Investigate API findings, recommendations, and alerts
This article describes how to investigate API security findings, alerts, and security posture recommendations for APIs protected by Microsoft Defender for APIs.
Before you start
- Onboard your API resources to Defender for APIs.
- To explore security risks within your organization using Cloud Security Explorer, the Defender Cloud Security Posture Management (CSPM) plan must be enabled. Learn more.
View recommendations and runtime alerts
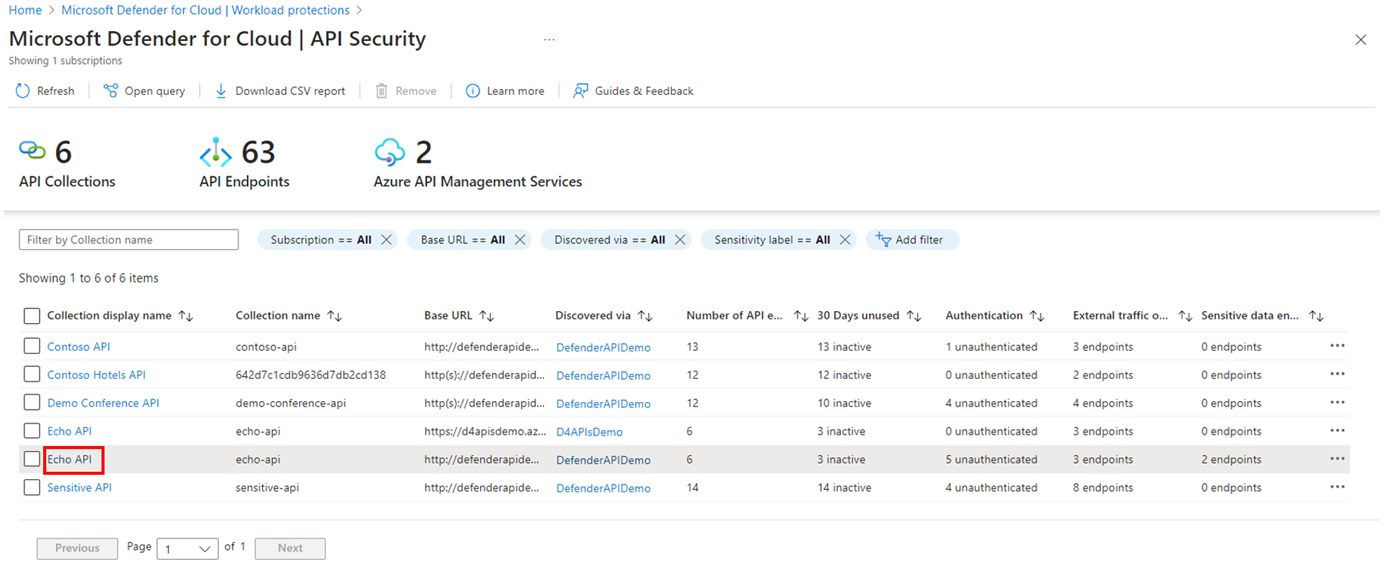
In the Defender for Cloud portal, select Workload protections.
Select API security (Preview).
In the API Security dashboard, select an API collection.
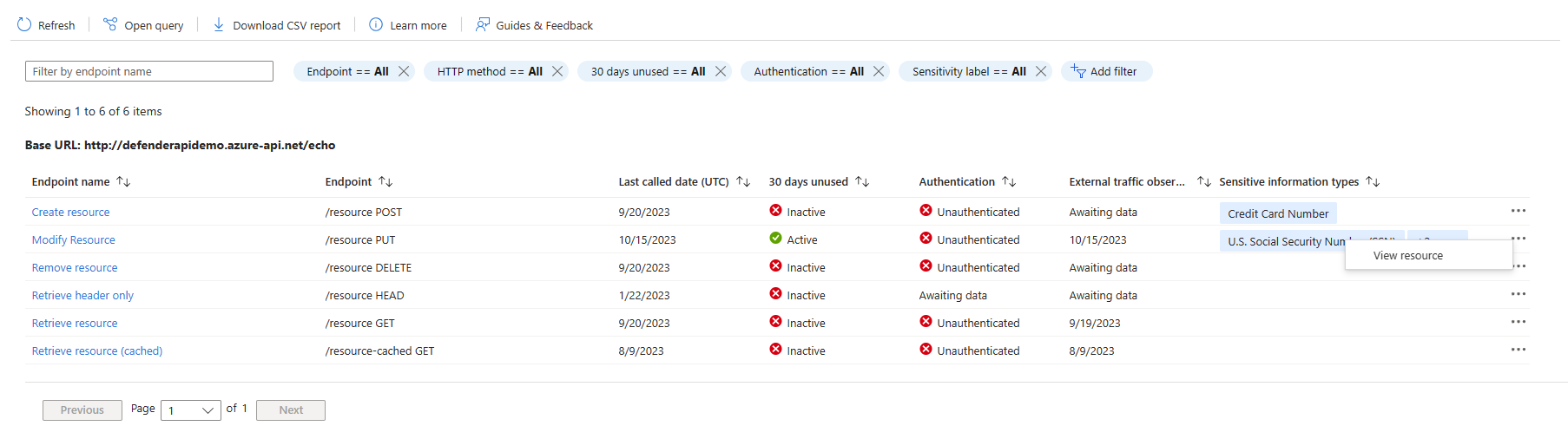
In the API collection page, to drill down into an API endpoint, select the ellipses (...) > View resource.
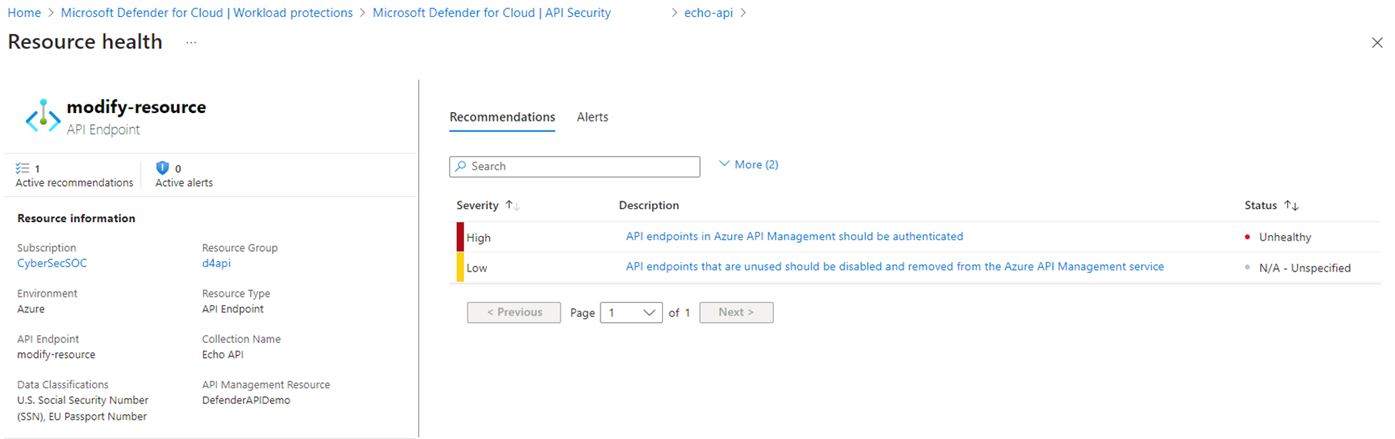
In the Resource health page, review the endpoint settings.
In the Recommendations tab, review recommendation details and status.
In the Alerts tab, review security alerts for the endpoint. Defender for Endpoint monitors API traffic to and from endpoints, to provide runtime protection against suspicious behavior and malicious attacks.
Remediate recommendations using Workflow Automation
You can remediate recommendations generated by Defender for APIs using workflow automations.
- In an eligible recommendation, select one or more unhealthy resources.
- Select Trigger logic app.
- Confirm the Selected subscription.
- Select a relevant logic app from the list.
- Select Trigger.
You can browse the Microsoft Defender for Cloud GitHub repository for available workflow automation.
Create sample security alerts
In Defender for Cloud you can use sample alerts to evaluate your Defender for Cloud plans, and validate your security configuration. Follow these instructions to set up sample alerts, and select the relevant APIs within your subscriptions.
Simulate alerts
To see the alert process in action, you can simulate an action that triggers a Defender for APIs alert. Follow the instructions in our Tech Community blog to do that.
Build queries in Cloud Security Explorer
In Defender CSPM, Cloud Security Graph collects data to provide a map of assets and connections across organization, to expose security risks, vulnerabilities, and possible lateral movement paths.
When the Defender CSPM plan is enabled together with Defender for APIs, you can use Cloud Security Explorer to identify, review and analyze API security risks across your organization.
- In the Defender for Cloud portal, select Cloud Security Explorer.
- In What would you like to search? select the APIs category.
- Review the search results so that you can review, prioritize, and fix any API issues.
- Alternatively, you can select one of the templated API queries to see high risk issues like Internet exposed API endpoints with sensitive data or APIs communicating over unencrypted protocols with unauthenticated API endpoints