Allow cross-tenant queries and commands
Principals from multiple tenants can run queries and commands in a single Azure Data Explorer cluster. In this article, you'll learn how to give cluster access to principals from another tenant.
To set the trustedExternalTenants on the cluster, use ARM Templates, AZ CLI, PowerShell, Azure Resource Explorer, or send an API request.
The following examples show how to define trusted tenants in the portal and with an API request.
Note
The principal who will run queries or commands must also have a relevant database role. See also role-based access control. Validation of correct roles takes place after validation of trusted external tenants.
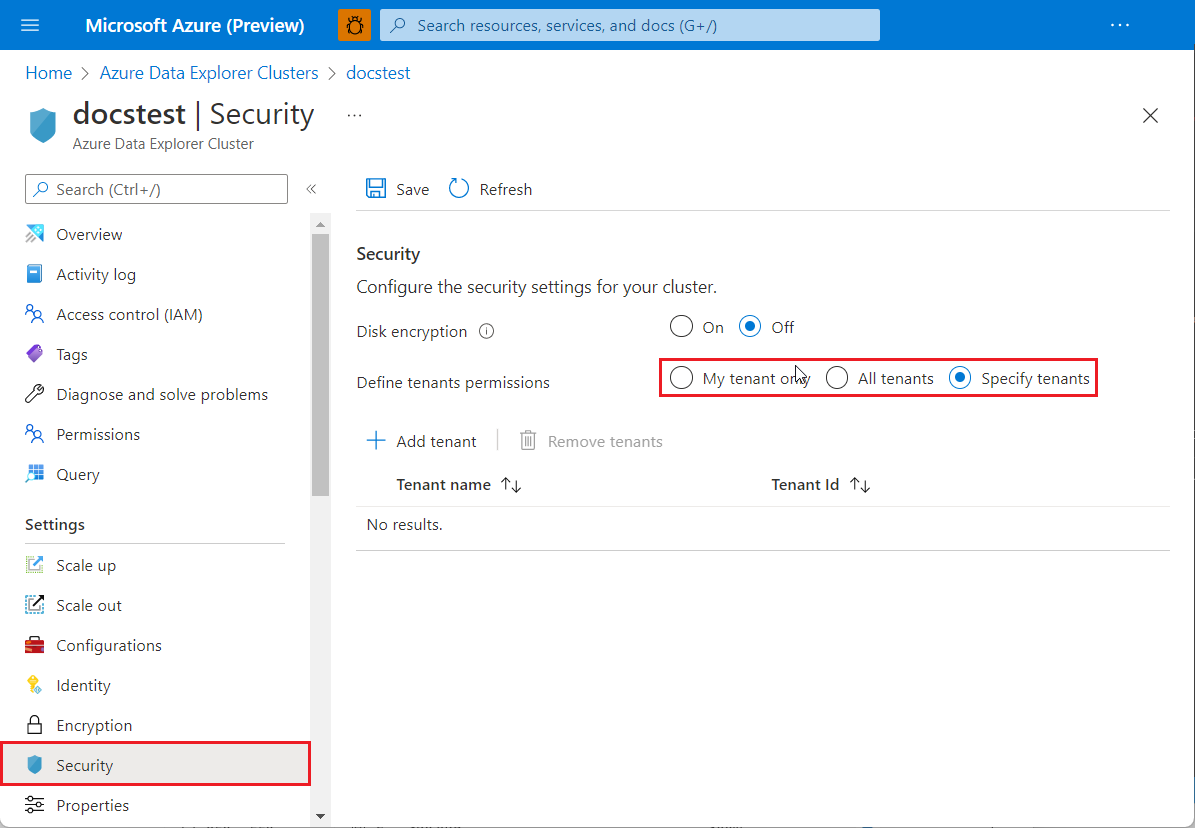
In the Azure portal, go to your Azure Data Explorer cluster page.
In the left-hand menu, under Settings, select Security.
Define the desired tenants permissions.
Add Principals
After updating the trustedExternalTenants property, you can give access to principals from the approved tenants. Use the Azure portal to give a principal cluster level permissions or database permissions. Alternatively, to give access to a database, table, function, or materialized view level, use management commands.
Limitations
The configuration of this feature applies solely to Microsoft Entra identities (Users, Applications, Groups) trying to connect to Azure Data Explorer. It has no impact on cross Microsoft Entra ingestion.