storage account that can be accessed behind a firewall or VNet
Since Azure SQL Managed Instance isn't a trusted Microsoft Service and has a different VNet from the storage account, executing a VA scan will result in an error.
Note
It is highly recommended to make sure your Azure SQL Managed Instances are enrolled to the November 2022 feature wave which will allow much simpler configuration of SQL Vulnerability Assessment when the storage account is behind a firewall or VNET.
To support VA scans on Azure SQL Managed Instances that have the November 2022 feature wave installed, follow the below steps:
Under the Azure SQL Managed Instance's Overview page, note the value under Virtual network / subnet.
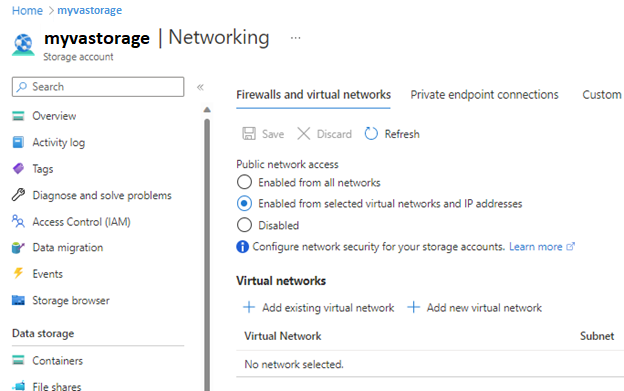
Head to the Networking page in the storage account where SQL VA is configured to store the scan results.
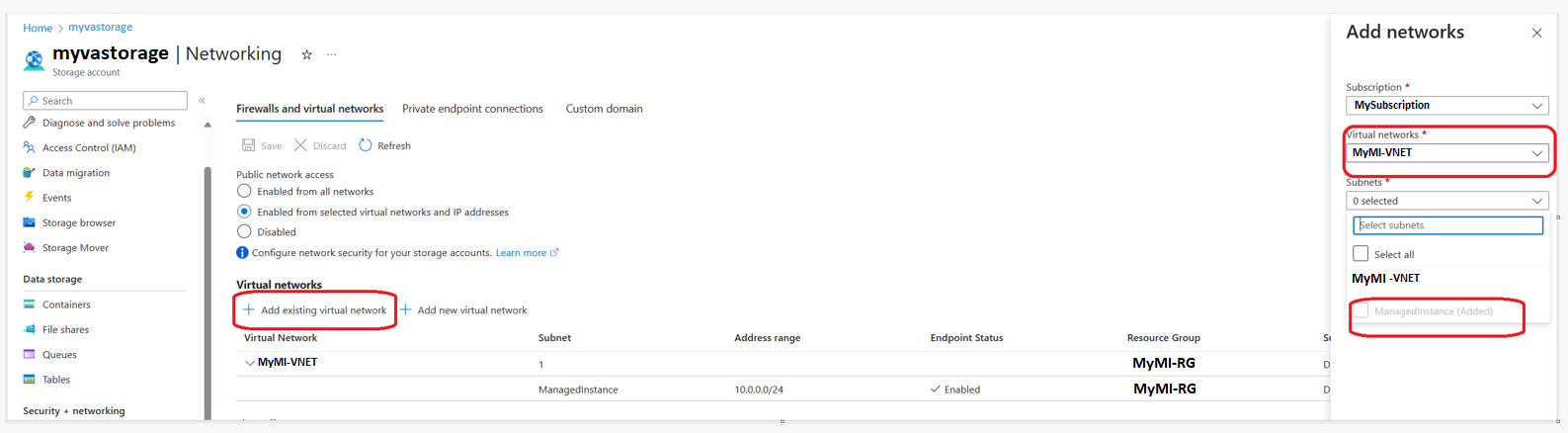
Under the Firewalls and virtual networks tab, under Public network access select Enabled from selected virtual networks and IP addresses.
Under the Virtual networks section, click Add existing virtual network and selected the VNET and subnet used by the managed instance that you've noted in the first step.
To support VA scans on Azure SQL Managed Instances that do not have the November 2022 feature wave installed, follow the below steps:
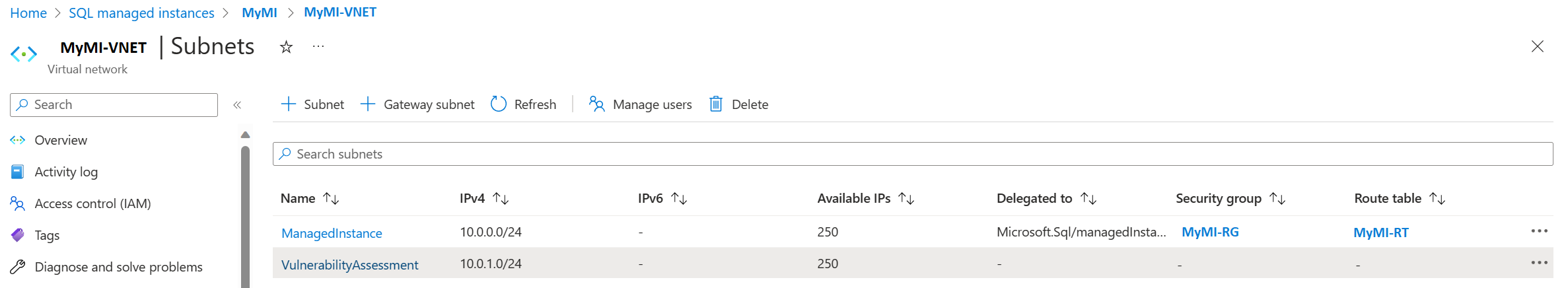
In the SQL managed instance pane, under the Overview heading, click the Virtual network/subnet link. This takes you to the Virtual network pane.
Under Settings, select Subnets. Click + Subnet in the new pane to add a subnet. For more information, see Manage subnets.
Traffic from the instance in the default managed instance subnet to Azure Resource Manager must be routed through the internet. Therefore, a route with the next hop being the internet and the destination tag being the appropriate UDR tag for the Azure Resource Manager address range must be assigned to the subnet where the managed instance is located. This route will be added automatically in new deployments, but needs to be added again if it was removed.
The new subnet should have the following configurations:
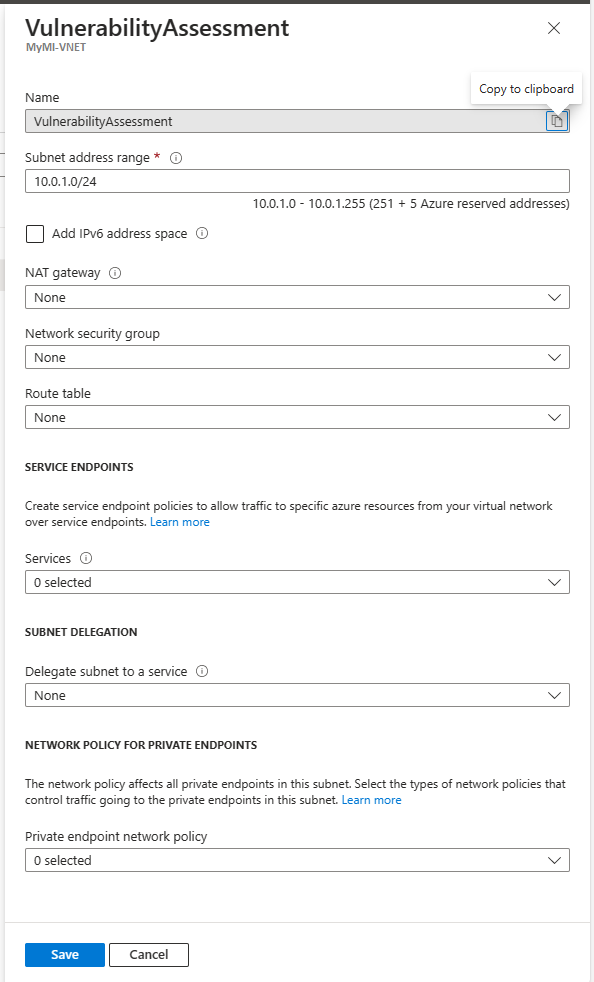
- NAT gateway: None
- Network security group: None
- Route table: None
- SERVICE ENDPOINTS - services: None selected
- SUBNET DELEGATION - Delegate subnet to a service: None
- NETWORK POLICY FOR PRIVATE ENDPOINTS - Private endpoint network policy: None selected
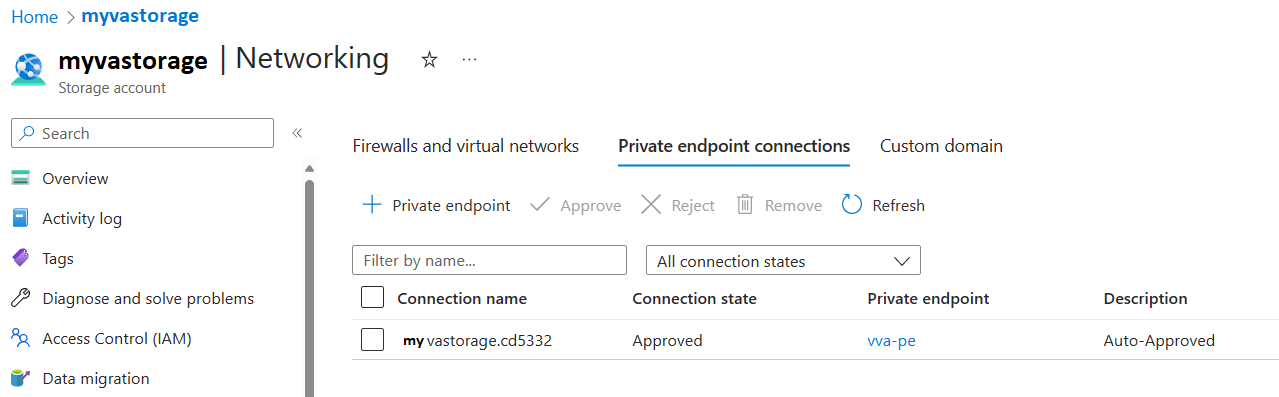
Head to the storage account where SQL VA is configured to store the scan results and click the Private endpoint connections tab, then click + Private endpoint
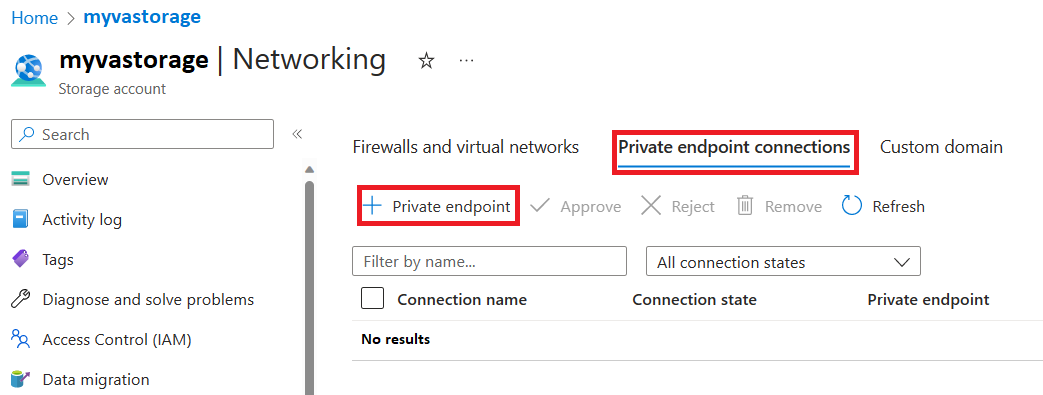
Choose the details for your private endpoint (it's suggested to put it in the same RG and the same region).
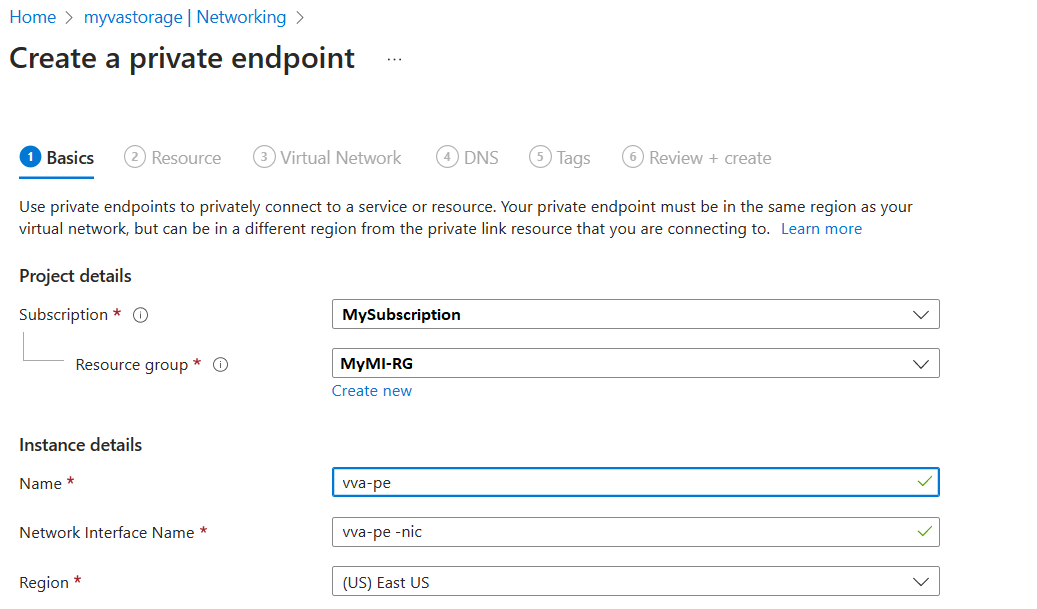
Choose blob for the Target sub-resource
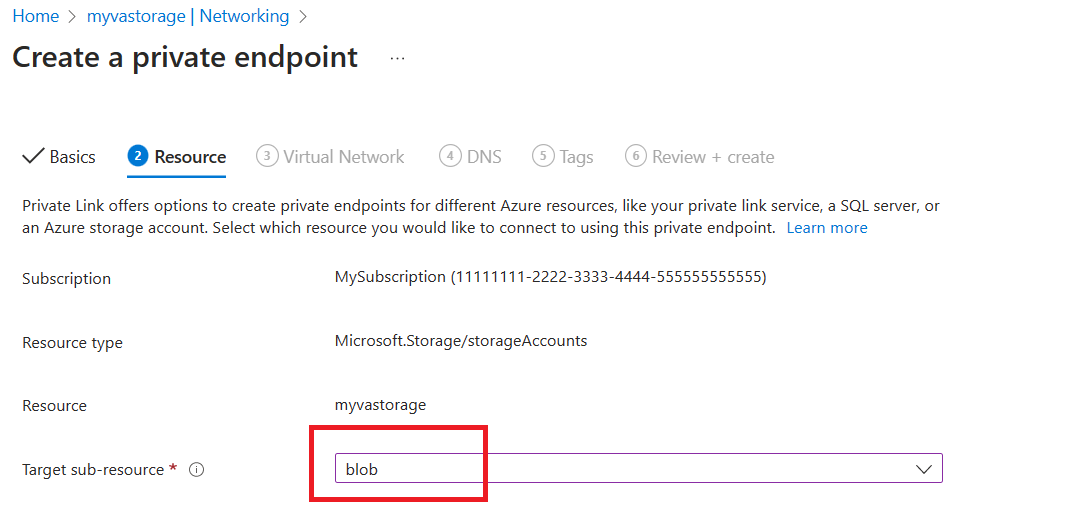
Select the virtual network of the SQL MI (from step 1) and choose the subnet you created (step 3):
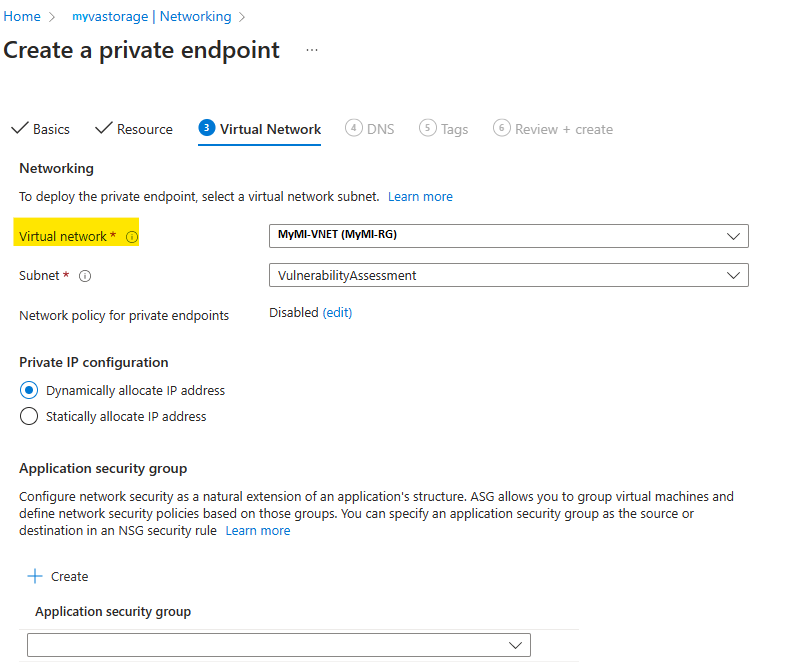
Select Integrate with private DNS zone (should be default) and choose the other default values
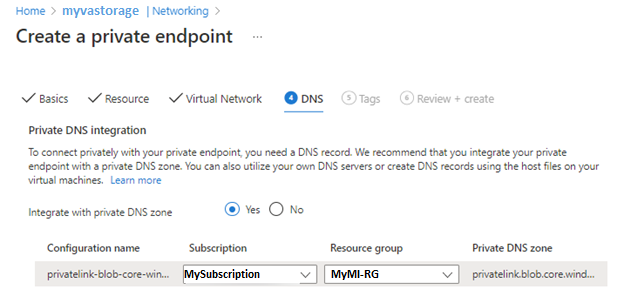
Continue to the Review + Create tab and click Create. Once the deployment is done you should see this in the Private endpoint connections tab under the Network section of the Storage account:
You should now be able to store your VA scans for Azure SQL Managed Instances in your storage account.
Troubleshoot vulnerability assessment scan-related issues
Troubleshoot common issues related to vulnerability assessment scans.
Failure to save vulnerability assessment settings
You might not be able to save changes to vulnerability assessment settings if your storage account doesn't meet some prerequisites or if you have insufficient permissions.
Storage account requirements
The storage account in which vulnerability assessment scan results are saved must meet the following requirements:
- Type: StorageV2 (General Purpose V2) or Storage (General Purpose V1)
- Performance: Standard (only)
- Region: The storage must be in the same region as the instance of Azure SQL Server.
If any of these requirements aren't met, saving changes to vulnerability assessment settings fails.
Permissions
The following permissions are required to save changes to vulnerability assessment settings:
- SQL Security Manager
- Storage Blob Data Reader
- Owner role on the storage account
Setting a new role assignment requires owner or user administrator access to the storage account and the following permissions:
- Storage Blob Data Owner
Storage account isn't visible for selection in vulnerability assessment settings
The storage account might not appear in the storage account picker for several reasons:
- The storage account you're looking for isn't in the selected subscription.
- The storage account you're looking for isn't in the same region as the instance of Azure SQL Server.
- You don't have Microsoft.Storage/storageAccounts/read permissions on the storage account.
Failure to open an email link for scan results or can't view scan results
You might not be able to open a link in a notification email about scan results, or to view scan results if you don't have the required permissions, or if you use a browser that doesn't support opening or displaying scan results.
Required permissions
The following permissions are required to open links in email notifications about scan results or to view scan results:
- SQL Security Manager
- Storage Blob Data Reader
Browser requirements
The Firefox browser doesn't support opening or displaying scan results view. We recommend that you use Microsoft Edge or Chrome to view vulnerability assessment scan results.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for