Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
Azure SQL Database
Azure Synapse Analytics
This article describes the logical server in Azure used by databases in Azure SQL Database and Azure Synapse Analytics. In the Azure portal, the logical server is named SQL server and is different to the SQL Server product.
Overview
In Azure SQL Database and Azure Synapse Analytics, a server is a logical construct that acts as a central administrative point for a collection of databases. At the logical server level, you can administer logins, firewall rules, auditing rules, threat detection policies, and failover groups. A logical server can be in a different region than its resource group. The logical server must exist before you can create a database in Azure SQL Database or a dedicated SQL pool in Azure Synapse Analytics. All databases managed by a single logical server are created within the same region as the logical server.
This logical server is distinct from a SQL Server instance that you may be familiar with in the on-premises world. Specifically, there are no guarantees regarding location of the databases or dedicated SQL pool in relation to the server that manages them. Azure SQL Database and Azure Synapse don't expose any instance-level access or features. In contrast, the instance databases in a managed instance are all physically co-located - in the same way that you are familiar with SQL Server in the on-premises or virtual machine world.
When you create a logical server, you provide a server login account and password that has administrative rights to the master database on that server and all databases created on that server. This initial account is a SQL login account. Azure SQL Database and Azure Synapse Analytics support both SQL authentication and Microsoft Entra authentication. For information about logins and authentication, see Managing Databases and Logins in Azure SQL Database. Windows Authentication is not supported.
A logical server in SQL Database and Azure Synapse Analytics:
- Is created within an Azure subscription, but can be moved with its contained resources to another subscription
- Is the parent resource for databases, elastic pools, and dedicated SQL pools
- Provides a namespace for databases, elastic pools, and dedicated SQL pools
- Is a logical container with strong lifetime semantics - delete a server and it deletes its databases, elastic pools, and SQL pools
- Participates in Azure role-based access control (Azure RBAC) - databases, elastic pools, and dedicated SQL pools within a server inherit access rights from the server
- Is a high-order element of the identity of databases, elastic pools, and dedicated SQL pools for Azure resource management purposes (see the URL scheme for databases and pools)
- Collocates resources in a region
- Provides a connection endpoint for database access (
<serverName>.database.windows.net) - Provides access to metadata regarding contained resources via DMVs by connecting to a
masterdatabase - Provides the scope for management policies that apply to its databases - logins, firewall, audit, threat detection, and such
- Is restricted by a quota within the parent subscription (six servers per subscription by default, for more information, refer to subscription limits)
- Provides the scope for database quota and DTU or vCore quota for the resources it contains (such as 45,000 DTU)
- Is the versioning scope for capabilities enabled on contained resources
- Server-level principal logins can manage all databases on a server.
- The
masterdatabase of a logical server contains logins similar to those in instances of SQL Server that are granted access to one or more databases on the server, and can be granted limited administrative rights. For more information, see logins. - Creating, altering, or dropping user objects such as tables, views, or stored procedures in the
masterdatabase on a logical server is not supported. - The default collation for all databases created on a server is
SQL_LATIN1_GENERAL_CP1_CI_AS, whereLATIN1_GENERALis English (United States),CP1is code page 1252,CIis case-insensitive, andASis accent-sensitive.
Note
Microsoft Entra ID was previously known as Azure Active Directory (Azure AD).
Manage servers, databases, and firewalls
You can manage logical servers, databases, dedicated SQL pools, and firewalls by using the Azure portal, Azure PowerShell, the Azure CLI, Transact-SQL (T-SQL) and REST API.
You can create the resource group for a logical server ahead of time or while creating the server itself. There are multiple methods for getting to a new SQL server form, either by creating a new SQL server or as part of creating a new database.
Create a blank server
To create a blank logical server (without a database, elastic pool, or dedicated SQL pool) using the Azure portal, navigate to a blank SQL server (logical SQL server) form.
Create a blank or sample database in Azure SQL Database
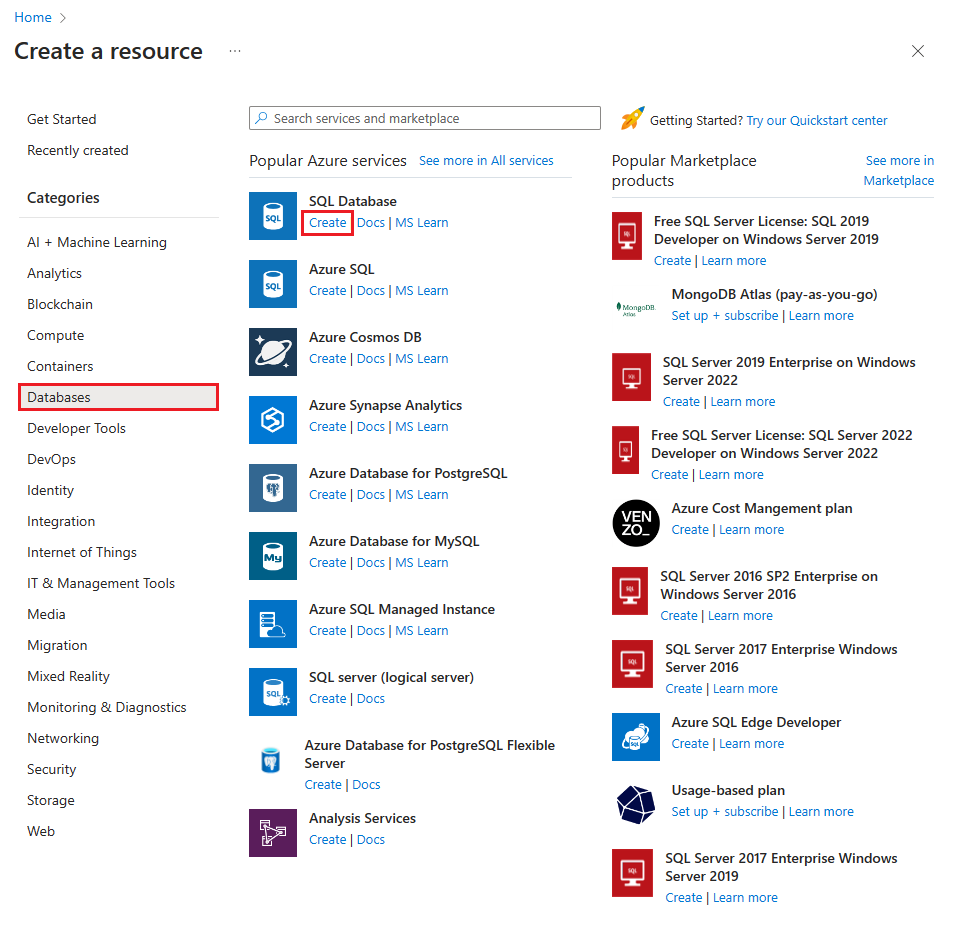
To create a database in SQL Database using the Azure portal, navigate to create a new SQL Database and provide the requested information. You can create the resource group and server ahead of time or while creating the database itself. You can create a blank database or create a sample database based on AdventureWorksLT.
Important
For information on selecting the pricing tier for your database, see DTU-based purchasing model and vCore-based purchasing model.
Manage existing server
To manage an existing server, navigate to the server using a number of methods - such as from specific database page, the SQL servers page, or the All resources page.
To manage an existing database, navigate to the SQL databases page and select the database you wish to manage.
For example, to configure a firewall rule, follow these steps:
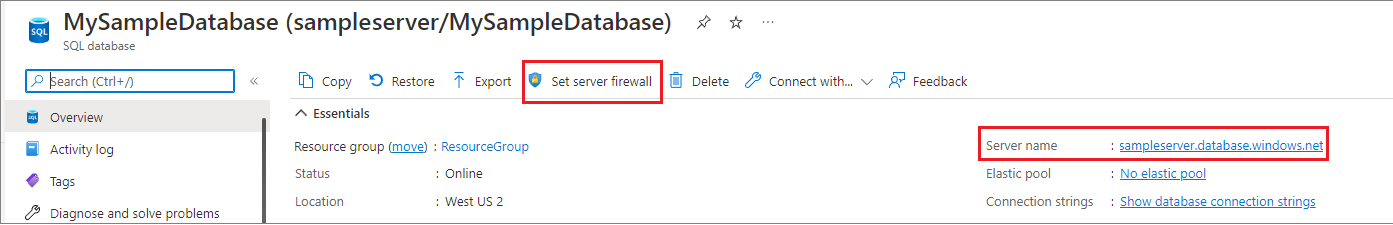
Navigate to your database resource in the Azure portal. Select Set server firewall on the toolbar.
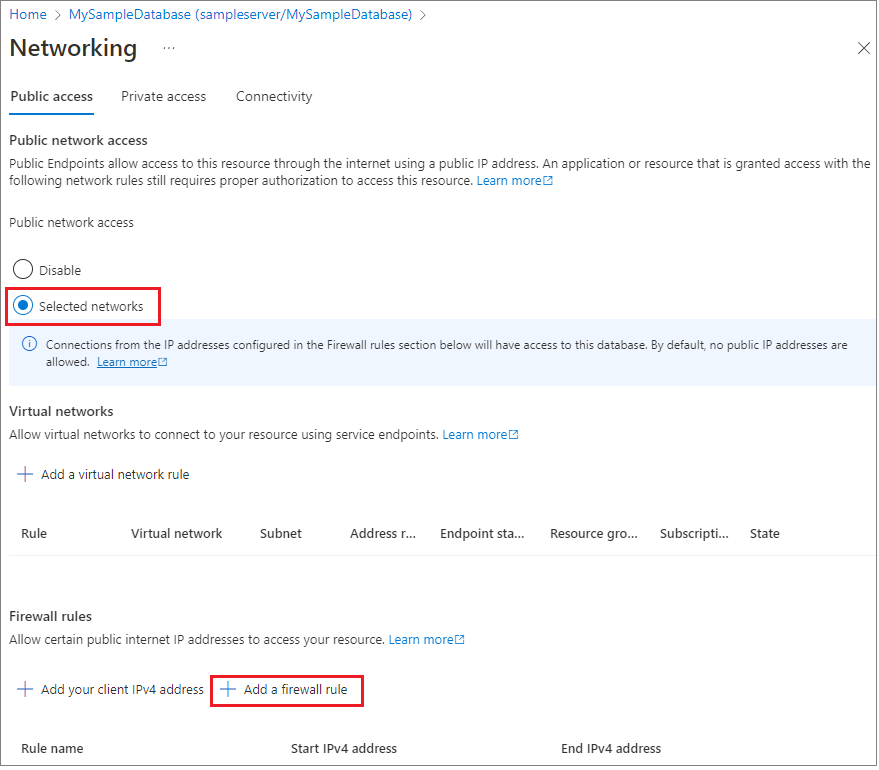
Set Public network access to Selected networks to reveal the virtual networks and firewall rules. When set to Disabled, virtual networks and firewall rule settings are hidden.
Choose Add a firewall rule to configure the firewall.
Important
To configure performance properties for a database, see DTU-based purchasing model and vCore-based purchasing model.
Tip
For an Azure portal quickstart, see Create a database in SQL Database in the Azure portal.
Next steps
- To learn about migrating a SQL Server database to Azure SQL Database, see Migrate to Azure SQL Database.
- For information about supported features, see Features.